XML Injection is a critical security vulnerability that can compromise Laravel applications using XML-based inputs. Attackers exploit this flaw to manipulate XML data, access restricted files, or execute malicious code.

In this blog, we’ll explore XML Injection in Laravel, how attackers exploit it, and how to secure your application with proper coding practices. Plus, we’ll show you how to test your website security using our Website Vulnerability Scanner.
What is XML Injection?
XML Injection occurs when an application improperly processes user-supplied XML data, allowing attackers to inject malicious XML content. This vulnerability can lead to:
- Unauthorized Data Access – Attackers can read sensitive files.
- Denial of Service (DoS) – Crafted payloads can crash the system.
- Data Manipulation – Malicious users can alter XML responses.
- External Entity Injection (XXE) – Attackers can retrieve internal files.
How Attackers Exploit XML Injection in Laravel
Consider a Laravel application that processes XML-based API requests. If input validation is missing, attackers can inject malicious XML:
Vulnerable Code Example
if ($request->has('xml_data')) {
$xmlData = $request->input('xml_data');
$xml = simplexml_load_string($xmlData); // No validation
$name = $xml->name;
echo "Hello, " . htmlspecialchars($name);
}
Attack Scenario
An attacker submits:
<root>
<name>&sendAttack;</name>
</root>
Without validation, Laravel processes the payload, leading to an XML Injection attack.
How to Prevent XML Injection in Laravel
To secure your Laravel application, follow these best practices:
1. Use Secure XML Parsers
Instead of simplexml_load_string(), use DOMDocument with secure settings:
if ($request->has('xml_data')) {
$xmlData = $request->input('xml_data');
$dom = new DOMDocument();
$dom->loadXML($xmlData, LIBXML_NOENT | LIBXML_DTDLOAD); // Unsafe settings
}
This still allows entity injection. To fix it, use:
if ($request->has('xml_data')) {
$xmlData = $request->input('xml_data');
$dom = new DOMDocument();
libxml_disable_entity_loader(true); // Secure setting
$dom->loadXML($xmlData, LIBXML_NOENT | LIBXML_DTDLOAD);
}
2. Validate User Input Before Processing
Implement strict input validation using Laravel’s validation methods:
$request->validate([
'xml_data' => 'required|string|max:5000'
]);
3. Disable External Entity Processing (XXE Protection)
Modify your XML parser to disable external entity loading:
libxml_use_internal_errors(true);
$xml = new DOMDocument();
$xml->loadXML($xmlData, LIBXML_NOENT | LIBXML_DTDLOAD);
By disabling external entity processing, you prevent XML Injection and XXE attacks.
4. Use JSON Instead of XML
If possible, switch from XML to JSON for data exchange, as JSON is less prone to injection attacks:
$data = json_decode($request->input('json_data'), true);
Test Your Website Security for XML Injection
Wondering if your Laravel website is vulnerable to XML Injection? Use our Free Website Security Checker to scan your site for XML Injection and other vulnerabilities.
📌 Check your website security now
🖼️ Screenshot: Free Website Security Checker
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
After scanning, you will receive a security report detailing vulnerabilities found in your Laravel application to check Website Vulnerability.
🖼️ Screenshot: Website Vulnerability Assessment Report
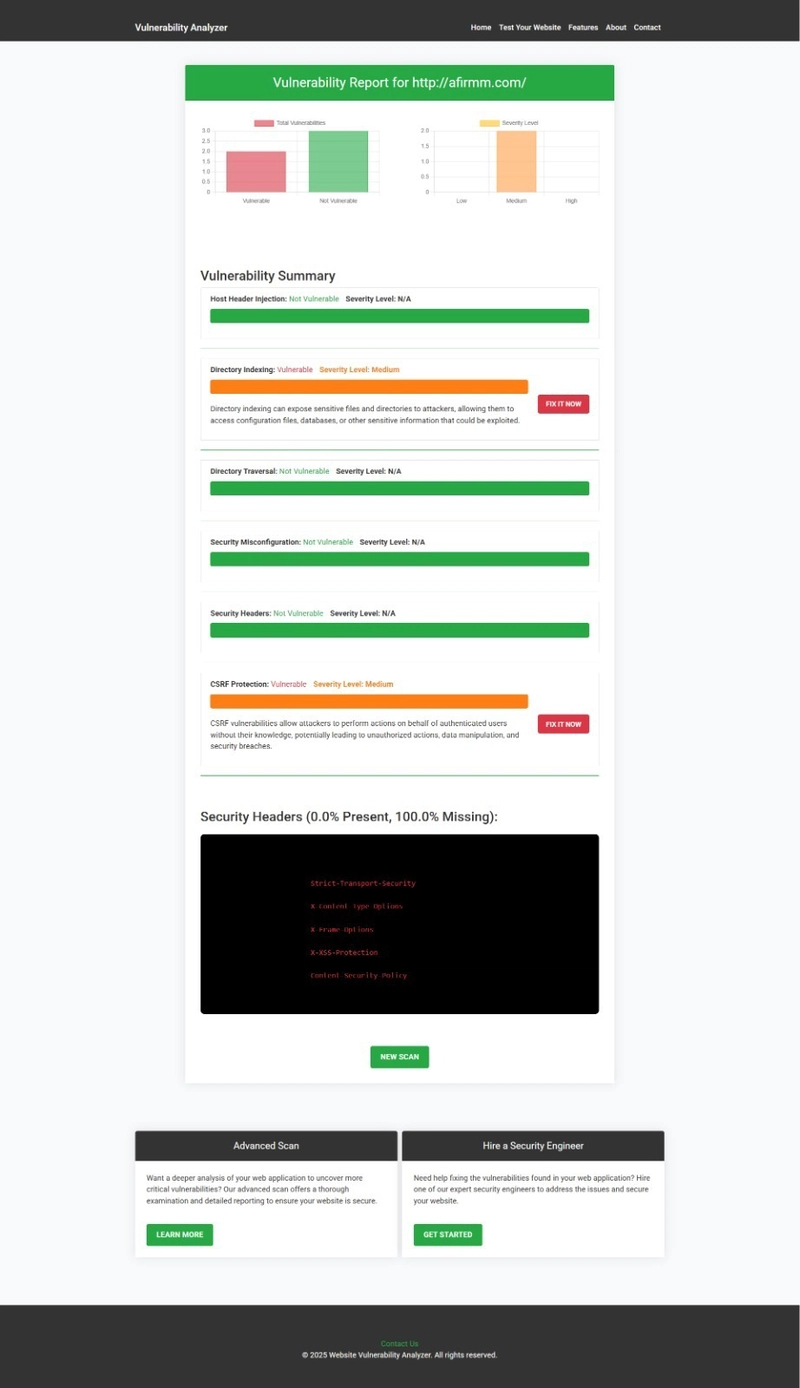 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Final Thoughts
XML Injection is a serious threat to Laravel applications, but it can be prevented with secure coding practices. Always sanitize user inputs, disable external entity processing, and validate XML data.
🔹 Test your website security now using our Free Website Security Scanner, also check our related blog at Pentest Testing Corp.
Do you have questions or need help securing your Laravel application? Drop a comment below or share this blog with developers to spread awareness! 🚀



Top comments (0)