HMM, Now it is time to create a caching/proxy server using squid proxy open source project
sudo apt install squid
sudo systemctl enable --now squid
touk@ubuntu:/etc/squid$ tree
.
├── conf.d
│ ├── debian.conf
│ └── local.conf
├── errorpage.css
└── squid.conf
1 directory, 4 files
For simplicity, we’ll create our customize config file in conf.d, and as you can see i have local.conf file under the conf.d directory
touk@ubuntu:/etc/squid/conf.d$ cat local.conf
http_port 8080
cache_dir ufs /var/spool/squid 100 16 256
Here, I have setup squid to use port 8080, and use it as my caching server
this will work only for my local host because i need to create some acl and decide which clients will use it
sudo systemctl restart squid
squid will use the default port 3128 by default ( other ports are in UNCONN state)
touk@ubuntu:/etc/squid/conf.d$ sudo ss -tunap | less -s | grep 8080
tcp LISTEN 0 256 *:8080 *:* users:(("squid",pid=117073,fd=17))
touk@ubuntu:/etc/squid/conf.d$ sudo ss -tunap | less -s | grep squid
udp UNCONN 0 0 0.0.0.0:53267 0.0.0.0:* users:(("squid",pid=117073,fd=9))
udp UNCONN 0 0 *:38167 *:* users:(("squid",pid=117073,fd=5))
udp ESTAB 0 0 [::1]:48837 [::1]:47244 users:(("squid",pid=117073,fd=20))
tcp LISTEN 0 256 *:8080 *:* users:(("squid",pid=117073,fd=17))
tcp LISTEN 0 256
And sure enough, from the access logs i can see my caching is working perfect:
root@ubuntu:/etc/squid/conf.d# tail -f /var/log/squid/access.log
1693403379.468 293103 127.0.0.1 TCP_TUNNEL/200 2459 CONNECT incoming.telemetry.mozilla.org:443 - HIER_DIRECT/34.120.208.123 -
1693403379.468 293171 127.0.0.1 TCP_TUNNEL/200 5155 CONNECT incoming.telemetry.mozilla.org:443 - HIER_DIRECT/34.120.208.123 -
1693403381.469 171233 127.0.0.1 TCP_TUNNEL/200 5919 CONNECT adservice.google.dz:443 - HIER_DIRECT/142.251.143.98 -
1693403381.469 289049 127.0.0.1 TCP_TUNNEL/200 6976 CONNECT googleads.g.doubleclick.net:443 - HIER_DIRECT/142.251.143.162 -
1693403381.469 171521 127.0.0.1 TCP_TUNNEL/200 8278 CONNECT adservice.google.com:443 - HIER_DIRECT/142.251.143.162 -
1693403390.429 175780 127.0.0.1 TCP_TUNNEL/200 18484 CONNECT encrypted-tbn0.gstatic.com:443 - HIER_DIRECT/142.251.143.206 -
1693403391.429 171131 127.0.0.1 TCP_TUNNEL/200 8341 CONNECT id.google.com:443 - HIER_DIRECT/142.251.143.131 -
1693403391.429 286197 127.0.0.1 TCP_TUNNEL/200 18109 CONNECT www.gstatic.com:443 - HIER_DIRECT/142.251.143.99 -
1693403392.429 294374 127.0.0.1 TCP_TUNNEL/200 1654131 CONNECT www.google.com:443 - HIER_DIRECT/142.251.143.100 -
1693403478.431 171006 127.0.0.1 TCP_TUNNEL/200 5449 CONNECT contile.services.mozilla.com:443 - HIER_DIRECT/34.117.237.239 -
RESTRICTING SERVER ACCESS
root@ubuntu:/etc/squid/conf.d# cat local.conf
http_port 8080
cache_dir ufs /var/spool/squid 800 16 256
auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/htpasswd
auth_param basic realm proxy
acl internal src 192.168.1.0/255.255.255.0
acl authenticated proxy_auth REQUIRED
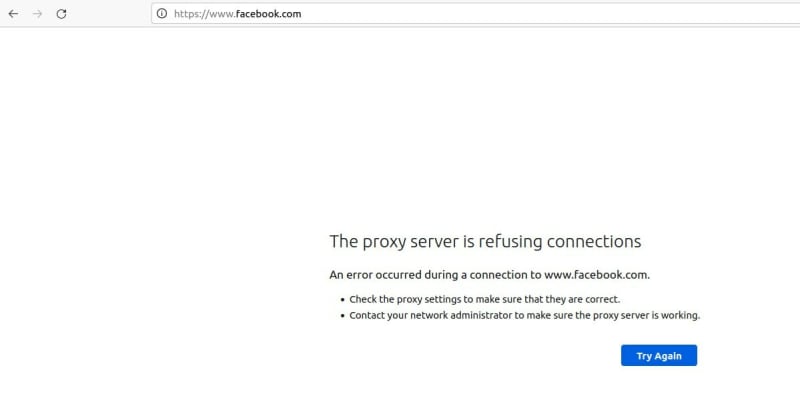
acl blocked_websites dstdomain facebook.com fb.com linux.com
http_access deny blocked_websites
http_access allow internal authenticated
Let me explain this:
- I am using the proxy via port 8080
- I am using the cache directory in /var/spool/squid and 800 is the size by default with a megabyte
- Now i have created the ACL, i am creating the hosts which are defined by 'internal' and then the action that will be applied on them
acl internal src 192.168.1.0/255.255.255.0
http_access allow internal
With Squid you can restrict access by domain name or regular expression
If it is a long list of domain you can use a file populated by these domains, maybe you have a script that will do this for you
In this example, i'll block video streaming from domains inserted into a file
acl video_streaming dstdomain "/etc/squi/streaming.list"
http_access deny video_streaming
You can view a full list of ACL TYPES on this page




Top comments (0)