- What are Bugs?
A software bug is an error in a computer program that causes it to produce unexpected results or to behave in a disruptive fashion.
Albeit a bug can be a very innocent flaw, a careless mistake the impact it can have can still be exponentially larger than an exploit due to a big logical error in a code base.
eg. a small rounding error in the calculation of an orbit of a satellite can cause major financial damages with many other implications like space pollution.
Hence, every developer should be aware of basic cybersecurity practices!
- How to reduce the number of bugs in your code?
Bringing a structure to your project can be immensely helpful, This structure can be brought by organizing your code but more importantly in your project and amongst your team.
To achieve this we can use the SDLC Pipeline (Software Development Lifecycle) -
1) Plan
Build a basic plan about your project, so that all features of your project are covered and there are no misunderstanding among the different teams or people working on the project.
Some things you can do that will make this phase a cakewalk are to make use of tools like Lucidchart to make a rough flow of your application. You can also include advice from your client at this stage of development!
Tools like Jira can be used to delegate work and keep on top of things!
2) Analyze
After you have a basic flow of your application and various inputs from your team and the client, you will have a very good understanding of what you have to exactly establish in the project. This is the correct time to figure out a tech stack and the intricacies of the project.
3) Design
During this phase of the project you should start by making the wireframe for your application with the goal of having a prototype of the application including UI/UX, authflow etc.
For this tools like Figma can be a lifesaver!
4) Build
This is the part where the major chunk of the work is done and the foundation for the project is laid out, it is therefore essential for you to write elegant code so that it is easy to debug and maintain the code later.
You can use developer tools like eslint, husky etc. for javascript/typescript based projects but such tools can be found for almost any architecture, language or framework that exists.
5) Testing
This is a very important step concerning the cybersecurity aspect of the application. Testing for an application can be done using multiple testing frameworks like Mocha for Javascript etc. and using multiple testing paradigms like unit testing and many more!
A good resource to read about different testing paradigms can be found here.
Also taking inputs from customers/client can also be profoundly helpful, this can be done through beta testing programs.
6) Deployment
Although it might not seem like it but how an application is deployed can have radical impacts on the security of an application. Aspects like it being sandboxed in a container or it having an SSL/TLS certificate or it having a load balancer can make or break your application when it matters the most. So make sure to deploy your application securely and reliably!
Beware this is the stage where Project Secrets are leaked the most!
7) Maintain
Once the project is launched into the public domain, regular maintenance is essential to say the least.
Keeping an eye on how the users are interacting with your application by making use loggers like Winston is a must.
Use of tools like Trivy and Dependabot Alerts can be used in combination with Automation Scripts and Version Control to avoid influx of vulnerabilities in peer dependencies of the application.
Offering Bug Bounties can also help avoiding disasters as it gives incentive to people who find vulnerability to report it to you rather than harming the infrastructure of your project.
However the above might seem trivial and not closely related to Cybersecurity, believe me it would lead to you avoiding having silly bugs in your code in the first place and make your life way easier in the future.
- Finding Bugs in applications
1) A very common way for testing is to use automated testing tools like BeVigil, a mobile phone app vulnerability finding tool! Such tools can help you to find Secret key leaks and much more with a click of a button. Without much effort you can get an insight into the working and the probable bugs that might exist.
2) Ownership of code decides what kind of environment you can test the code in.
- WhiteBox - In a whitebox environment, you have access to the entire codebase and a clear understanding of how the application logic works. Generally, it is easier to find bugs in such an environment.
- BlackBox - In a blackbox environment you are only faced with the application that the end user faces and are not aware about the inner working of the application at all
- GreyBox - In a grey box you have partial or a vague idea about the inner workings of the app.
3) From my experience of participating in multiple CTFs (Capture the Flag) I would say that to find a bug you need to be beware of everything in the code, any small innocent looking piece of code can cause you the biggest of problems. Also, as you develop more applications and widen your knowledge it will be easier for you to find bugs by guessing what another person might've used as an obvious choice to develop their program. Always trust your inkling!
I would like to illustrate a small example of a very common kind of bug here (SQL Injection) -
Many applications make use of structured databases for the operation of an authentication systems, search fields etc. A vulnerability called SQL Injection can quite commonly be found in such applications
To follow along visit this link. We gonna find our first bug today!
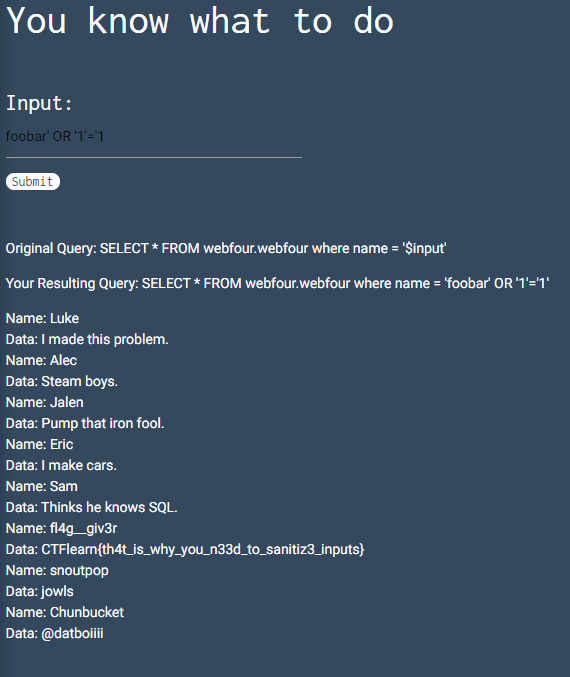
When you visit the link you should be greeted with something like this -
Since we are beginners we got some hints going for us! 🤩
From the looks of it, the app behaves like a searching program You give an input and a resulting output is produced on the basis of input.
If we see our hint it says -
SELECT * FROM webfour.webfour where name = '$input'
Even people who doesn't know SQL can tag along, just read the code as plain english.
So it means SELECT * (* means all) from webfour.webfour (Database table) where name = $input
So whatever we write in input field is written in place of $input
so if we write something along the lines of
foobar' OR '1'='1
the resultant query becomes
SELECT * FROM webfour.webfour where name = 'foobar' OR '1'='1'
So we are basically saying Select all from Database where a condition is always true.
And hence we obtain all entries of their database
This my friends is called a Database Leak and you have done it!!
- Now that we have found a bug we'll learn how to report it
DOs
- Use simple and clear language to explain the bug
- Mention privilege required to observe the bug
- Explain the way to reproduce the bugs with the request and response flows
- Describe the impact of the bug
- Attach evidence (screenshots, videos etc.)
- Be Nice and supportive
- Link similar bug reports/issues if there exists any
- List the environment in which you encountered the bug eg. the operating system you were using etc.
DON'Ts
- Do Not Not report a bug! If you find a bug make sure to report it. It could be beneficial for you the owner of the affected application and to the public in general.
- Have a very Crisp and Apt title for your report
- Use channels like Jira instead of emails/tweets
When you are writing a report it is beneficial for you to know how your report will reach to a developer through the triage process.
This can help you write better reports and earn the Bug Bounty you deserve. 🤠
A sample bug report would look something like this -
Bug Name: Application crashes upon clicking the SAVE button while creating a new user.
Area Path: USERS menu -> New Users
Build Number: Version Number 5.0.1
Severity: HIGH (High/Medium/Low) or 1
Priority: HIGH (High/Medium/Low) or 1
Assigned to: Developer-X
Reported By: Your Name
Reported On: Date
Reason: Defect
Status: New/Open/Active (Depends on the Tool you are using)
Environment: Windows 2003/SQL Server 2005
Description: Application crashes upon clicking the SAVE button while creating a new the user, hence unable to create a new user in the application.
Steps to Reproduce:
1) Login into the Application.
2) Navigate to the Users Menu -> New User
3) Filled out all the user information fields.
4) Clicked on the ‘Save’ button.
5) Seen an error page “ORA1090 Exception: Insert values Error…”
6) See the attached logs for more information (Attach more logs related to the bug if any)
7) Also see the attached screenshot of the error page.
Expected Result: On clicking the SAVE button, you should be prompted to a successful message “New User has been created successfully”.
(Attach ‘application crash’ screenshot. IF any)
I know the post might've been a little long but I hope you gained some insight into the cybersecurity world ✌.
Resources -
The following workshop which was conducted by CloudSEK and CSI-VIT -





Top comments (0)