This is a series of posts on Blockchain, Ethereum, Smart Contracts and their security. The work was done in collaboration with Dr. Andrew Melnik, Marvin Koppka and Mustafa Erdogan at Bielefeld University under ISY Project: NFTs and Cryptocurrencies With Smart Contracts with the aim to provide a reference material on the blockchain technology.
In this second post we will examine Ethereum architecture and two of its consensus algorithms, Proof of Work and Proof of Stake, which allow all nodes in the network to agree on a single state of the blockchain.
Part 2. Ethereum
See also Part 1. Blockchain for an overview of Blockchain, its security fundamentals and issues arising from the choice of its consesus algorithm, such as 51% attack and energy consumption, and Part 3. Smart Contracts for a quick overview, risks, including reentrancy attack, and NFT use case with the objective to examine its storage options and associated risks.
2.1 Introduction
Ethereum is a decentralized community-driven open-source Blockchain created for various purposes such as Decentralized Finance (DeFi), more transparent supply chains, healthcare and smart contracts. With its special structure Ethereum saves additional information such as Transactions Receipts and the resulting state calculated by the Ethereum Virtual Machine (EVM) in multiple data structures called Patricia Merkle Tries.
Due to additional information given by the Tries, such as the state, light clients — nodes that do not have a full copy of the blockchain — are not just able to prove inclusion of transactions but also verify given information about the state. While this information would normally result in the verification of every single transaction in the entire chain, this can be apprehended by saving these states. As such, transactions in the Blockchain are more easily verifiable for certain kinds of queries.[9] Additionally, Smart Contracts, which we will cover in the next post, enable automation of contracts effectively replacing the need for third parties, and creation of Tokens, such as non-fungible tokens (NFTs).
2.2 Workflow
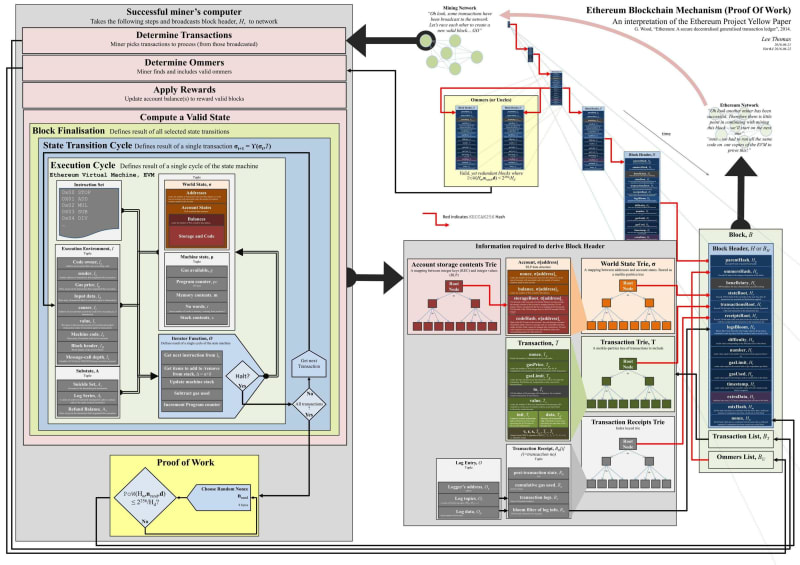
Figure 1 outlines the workflow of Ethereum Blockchain detailing specific components of each data structure and Keccak-256 hashes indicated by red lines. In the following sections which we will explain different stages of that workflow.
2.2.1 Mining Network
Starting with the topside of the figure, the Mining Network, it consists of several computers called nodes forming a peer-to-peer network. Each of these nodes runs a blockchain client to access the Blockchain, albeit there are differences in nodes. A node can either be an archive, full or light node.[2] Transactions added to the blockchain originate from nodes or wallets that interact with nodes.
These transactions get added to a node temporary memory pool, which is simply a pool of transactions waiting to be added into a candidate block, discussed in the previous post about Blockchain, see Section 1.3. Each node has its own memory pool where new transactions are added after being propagated along the network. Next, we will see what happens to these transactions.
2.2.2 Block Finalization
For transactions to be included in the blockchain they need to be included in a block (left side of the Figure 1 - Determine Transactions). The finalization of the block involves four stages which as can be seen in the Ethereum Yellow Paper (11. Block Finalisation) vary depending on whether the block is finalized for mining or has already been mined and needs to be validated.[4] In our case, ommers and transactions need to be determined and added to the block. The first transaction in the list of transactions is the application of rewards, the beneficiary address for miners to receive rewards. After that, at the fourth stage the process of mining starts which computes a valid state and block nonce. Before explaining the process of the consensus algorithms let us first examine the block structure, including the data structures used and the way transactions are added to the network.
2.2.3 Accounts and Blocks
As shown in Figure 1 and Figure 1, 2 from the previous post, blocks consist of a Block header, transactions and an ommers list. Transactions can be added by Ethereum accounts, namely Externally owned accounts (EOA) and contract accounts. Accounts, as discussed in the previous post Section 1.1.3, are generated from 256-bit private keys using elliptic curve algorithms. Externally owned Accounts are essentially accounts created and controlled by anyone holding the corresponding private key. While EOAs can receive, hold, send Ether or tokens and interact with deployed smart contracts on their own, contract accounts can only send transactions after receiving incoming transactions from either EOAs or other contracts if the first transaction was initiated by an EOA. Contract accounts are smart contracts deployed in the network and are controlled by code. They will be discussed in the next post.
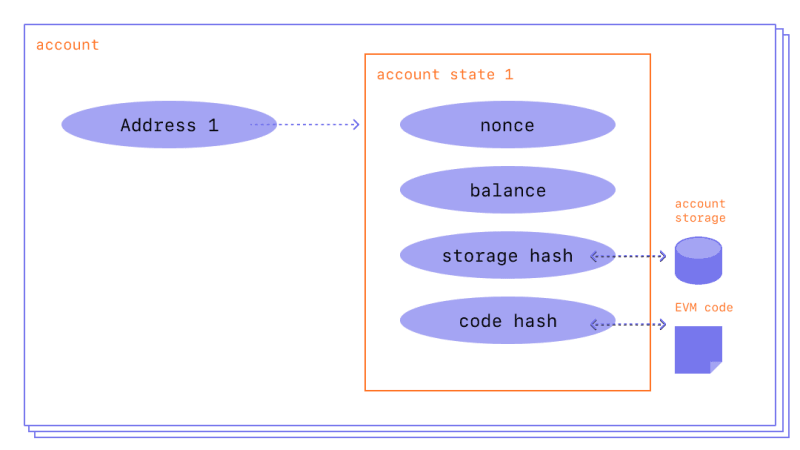
As depicted in Figure 2, each account has four fields, the nonce, balance, storage hash and code hash equal to the one from Figure 1 (the bottom right side of the figure). The code hash represents a hash of the EVM code of the account, which is executed if the address receives a message call. For EOAs this code is the hash of an empty string.[4] The code of accounts is stored in the state database. The storage root is "a 256-bit hash of the root node of a Patricia Merkle Trie that encodes the storage contents of the account". Without going into too much detail, a Merkle Tree is an efficient data structure for key-value mappings that enables fast and secure validation of given data, see Section 1.1.5 of the previous post. Its main feature is that any change in a node yields different hash values in the nodes above the changed one, including the root node. Because of this property Ethereum light clients can operate making the functioning of the network much cheaper. In addition, Ethereum stores the root hashes of three other trees, namely the World State Trie, Transaction Trie and Transaction Receipts Trie. The World State Trie is a "mapping between addresses and account states" where each leaf node represents an account state. Therefore account states, i.e. their balances, nonce values and the hashes for the storage root and code, become traceable and verifiable at any point in time. That also refers to state changes enacted by transactions as these are stored in the Transaction Receipts Trie, while the Transaction Trie is derived from the transaction list.
In the next section we will look at how such blocks are added to the blockchain.
2.2.4 Consensus Algorithms
As previously mentioned in the overview of Blockchain (see Section 1.3) the process of adding blocks to the blockchain depends on the consensus algorithm in use. These algorithms allow all nodes in the network to agree on its single state. Before September 15, 2022 Ethereum used the Proof of Work (PoW) consensus protocol Ethash, while after that date a much more efficient algorithm Proof of Stake (PoS) was merged into the network. Both algorithms will be covered in the next two sections.
Proof of Work
For PoW, nodes in a peer-to-peer network are referred to as miners. To recap, each miner builds a candidate block from pending transactions in its temporary memory pool. The miners can choose transactions they want to add into the candidate block and then start with the mining process. Mining describes the process of hashing the candidate block until a valid hash could be found. For a candidate block to be valid, the hash of the block needs to be below a certain target value. This target value adapts to the computational power existing in the network and is updated in intervals. As shown in Figure 3 a value called number used once (nonce) in the block header is changed in an iterative manner until a valid hash value is found. Due to several resistances of Keccak-256 (see Figure 5 in the post about Blockchain) mining is done by brute force, which involves changing the nonce value until the resulting hash becomes valid. The newly found valid block is propagated along the network.

This brute force technique and competition to win the reward by first announcing a new valid block requires high computational effort from all network nodes. On the one hand, it leads to immensely increased safety as well as a reduction in the likelihood of attacks such as the double spending attack in which the same currency is spent multiple times by tempering with the Blockchain. But on the other hand, massive energy consumption and slow addition of new blocks makes PoW highly inefficient and unsustainable. For this reason, Ethereum changed its consensus algorithm to Proof of Stake on September 15, 2022, known as "The Merge".[1]
Proof of Stake
With PoS, nodes are referred to as validators minting or forging blocks. Each validator stakes coins acting as a security deposit in case of the approbation of fraudulent blocks by the validator. As a result, trust is built in validators because the stakes are higher than benefits gained from approving wrong transactions. The chance of being chosen as validator increases with the amount of the staked coins. A chosen node validates transactions in the block and adds them to the blockchain for which it is rewarded with the fees of the included transactions. The fees as well as staked coins are released when a node discontinues being a validator, albeit the release is delayed in order to deduct coins if necessary.
The energy consumption of Ethereum using PoS was reduced by 99.95% and the time necessary for adding new blocks could be significantly reduced.[1] Furthermore, PoS decreases the need for high hash rates and thus the need for expensive and massive amounts of hardware. Additionally, it might yield increased decentralization as mining in pools is suspended together with the reduced necessity of expensive hardware, producing more distributed nodes that contribute to the network. While the majority of attacks are still possible, the benefit outweighs the loss of the 51% staked coins necessary, together with the possible fluctuations of the coin as a result of such an attack.
After a new block has now been added to the blockchain via PoW or PoS, it is propagated along the network to other nodes which validate it and include it into their copy of the blockchain. As stated in the Ethereum Yellow Paper and illustrated on the left side of Figure 1, the block is finalized in four stages which slightly vary depending on whether the block is mined or propagated and validated.[4] Compared to mining, where the ommers and transactions for the candidate block are determined, the reward is applied and a valid state and nonce are computed with the consensus algorithm, validation of valid blocks is done for all other nodes in the network and involves validating the ommers, transactions, applying the rewards and verifying the state and nonce of the valid block.
Next we will look at how how these states are verified.
2.2.5 Ethereum Network
The verification of the state includes running the code on the Ethereum Virtual Machine (EVM), the backbone for computing states. It is important to note, that every node goes through that step of validating and verifying new blocks. As a state machine, the EVM computes the state of the blockchain after each transaction by applying changes in the fields of accounts involved in the transaction, which allows nodes to validate and verify all state transitions including the final one. This work then repeats with choosing new transactions from the transaction pool for the next candidate block. Since we only covered the EVM briefly, please check Ethereum Virtual Machine for more information, albeit this in-depth knowledge is not required to grasp the concepts of Ethereum.[16]
Summary
This concludes our overview of Ethereum and its consensus algorithms. We explored the way state is stored in the network and how transactions are added and validated. The new Proof of Stake consensus algorithm makes Ethereum sustainable by reducing its energy consumption by 99.95% and relying on more affordable hardware.
For an overview of Blockchain, its security fundamentals and issues arising from the choice of its consesus algorithm, such as 51% attack and energy consumption, see the previous post Part 1. Blockchain.
The next post on Part 3. Smart Contracts will bring the notion of Ethereum's primary use case of the blockchain, which include contracts such as NFTs, Tokens, DeFi protocols and others.
References
- The Merge on Ethereum, https://ethereum.org/en/upgrades/merge/.
- Ethereum nodes and clients, https://ethereum.org/en/developers/docs/ nodes-and-clients.
- Chapter 4. Cryptography — Elliptic Curve Cryptography Explained, https://www.oreilly.com/library/view/mastering-ethereum/9781491971932/ch04.html.
- Ethereum Yellow Paper, https://ethereum.github.io/yellowpaper/paper.pdf.
- Functionality of smart contracts, https://www.ibm.com/topics/smart-contracts.
- The Keccak reference, https://keccak.team/files/Keccak-reference-3.0.pdf.
- The Keccak SHA-3 submission, https://keccak.team/files/Keccak-submission-3.pdf.
- Merkle Tree, https://soliditydeveloper.com/merkle-tree/.
- Blogpost of Vitalik Buterin — Merkling in Ethereum, https://blog.ethereum.org/2015/11/15/merkling-in-ethereum.
- NFT Metadata, https://www.weforum.org/agenda/2022/02/non-fungible-tokens-nfts-and-copyright/.
- Reentrancy attack in a Solidity smart contract, https://cryptomarketpool.com/reentrancy-attack-in-a-solidity-smart-contract/.
- ERC Token Standards - The Ultimate List, https://www.blockchain-council.org/ethereum/erc-token-standards/.
- Why Does Bitcoin Use So Much Energy? https://www.forbes.com/advisor/ca/investing/cryptocurrency/bitcoins-energy-usage-explained/.
- ERC-721 Non-Fungible Token Standard, https://ethereum.org/en/developers/docs/standards/tokens/erc-721/.
- Ethereum block architecture, https://ethereum.stackexchange.com/questions/268/ethereum-block-architecture.
- Ethereum Virtual Machine, https://ethereum.org/en/developers/docs/evm/.
- Ethereum Wallets, https://ethereum.org/en/wallets/.
- Cryptographic Hashes and Bitcoin, https://freecontent.manning.com/cryptographic-hashes-and-bitcoin/.
- Private and public keys on Ethereum, https://www.massmux.com/private-and-public-keys-on-ethereum/.
- What Is Sleepminting And Will It Ruin NFT Provenance? https://timdaub.github.io/2021/04/22/nft-sleepminting-beeple-provenance/.
- Pentagon finds concerning vulnerabilities on blockchain, https://www.techrepublic.com/article/pentagon-finds-concerning-vulnerabilities-on-blockchain/.
- A. M. Antonopoulos and G. Wood. Mastering Ethereum: Building Smart Contracts and DApps. O’Reilly Media, 2018.



Top comments (2)
this is very useful!
Thank you! You can also check the other two posts in this 101 crash course