Testing
This week was the first coming back from the reading week break and I had a few clear cut objectives coming into it. The first thing that I wanted to accomplish was to create an e2e test for the authentication flow that I have added to the open source starchart project. The library that we use for e2e testing is playwright, and using it is actually pretty easy. The corresponding issue for the creation of the test is here. Initially there was a speed bump seeing as the playwright scripts were written to run with a different port but David looked into it and came to the conclusion that using 8080 should be fine and after that change my e2e tests passed CI PR#1 to my branch.
I learned after I was done with creating my test that it is possible to use a plugin to easily record things but doing it how I did it was not far off, instead of using a pretty plugin I just ran the dev server in one console and I ran an npx command in another: npx playwright codegen localhost:8080. This looks a little wonky seeing as for some reason the CSS does not quite take on this browser that is used for recording tests but in any case it makes writing tests easy because you can practically do what you want to test and it records the playwright syntax that would re-produce your actions on the specified URL (in this case localhost:8080). Here's how it looks:
along with a console that allows you to pick elements out of the page and start and stop recording along with a real time view of the playwright syntax you are recording with your actions:
Something similar to the auth test that I wrote in #294 was later used as a dependency for the rest of the e2e tests in a PR written by Eakam #313.
This is a video from the playwright devs showing off project dependencies, what was used in #313. https://www.youtube.com/watch?v=PI50YAPTAs4
Staging SAML
The second order of business this week was to bring the local idp I set up more in line with the staging idp by actually testing our SAML in staging and seeing what claims we get back from Azure AD and then taking those claims and configuring our simpleSAMLphp local idp to return the same claims.
David tasked me with gutting starchart so that all that was left was the SAML logic basically and so that is what I did. Then after the second meeting of the week we got on a call and took my butchered branch to staging after I pushed it as an image to dockerhub so that he could run a container of it.
There was a problem that I did not understand when we got to trying to run it, to solve it David pulled up the files in the build folder and added logging to key points where our IDP was being used to find that despite us setting the IDP in an init method when the code called for its use it was undefined. This was the impetus for the changes to the init logic that David had setup the weeks prior in #321. The change towards loading the idp metadata from a file turns out to also be the recommendation from a security perspective as well apparently as mentioned here.
After fixing the issue we were able to see what the response from the actual Seneca IDP would look like:
{
"attributes":{
"displayname":"Stefan Frunza",
"email":"sfrunza@myseneca.ca",
"group":"mycustomdomain-dev-students",
"http://schemas.microsoft.com/claims/authnmethodsreferences":"http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password",
"http://schemas.microsoft.com/identity/claims/identityprovider":"https://sts.windows.net/eb34f74a-58e7-4a8b-9e59-433e4c412757/",
"http://schemas.microsoft.com/identity/claims/objectidentifier":"61e8ee88-bd7c-453f-be1d-f11778b7c191",
"http://schemas.microsoft.com/identity/claims/tenantid":"eb34f74a-58e7-4a8b-9e59-433e4c412757",
"sAMAccountName":"sfrunza"
},
"audience":"https://mycustomdomain-dev.senecacollege.ca/sp",
"conditions":{
"notBefore":"2023-03-08T20:39:18.590Z",
"notOnOrAfter":"2023-03-08T21:44:18.590Z"
},
"issuer":"https://sts.windows.net/eb34f74a-58e7-4a8b-9e59-433e4c412757/",
"level":"info",
"message":"Saml Response",
"nameID":"bwNMtMWvOf99rmm1zCSelnfkgSOijBEQubNe0G7Ir58",
"response":{
"destination":"https://mycustomdomain-dev.senecacollege.ca/login/callback",
"id":"_295e9f6d-abeb-41ae-bef4-10b4112c8bb1",
"inResponseTo":"_bf26e2ce-93f6-4816-8ad9-cb74629f80e1",
"issueInstant":"2023-03-08T20:44:18.767Z"
},
"sessionIndex":{
"authnInstant":"2023-03-08T20:44:17.232Z",
"sessionIndex":"_920c1410-15fe-44be-ac98-70d17cb73000"
},
"timestamp":"2023-03-08T20:44:20.906Z"
}
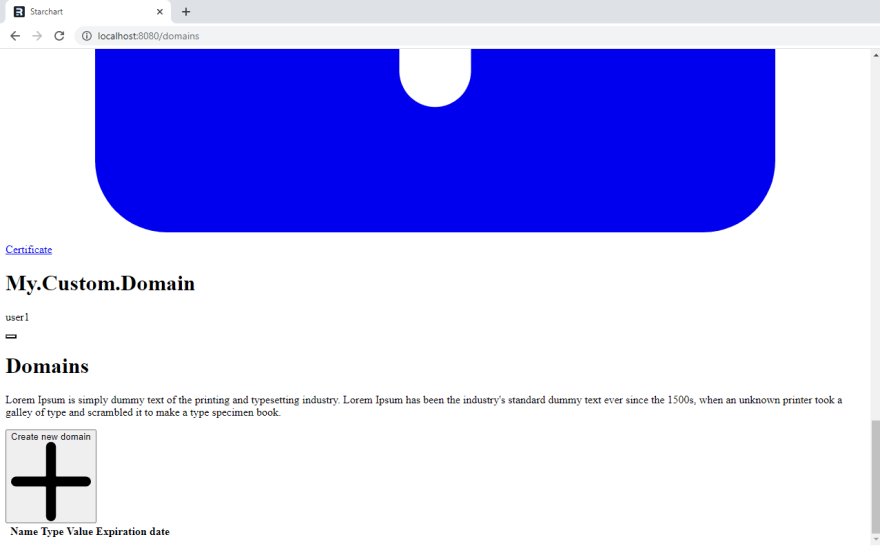
I was also able to take some snapshots of our great victory:
The work we did here allowed Chen and I to rework the user model and simpleSAMLphp config in the following #312 #307
Looking forward
I noticed that the routing is deprecated and slated to change to flat routes and opened the following issue #320.
I also opened an issue to do with how we plan to handle admins, in that the admins are meant to be able to assume control of regular user accounts and so there should be an "effective username" field as well #306. The effective username should come in empty only for admins and the rest of the users should have that field be populated with their username.






Top comments (0)