When starting in the world of cybersecurity/hacking, we always want to run and hack anything but it's important to know the basics.
In this post we will review some basic topics as a starting point.
The reason why you lock your house when you go out so no bad guy comes inside and steal your belongings is similar to why companies are so serious about information security, Spoiler alert: no one wants their personal belongings get stolen.
What is Information Security?
- Information security means securing or protecting sensitive and important information as well as the systems that store this information from any unauthorized handling.
Information security consists of various important elements, we will first start with the CIA triad and later with the rest of elements.
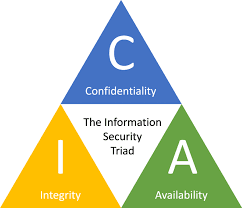
What is the CIA triad?
- The CIA triad consists of three important elements:
1. Confidentiality(C)
2. Integrity(I)
3. Availability(A)
Now, what do they mean?
- Confidentiality: Only those with authorized access will be able to access the information.
Example: Encryption - Integrity: The assurance that the information/data haven't suffered any unauthorized modification.
Example: Hashing - Availability: Data always been accessible for authorized users when required.
Example: Backups, clustered machines - Non-repudiation: Senders of a message can't deny having sent a message and the receivers can't deny having received it.
Example: Digital Signatures - Authenticity: Guarantee of something being genuine.
Example: Digital certificates,bio-metrics
Why Information Security attacks happen?
- Attacks occur for a variety of reasons like attackers wanting to steal sensitive information, data disclosure, ransomware and many others.
- It's important to understand the threats that a system may face to implement required preventive measures.
You can start learning and understanding the different hacking phases:
1. Reconnaissance(Footprinting)
2. Scanning
3. Gaining access
4. Maintaining access
5. Clearing logs
Thanks for reading my first post! it may not be much but you start with something.


Top comments (0)