I’m sure that using MFA (Multi-Factor Authentication) today is oblivious.
For 2FA (2-Factor Authentication) the most used method is TOTP – Time-based One-time Password, when alongside with the common login:password also needs to enter a code generated by a device or software.
The most known implementation is Google Authenticator but also there is a lot of other solutions.
On the last couple of days, I was looking for such a solution for our project and have found the Authy – really nice and usable thing.
Authy vs Google Authenticator
Authy benefits in a few words:
- it’s not tied to a concrete device – can be installed on multiple cellphones (but still the original phone number will be used)
- has desktop applications for Windows, macOS, and browsers extension to make access to codes more simple, also – you’ll not be dependent on phone device and still be able to log in if you left your phone on a kitchen
- create accounts backup – when installing Authy on a new device it will restore all your records
See more here>>>.
InstallingAuthy
Install on a phone from Google Play on Apple Store:
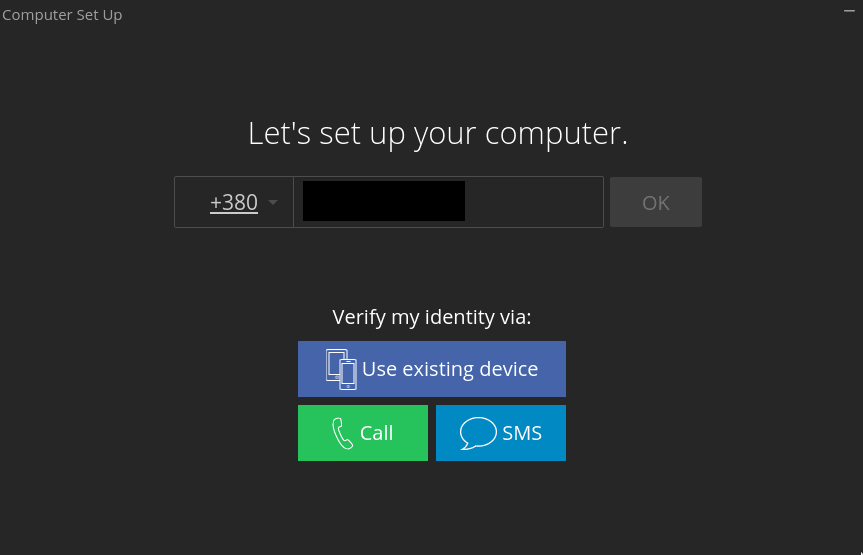
Set your mobile number – it will be also used for authorization on other devices, and your email.
Authorize using SMS or phone call. Best to use SMS as calls will be done via Viber and can be with awful quality:
The is also AUR package for Arch Linux but I didn’t use it and not sure it has a sense as there is nice Chrom’es extension.
Install an application for Chrome via Chrome Apps and extension for quick access.
Application without the extension can be launched via chrome://apps.
For Windows and macOS applications can be downloaded from the downloads page.
Authorize again using SMS:
Configuring Github MFA
Documentation here>>>.
Go to the Settings > Security, click on the Enable two-factor authentification:
Click on the Set up using an app:
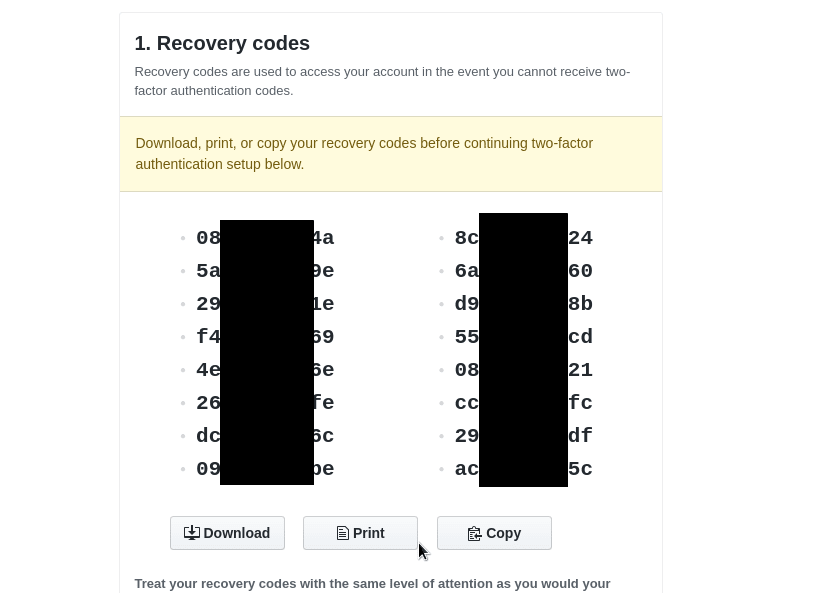
On the next page, you’ll get codes to restore access in case if you’ll lose your MFA-device.
Save them!
On your phone open Authy, click the Add account and set backups password:
The same password will be used to access your data from other Authy applications so store and remember it.
Github will display QR-код:
Scan it from your phone:
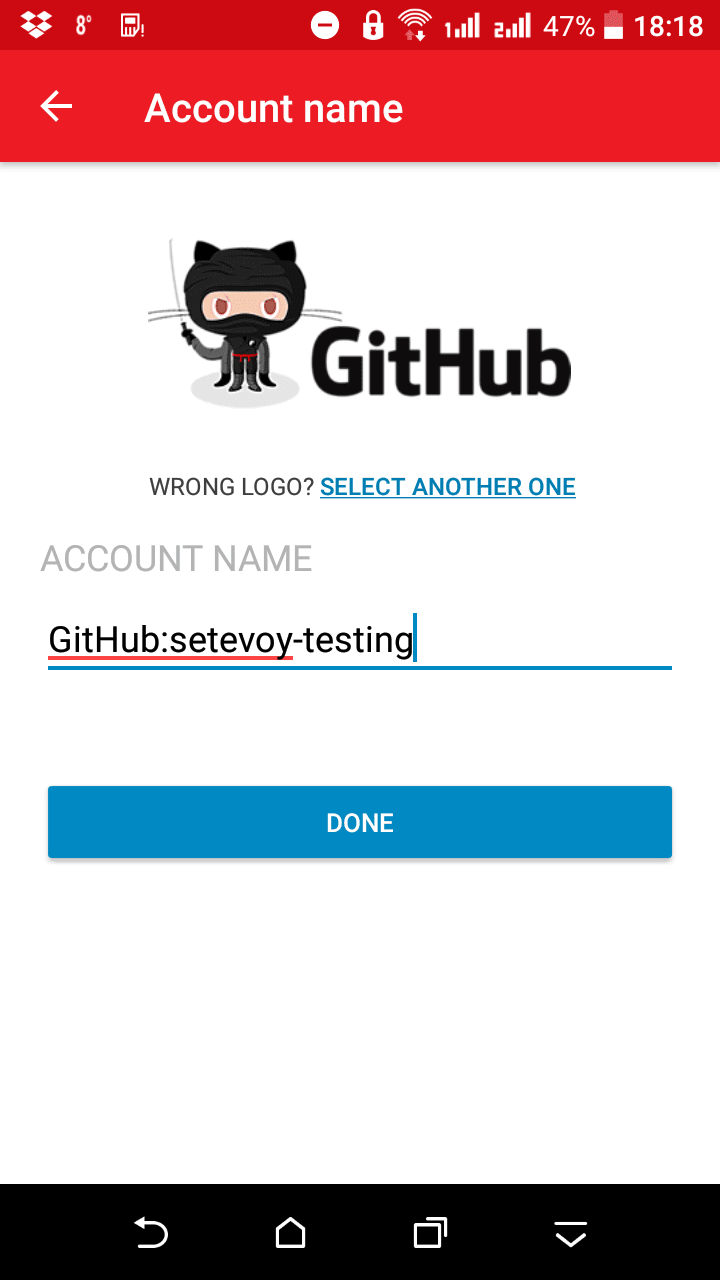
Choose a logo and save new account:
After creating a new account Authy will start displaying generated codes.
Enter it at the bottom on the Github page:
Done:
On this page you also will be able to configure SMS to restore access – do it :
Configuring AWS MFA
Repeat for AWS.
The documentation is available here>>> but it’s a bit outdated.
Go to the Security Credentials:
Click on the Activate MFA:
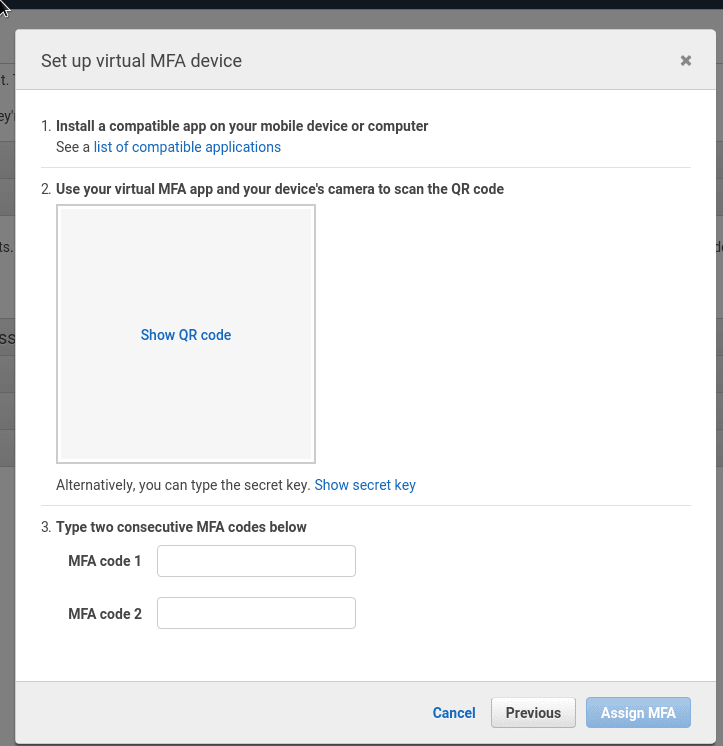
By default the Virtual MFA device will be checked – leave it and press Continue:
Click the Show QR Code:
Scan it, create the account in Authy and enter the code from your Authy application at the bottom, then wait when it will be updated with a new one – and enter again:
Done.
Similar posts
- 04/16/2019 Jenkins: a job to check a Github organization’s public repositories list (0)
- 04/03/2019 MySQL/MariaDB: like Petya ransomware for MySQL and ‘root’@’%’ access (0)
- 03/28/2017 Arch: Git – github.com errno=Connection refused (0)

















Top comments (2)
I would not trust Authy to handle my OTPs.
Their code is not open-source, which means no one can verify that they are handling the data securely.
They use SMS to authenticate users/devices. Not everyone has a phone number and a phone number is personal. A solution to this while not changing much, is to switch to passwordless authentication with email.
I do enjoy the idea behind Authy. It is really nice that people are really trying to promote security.
On a note, you could make email based authentication very secure with PGP. Only people who are crypto geeks would do it this way.
But overall, I think Authy could be going down a slightly better path. But either way, I think it's better having Authy than no multiple factors of authentication.
Oh my god, I have no idea what happened to my comment. I fixed it though. I swear that wasn't there when I posted it.