Welcome back, fellow tech explorers! 🚀 If you've been following my blog series on computer networking, you already know the drill. So far, I’ve covered:
Computer Networking Basics – Where we cracked the networking code.
Data Link Layer (Part 1 & Part 2) – Where we learned how devices whisper
secrets to each other using MAC addresses and frames.
If you haven’t read them yet, go check them out! Trust me, they’ll make this journey much smoother.
Now, let’s talk about the Network Layer – the part of networking that ensures your data finds its way through the chaotic digital highways. Think of it like Google Maps for the internet.
Introduction: The Network Layer
"The Network Layer is the third layer in the OSI (Open Systems Interconnection) model and plays a crucial role in data transmission across networks. It is responsible for routing, forwarding, and addressing data packets to ensure they reach their intended destination." ok done with text book definition now, let's understand it with interesting example:
Imagine ordering a pizza, but the delivery guy has no map. He takes random turns, gets lost, and your pizza never arrives. That's what happens to data packets without proper routing! Luckily, the Network Layer acts like Google Maps, ensuring your data (or pizza) reaches the right destination.
In this blog, we’ll explore how IP addresses, routers, and routing algorithms work together to make internet magic happen. Let’s dive in! 🚦💻
Function of Network layer
Logical Addressing (IP Addressing) – Assigns unique IP addresses to
devices to ensure data reaches the correct destination.Routing– Determines the best path for data packets to travel across
networks.Packet Forwarding – Moves packets from one network to another based
on routing decisions.Fragmentation and Reassembly – Splits large data packets into
smaller ones for transmission and reassembles them at the destination.Error Handling & Diagnostics – Uses protocols like ICMP to detect
issues like unreachable hosts or network congestion.Traffic Control & Congestion Avoidance – Manages network congestion
by optimizing data flow and rerouting packets if necessary.
IP Addressing and Subnetting
Before your data finds its way through the network, it needs an address—just like a home address for postal mail. In the networking world, this is done using IP addresses. The Network Layer ensures that every device has a unique identity so that data reaches the correct destination.
IPv4 vs. IPv6: The Addressing Evolution
There are two main types of IP addresses:
IPv4 (Internet Protocol Version 4)
- Uses a 32-bit address (4 bytes).
- Decimal notation (e.g., 192.168.1.1).
- Can support around 4.3 billion unique addresses.
- Due to the internet’s rapid growth, IPv4 addresses are running out.
IPv6 (Internet Protocol Version 6)
- Uses a 128-bit address (16 bytes).
- Hexadecimal Notation (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334)
- Can support an almost infinite number of addresses(340 undecillion).
- Includes improved security and efficiency features.
Think of IPv4 as old-school phone numbers with limited digits, while IPv6 is like modern international phone numbers with a much larger range.
Classful Addressing: The Traditional IP Addressing Method
Classful addressing was the original method used for IP address allocation, where IP addresses were divided into fixed-size classes.
Each IP address consists of two parts:
- Network Part – Identifies the network.(prefix)
- Host Part – Identifies individual devices (hosts) within that network.(suffix)
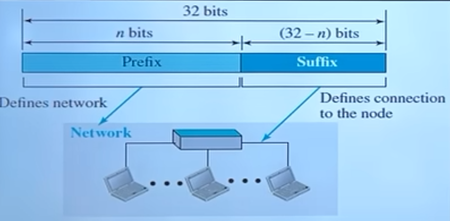
However, classful addressing led to inefficient IP usage, which is why Classless Inter-Domain Routing (CIDR) replaced it. But understanding classful addressing is still important!
IP Address Classes (A to E)
In classfull addressing, IP addresses are divided into five classes (A to E) based on their first few bits and range of values.
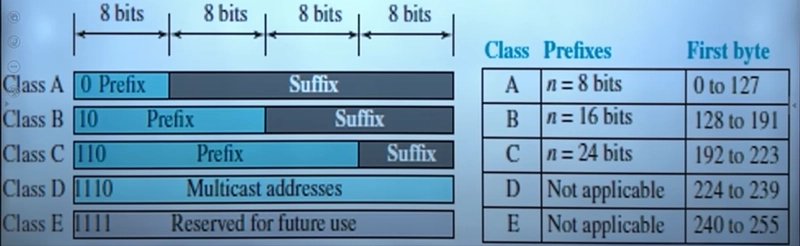
1.Class A (Large Networks like ISPs, Government, Large Corporations)
- First Bit: Always starts with 0 (binary: 0xxxxxxx).
- Range: 1.0.0.0 to 126.255.255.255.
- Prefix Length: 8 bits (n = 8) → Net ID: 8 bits, Host ID: 24 bits.
- Supports: 16 million hosts per network (2²⁴ - 2 addresses per network).
- Example: Google (8.8.8.8), Apple (17.x.x.x) use Class A addresses.
📌 Note: 127.x.x.x is reserved for loopback addresses (used for testing on a local machine).
2.Class B (Medium-Sized Networks like Universities, Large Organizations)
- First Two Bits: Always starts with 10 (binary: 10xxxxxx).
- Range: 128.0.0.0 to 191.255.255.255.
- Prefix Length: 16 bits (n = 16) → Net ID: 16 bits, Host ID: 16 bits.
- Supports: 65,536 hosts per network (2¹⁶ - 2 addresses per network).
- Example: Many universities and corporations use Class B addresses.
3.Class C (Small Businesses, Local Networks, Home Networks)
- First Three Bits: Always starts with 110 (binary: 110xxxxx).
- Range: 192.0.0.0 to 223.255.255.255.
- Prefix Length: 24 bits (n = 24) → Net ID: 24 bits, Host ID: 8 bits.
- Supports: 254 hosts per network (2⁸ - 2 addresses per network).
- Example: Home Wi-Fi networks often use private Class C addresses (192.168.x.x).
📌 Note: This class is widely used in private networking (e.g., routers assigning IPs like 192.168.1.1).
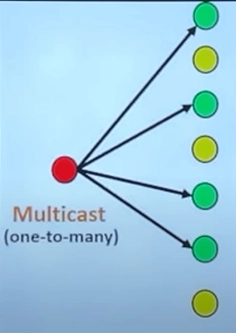
4.Class D (Multicast Applications like Streaming, Live Feeds)
- First Four Bits: Always starts with 1110 (binary: 1110xxxx).
- Range: 224.0.0.0 to 239.255.255.255.
- Purpose: Used for multicasting, where one sender transmits to multiple receivers (e.g., video conferencing, IPTV).
- No Net ID / Host ID: Instead of assigning hosts, Class D uses group IDs.
- Example: Video streaming services and real-time data sharing use multicast addressing.
📌 Note: Class D does not support subnetting since it’s used for group communication.
5.Class E (Experimental & Future Use, Reserved by IETF)
- First Four Bits: Always starts with 1111 (binary: 1111xxxx).
- Range: 240.0.0.0 to 255.255.255.255.
- Purpose: Reserved for future networking research and experiments.
- Not Used for Public Internet: No devices or organizations use Class E addresses.
- Example: Research institutions and networking experiments may utilize this class.
📌 Note: You cannot assign Class E addresses to hosts or routers in practical networking.
Casting in Networking: How Data is Sent
In networking, casting refers to how data is transmitted from one device to another. There are three main types:
- Unicast: Transmitting data from one source host to one destination host.(one to one transmission) (e.g., sending an email to a specific person).
- Multicast: Transmitting data from one source host to a particular group of hosts having an interest in receiving the data.(One-to-many communication) (e.g., streaming a live event to multiple users).
- Broadcast: Transmitting data from one source host to all other hosts residing in a network either same or other network.(One-to-all communication) (e.g., a DHCP request sent to all devices in a network).
What is Subnetting? Why is it Needed?
Subnetting is the process of dividing a large network into smaller, manageable sub-networks (subnets).
Why is subnetting important?
Helps reduce network congestion by limiting broadcast traffic.
Improves security by isolating different network segments.
Ensures efficient use of IP addresses, preventing wastage.
For example, instead of using a single Class A network with millions of devices, subnetting allows dividing it into smaller networks to improve efficiency.
Subnet Mask: The Key to Subnetting
A Subnet Mask helps identify which part of an IP address belongs to the network and which part belongs to the host.
For example, in 192.168.1.0/24 (Subnet Mask: 255.255.255.0):
192.168.1.0 is the network portion.
The last octet (0-255) represents host addresses.
Common Subnet Masks:
Class A: 255.0.0.0 (/8)
Class B: 255.255.0.0 (/16)
Class C: 255.255.255.0 (/24)
By adjusting the subnet mask, networks can be further divided into smaller subnets, optimizing IP allocation.
Classless Addressing
Classless Addressing is a modern method of IP addressing that removes the limitations of fixed classes (A, B, C) and allows networks to use IP addresses more efficiently. It is implemented through CIDR (Classless Inter-Domain Routing).
Why Was Classless Addressing Adopted?
Classful addressing caused two major problems:
-
IP Address Wastage:
- Class A networks had 16 million addresses, but even a large organization might use only a few thousand.
- This led to a shortage of available IPv4 addresses.
-
Rigid Network Sizes:
- Companies needed more flexible subnetting instead of being forced into Class A, B, or C.
- Classless addressing allows custom subnet sizes instead of being stuck with classful limits.
How Classless Addressing Works?
Instead of dividing IPs into strict classes, CIDR allows any number of bits to be allocated for the network and host portions. This helps in efficient IP allocation.
CIDR Notation (Classless Inter-Domain Routing Notation)
CIDR (Classless Inter-Domain Routing) notation is a shorthand representation of IP addresses and their subnet masks. It defines how many bits belong to the network portion of an address.CIDR Notation Format: IP Address / Subnet Bits, The /x (suffix) tells us how many bits are used for the network portion.The remaining bits are used for the host portion.
Example 1: 192.168.1.0/24
/24 means the first 24 bits are for the network.
The last 8 bits are for host addresses.
Subnet Mask: 255.255.255.0
Total Hosts: 2⁸ - 2 = 254 (excluding network and broadcast addresses).
Example 2: 10.0.0.0/16
/16 means the first 16 bits are for the network.
The remaining 16 bits are for host addresses.
Subnet Mask: 255.255.0.0
Total Hosts: 2¹⁶ - 2 = 65,534
How CIDR Improves IP Allocation?
Instead of using fixed Class A, B, or C, CIDR customizes network sizes based on actual needs.
Example: A company may require 5000 IP addresses. In classful addressing, they would need a Class B network (65,536 IPs). With CIDR, they can use a /19 subnet (8192 IPs), avoiding waste.
Supernetting (Merging Multiple Networks into One)
Supernetting is the process of combining multiple smaller networks (subnets) into a larger network to improve routing efficiency. It is the opposite of subnetting.
Used to reduce routing table size by advertising one large block instead of multiple small ones.
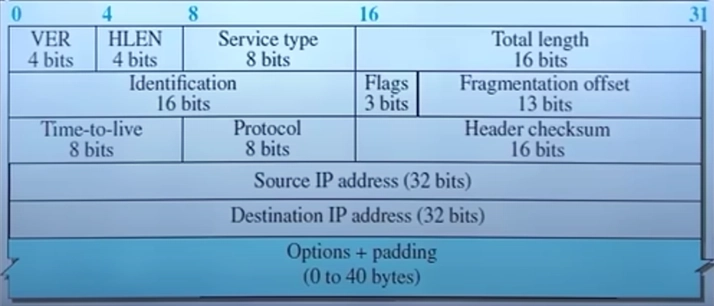
IPv4 Header

a payload refers to the actual data being transmitted inside a packet. It is the part of the packet that carries the useful information intended for the receiver, excluding headers, trailers, and metadata.
IPv4 Header Fields
Version – Specifies the IP version being used. For IPv4, this value is always 4.
Header Length (HLEN) – Defines the size of the header. Since IPv4 headers can have optional fields, their size may vary.
Type of Service (ToS) / Services type – Helps prioritize network traffic. For example, video calls may need higher priority than normal browsing.
Total Length – Represents the full size of the packet, including the header and the actual data (payload).
Identification – A unique number assigned to each packet to help reassemble fragmented data. If a large file is broken into smaller packets, this field helps put them back in order.
Flags – Controls fragmentation of packets. It tells whether a packet can be fragmented and if more fragments are coming.
Fragment Offset – If a packet is split into smaller parts, this field helps routers and devices reassemble them in the correct order.
Time to Live (TTL) – Limits how long a packet can travel in a network. Each router decreases its value, and if it reaches zero, the packet is discarded to prevent infinite loops.
Protocol – Indicates which transport layer protocol (like TCP or UDP) is being used to handle the data.
Header Checksum – A mechanism for error detection in the header. If an error is found, the packet is discarded and retransmitted.
Source IP Address – The IP address of the device that sent the packet.
Destination IP Address – The IP address of the intended recipient of the packet.
Options (Optional Field) – Provides extra functionalities like security, timestamp, and routing preferences. It is not commonly used.
Padding (Optional Field) – Fills up extra space in the header to maintain proper alignment for processing efficiency.
Key Limitation of IPv4 Header:
- Lacks security features.
- Limited address space (only ~4.3 billion addresses).
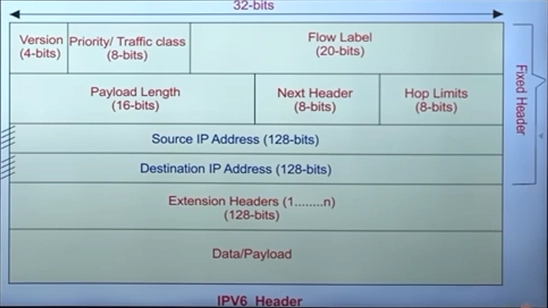
IPv6 Header Fields
Version – Specifies the IP version being used. For IPv6, this value is always 6.
Traffic Class – Similar to the Type of Service (ToS) field in IPv4, it helps prioritize certain types of network traffic.
Flow Label – Helps maintain smooth and consistent data flow for real-time applications like VoIP and video streaming.
Payload Length – Specifies the size of the actual data (payload) being carried by the packet.
Next Header – Specifies the type of information following the IPv6 header. It helps in identifying whether the next part is TCP, UDP, or additional extension headers.
Hop Limit – Functions like TTL in IPv4, preventing packets from looping indefinitely by decreasing its value at every hop. If it reaches zero, the packet is discarded.
Source Address – The IPv6 address of the sender.
Destination Address – The IPv6 address of the intended recipient.
Key Protocols of the Network Layer: ARP, ICMP, and IGMP
The Network Layer is responsible for moving packets from source to destination. However, just sending packets isn’t enough—devices in a network need to find each other, report errors, and manage group communication. That’s where three important protocols come into play:
ARP (Address Resolution Protocol) – Helps devices find each other in a local network.
ICMP (Internet Control Message Protocol) – Reports errors and network issues.
IGMP (Internet Group Management Protocol) – Manages communication between multiple devices in a group.

Let’s break them down one by one.
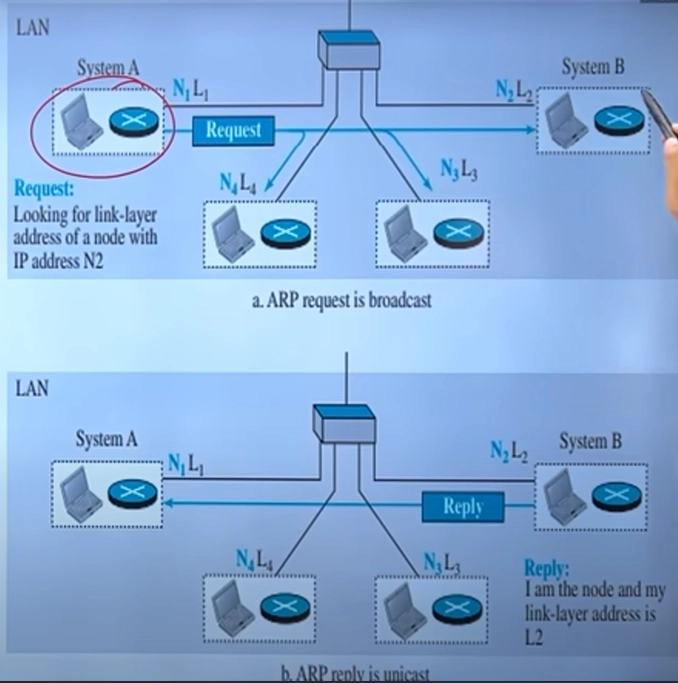
Address Resolution Protocol (ARP) – "The Detective of the Network"
Imagine you’re sending a letter to your friend. You know their name, but you don’t know their house number. So, you ask a neighbor, and they tell you the address. That’s exactly what ARP does in a network!
Computers communicate using IP addresses, but actual data travels using MAC addresses (the physical address of a device’s network card). ARP maps IP addresses to MAC addresses so devices can find each other.
🛠 How ARP Works?
If a device wants to send data but only knows the IP address of the receiver, it broadcasts an ARP request asking, "Who has this IP? Tell me your MAC address!"
The device with the matching IP replies with an ARP response containing its MAC address.
The sender now has the MAC address and can send the data.
🔥 Why is ARP Important?
Without ARP, devices in a LAN wouldn’t be able to communicate because they wouldn’t know each other’s MAC addresses.
ARP caches (stores) resolved addresses to speed up future communication.
ARP can be exploited in cyberattacks (ARP Spoofing), where attackers trick a device into sending data to the wrong MAC address.
Internet Control Message Protocol (ICMP) – "The Network's Troubleshooter"
ICMP is like a network doctor—it diagnoses connection problems and reports errors. It doesn’t send actual data but helps troubleshoot packet loss, unreachable networks, and latency issues.
🛠 How ICMP Works?
If a packet fails to reach its destination (e.g., due to an unreachable network), ICMP sends an error message back to the sender.
Network administrators use ping (ICMP Echo Request) to check if a device is online and responding.
Traceroute (ICMP Time Exceeded) helps find the path packets take across the internet.
🔥 Why is ICMP Important?
Helps diagnose connectivity issues (e.g., if a website is down).
Used in ping tests to check if a server or router is active.
Prevents endless loops by setting a Time-to-Live (TTL), so packets don’t travel forever.
Example:
Ping Command (ping google.com) – Sends ICMP Echo Requests to check if Google’s server is online.
Traceroute (tracert google.com) – Shows the path a packet takes to reach Google’s servers.
⚠️ Security Concern:
Attackers can use ICMP in DDoS attacks (e.g., Ping of Death, Smurf Attack) to flood a network with useless traffic.
Internet Group Management Protocol (IGMP) – "The Group Manager"
IGMP helps devices communicate in multicast groups. Instead of sending multiple copies of the same data to different devices, IGMP allows efficient group communication by delivering data to multiple recipients at once.
🛠 How IGMP Works?
A device joins a multicast group (e.g., an online live stream).
The router, using IGMP, registers the device and ensures it receives the multicast data.
When the device leaves the group, IGMP updates the router to stop sending unnecessary traffic.
🔥 Why is IGMP Important?
Reduces network traffic by avoiding duplicate transmissions.
Used in live video streaming, online gaming, and IPTV (Internet TV).
Helps in efficient routing for group-based communication.
Example of IGMP in Action:
Watching a Live Sports Stream: Instead of sending the same video to each viewer individually, the server sends one multicast stream, and IGMP ensures only interested users receive it.
Routing in the Network Layer
Routing is the process of finding the best path for data packets to travel from the sender to the receiver across multiple networks. It ensures that data reaches its correct destination efficiently.
How Does Routing Work?
Every packet has a destination IP address.
Routers analyze the destination address and decide where to forward the packet.
Routers use routing tables and algorithms to determine the best path for packet delivery.
Types of Routing
Static Routing – Routes are manually configured by the network administrator.
Dynamic Routing – Routes are automatically learned and updated using routing protocols.
Default Routing – Used when there is only one exit path for all unknown destinations (common in home networks).
Packet Forwarding and Routing Tables
What is Packet Forwarding?
Once a router decides the best path for a packet, it needs to forward the packet to the next device on the path. This process is called packet forwarding.
What is a Routing Table?
A routing table is a list of rules that helps routers decide where to send packets. It contains:
Destination IP Address – Where the packet needs to go.
Next Hop – The next device/router in the path.
Metric – A value that helps determine the best route (e.g., shortest path, fastest link).
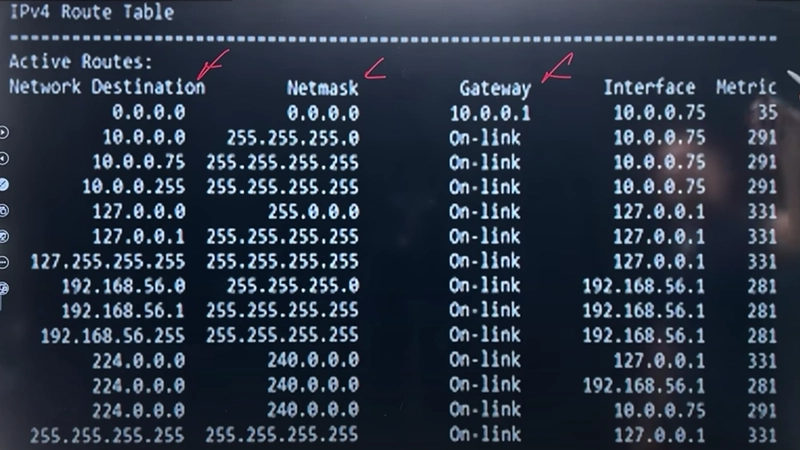
Routing Protocols Used for Packet Forwarding
RIP (Routing Information Protocol) – Uses hop count to find the best path.
OSPF (Open Shortest Path First) – Uses link-state information to calculate the best route.
BGP (Border Gateway Protocol) – Used for routing between different networks on the internet.
Network Address Translation (NAT) & Its Role
Network Address Translation (NAT) is a technique that allows multiple devices in a private network to share a single public IP address to access the internet.
Why is NAT Important?
Solves IPv4 Address Shortage – Since IPv4 addresses are limited, NAT allows multiple devices to use a single IP address.
Adds a Layer of Security – NAT hides internal IP addresses, making it harder for hackers to target devices.
Reduces Costs – ISPs provide fewer public IPs, and companies can still connect multiple devices.
Types of NAT
Static NAT – Maps one private IP to one public IP.
Dynamic NAT – Maps private IPs to a pool of public IPs.
PAT (Port Address Translation) – Multiple private IPs share one public IP using different port numbers (most common type).
Example of NAT in Action
Home Network Example:
Your home router has one public IP address, but multiple devices (laptops, phones, TVs) can browse the internet using that same public IP due to NAT.
Challenges and Security Concerns in the Network Layer
While the network layer ensures smooth communication, it also faces several challenges and security risks:
1. Routing Attacks
Man-in-the-Middle (MITM) Attack – Attackers intercept and manipulate network traffic.
Route Hijacking – Malicious entities advertise incorrect routes, disrupting traffic flow.
2. IP Address Spoofing
- Hackers fake an IP address to disguise their identity or impersonate a trusted device.
3. DDoS (Distributed Denial of Service) Attacks
- Attackers overload a network with massive traffic, causing services to crash.
4. IPv4 Address Exhaustion
- IPv4 addresses are running out, making IPv6 adoption necessary.
5. NAT and Performance Issues
- While NAT provides security, it can cause issues with applications that require direct peer-to-peer communication, such as VoIP and online gaming.
Conclusion
The Network Layer is a crucial part of the OSI model that ensures data is properly routed and delivered across different networks. It manages IP addressing, packet forwarding, and routing, making global communication possible. Technologies like IPv4, IPv6, NAT, and routing protocols help in efficient data transmission, while security measures protect networks from attacks.
Thank you for reading! I hope this blog helped you understand the Network Layer better. If you found it useful, feel free to follow me on my social media for more tech content:
🔗 Linkedin
🔗 X (Twitter)
Stay connected and keep learning! 🚀



Top comments (0)