
As most of you must be aware, Docker Hub has been compromised very recently and this attack has put almost 190K users at risk. According to me, this is one of the craziest supply chain attacks in the recent history. I say so, because it is not easy to make oneself foolproof against this attack. We might have to review multiple things before we feel safe, and still, we cannot provide the guarantee that we are secure enough.
Read more about this hack in Hacker News thread
Docker Hub Hacked - 190k accounts, GitHub tokens revoked, Builds disabled | Hacker News
For your benefit, I have come up with a list of checks which might help you to review your Docker hub, Github account, etc. Listed below are some of the checks that might help you while reviewing your Docker hub, Github accounts. All of these points are taken from my personal checklist, and they might or might not guarantee that you are completely secure.
Checklist
- Login to your Docker Hub and change your password in account settings page
- Check each of your repository image’s last build time, and see if you could identify any suspicious build. Additionally, check if any new tags were created for the images, or, if new images have been created or pushed manually
- Review the repository settings and check if any new collaborator has been added without your knowledge
- Review all external webhooks. Check if a suspicious webhook has been added to any of the repositories, or, if an existing webhook has been modified suspiciously
- Review your organization’s team members and ensure that any unknown user has not been added
- Ensure your automated builds from version control systems have been revoked and reconnected. Also, check for new connections or providers that might have been added suspiciously. Finally verify if the emails are mentioned correctly and that no new or modified webhooks have been added
- Navigate to your version control system provider and ensure you revoke the existing application integration and tokens. Also, review if any new GitHub apps have been added or if the existing ones have been removed
- Review yours and your organisation’s GitHub security activity to verify if any suspicious changes have been made over time
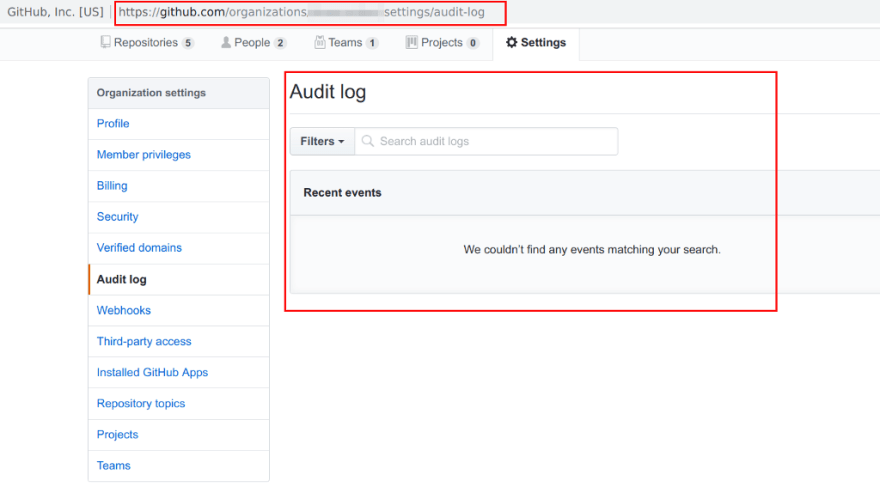
- Review your organisation’s and your personal account’s audit logs. Review any changes that have been made based on the privileges of the Docker Hub integration with GitHub
- Some additional checks which might be done includes, verifying your base images and existing images as it is possible that the corresponding owner accounts might have been compromised too. Use some open source image scanners like Clair, Vulners Audit, etc. These checks would apply even if you are not in Docker Hub and are using a private registry. This is because you might have ended up using some external base image like nginx, alpine, etc.
- Monitor, and monitor again, all the things (containers) that you are running. This is required because there are chances that some of the running containers might have been compromised already
These are some of the tips that I came up with and I would love to know what are some of the other thing that you might be thinking of and that could be helpful for our community. Please leave your comments and suggestions here and I will incorporate your suggestions into my post.
Contributors
Please feel free to provide any feedback, suggestions or improvements. If you liked this article, click the 👏 button and share this post so that other people could also benefit from this post.










Top comments (0)