Introduction
The internet is a digital universe that shares a lot in common with a maze. It’s so easy to lose our way and tumble into a rabbit hole that feels like an abyss. From pop-up ads to other intrusive forms of advertising that redirect us to other platforms, netizens have to contend with a lot of assault to surf the web.
Notable among the many boobytraps on the internet is one called typosquatting. It is a situation where malignant actors and cutthroat marketers register domain names that are somewhat similar to the domain names of organizations and popular entities with the hope of ensnaring unsuspecting netizens who click or mistype the URL of their intended website.
Many times, typosquatting attacks can be used to redirect to other platforms (a competitor’s website, betting, ads, or pornographic platforms). However, there are times when typosquatting can be used for utterly malignant activities, one of which is automatically installing dangerous software on your device. This can happen by simply visiting these platforms; a strategy termed drive-by download.
Typosquatting is a cyber-attack strategy that is used in every sphere of human interaction. While the business use is more common, there are famous cases where it has been utilized in politics to defame other political candidates and redirect potential political donors to the typosquatter’s donor. This was famously done in the 2020 US presidential election.
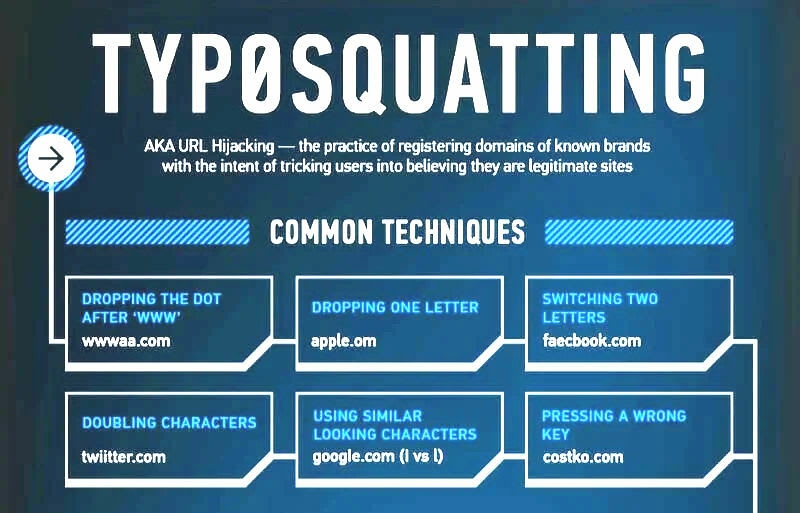
Common Typosquatting Attack Strategies
Typosquatting is built on the Achilles heel of the human mind that makes us likely to generalize words to infer their meaning quickly, preserve brain power, and boost efficiency. A lot of research has gone into trying to understand why humans are prone to typographical errors. Hence, it’s safe to say typosquatting attacks will continue to have a disconcerting success rate.
Common methods of typosquatting are:
Omission: This is when a domain name similar to a popular domain name target is registered, albeit with one or more letters missing. One example is registering a domain name like “Gogle.com” in a bid to ensnare users who subconsciously assumed the URL to be “Google.com”.
Addition: This is when an extra letter(s) is added when registering a domain name that looks like the target domain name of the typosquatting attack. One example is registering a domain name like “G0oogle.com” because it looks like “Google.com”.
Transposition: This is when a domain name intended to look like the target domain name is registered with the positions of the letters of the URL swapped around. One example is registering a domain name like “Googel.com” because it looks like “Google.com”.
Substitution: This is when a domain name has substituted characters to confuse unsuspecting netizens that they’re the same thing. For example, one can use “G00gle.com” to imitate “Google.com. Hint: zeroes have been used in the first one. It may or may not be apparent, depending on the font you’re using.
All of the above tricks of typosquatting are a means to an end. Typosquatting is typically the pipeline for executing unethical endeavors like:
- Impersonating financial organizations to illegally obtain the financial details of victims for the purpose of theft or money laundering.
- E-commerce fraud, which can occur by getting unsuspecting victims to pay for products that don’t get delivered.
- Hate pages aimed at demarketing the product or services of a business and defaming public figures.
- Hacking unsuspecting users by facilitating a drive-by download of malware or ransomware.
- Intrusive advertising, which is aimed at bombarding victims with adverts and redirecting them to an advertising page. Redirecting victims to betting or pornographic platforms.
Reducing Risk Exposure To Typosquatting Attacks
Due to the ease with which typosquatting attacks can be executed, it may appear like all hope is lost. However, there are cybersecurity tips that can help end-users, business owners, and software engineers avoid these boobytraps. It is worth noting that there is a burden on software engineers and DevOps engineers to reduce the likelihood of success of typosquatting attacks.
- Use browsers like Google Chrome that have policies that help ensure netizens can safely surf the internet.
- DevOps engineers need to purchase domain names that are similar to the domain name of their client to redirect traffic from those domain names to the client’s main domain name and to forestall typosquatting attacks. For example, “www.google.co” redirects to “www.google.com” (a smart move by the Google team).
- Netizens need to avoid clicking on links without reading through them carefully.
- Pin your favorite websites to your browser homepage (Google Chrome, Opera Mini, and other browsers do this automatically).
- Leveraging development tools: Software engineers typically leverage packages and libraries to build enterprise software solutions. Unfortunately, this can sometimes expose the developer and software solution to unintended typosquatting attacks.
Because a lot of packages and libraries consumed have names that sometimes defy normal language conventions, developers are less likely to carefully scrutinize resources before using them. This risk can have damaging consequences if things go wrong. As a result, many teams are beginning to rely on software solutions that help minimize this risk.
Tools like WS Diffend (a free tool for Ruby applications) help protect development teams and their solutions from falling prey to cyber threats that arise as a result of digital handshakes with third-party (and sometimes open source dependencies). As a result of the number of dependencies that developers use, tools like WS Diffend are a must.
WS Diffend is particularly notable because it scans for risks in Ruby applications (with a Javascript version nearing release) and offers robust, end-to-end cybersecurity that guards against typosquatting attacks, accidental injections, botnet code injections, viruses, package tampering, Ruby CVEs, dependency confusion, etc.
Conclusion
Typosquatting is one of those obvious threats that are still easy to fall for. It’s surprising how the simplest tricks work so well. We are all busy professionals who make thousands of decisions daily. As such, it’s common to make split-second decisions or skip out on reading things clearly before clicking or visiting websites.
There is an explicit burden placed on software engineers to help reduce the success rate of typosquatting by collaborating with cybersecurity experts and leveraging tools like WS Diffend in foolproofing software solutions.





Top comments (0)