Why HIPAA Compliance Matters in WPF Medical Apps
HIPAA Compliance in WPF Apps is crucial, as WPF (.NET) medical applications have a critical responsibility to protect Protected Health Information (PHI) from unauthorized access. Any security failure can expose sensitive medical data, leading to privacy violations and severe penalties for non-compliance with the Health Insurance Portability and Accountability Act (HIPAA).
The Importance of Protecting PHI in .NET Applications
Medical applications store and process highly sensitive information, including electronic health records (EHRs), diagnoses, prescriptions, and medical images. If compromised, this data can be exploited for fraud, medical identity theft, or even the malicious alteration of patient records.
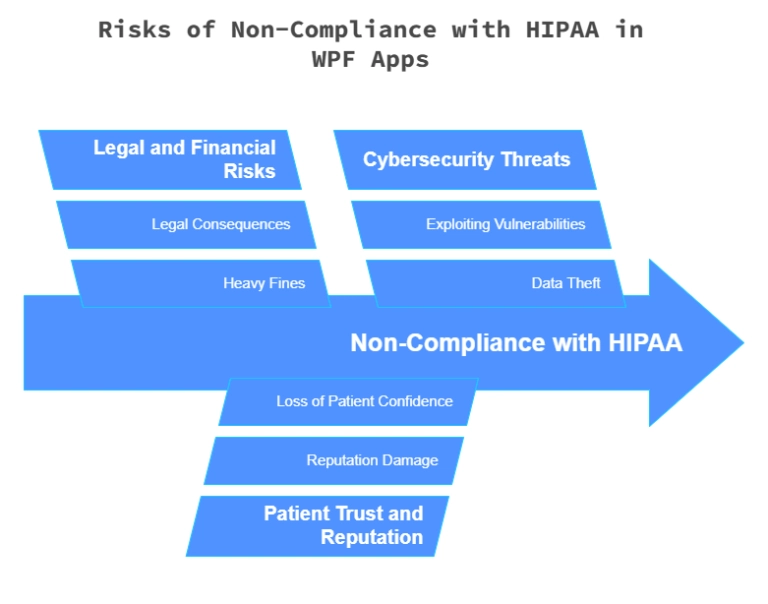
Why Do WPF Apps Handling PHI Need HIPAA Compliance?
- Legal and financial risks: HIPAA regulations impose strict security requirements on any application handling PHI. Non-compliance can lead to heavy fines and legal consequences.
- Patient trust and reputation: A data breach can damage a healthcare provider’s reputation and result in loss of patient confidence.
- Cybersecurity threats: Without proper safeguards, attackers can exploit vulnerabilities in the application to steal or manipulate medical records.
How Jailbroken Devices Compromise Medical App Security
What Is a Jailbroken or Rooted Device, and Why Is It a Threat?
A jailbroken (iOS) or rooted (Android) device is a smartphone, tablet, or computer that has been modified to bypass manufacturer security restrictions. While some users jailbreak their devices for customization, this process also disables key security mechanisms, exposing the system to threats.
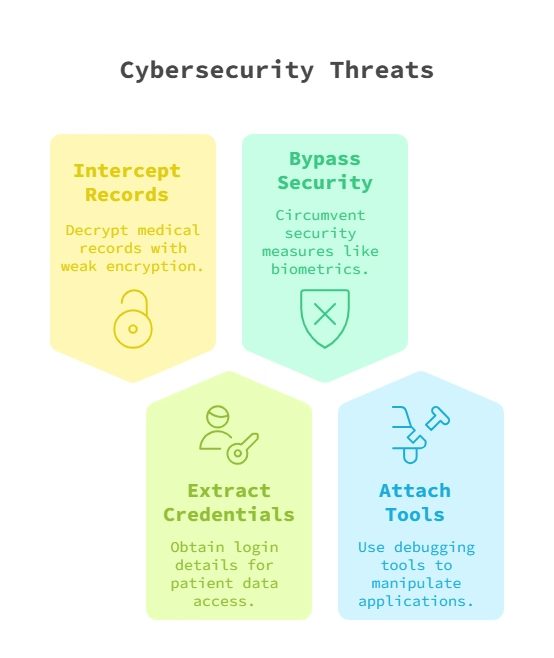
How Attackers Can Extract PHI from Unprotected Applications
When a WPF medical application runs on a jailbroken or rooted device, attackers can exploit vulnerabilities to:
- Intercept and decrypt stored medical records if encryption is weak or improperly implemented.
- Extract login credentials and session tokens to access patient data.
- Bypass security features such as biometric authentication or PIN verification.
- Attach debugging tools to analyze and manipulate the application’s behavior.
Preventing Compliance Risks: Detecting and Auto-Deleting PHI on Jailbroken Devices
Since HIPAA mandates strict data protection, allowing a medical application to run on a compromised device creates a major compliance risk. To prevent this, WPF developers need mechanisms to detect jailbroken devices and automatically delete PHI before it can be accessed.
Understanding Runtime Threat Detection in WPF Apps
Ensuring HIPAA compliance in WPF medical applications goes beyond encryption and access control. A critical aspect is real-time threat detection to prevent unauthorized access to Protected Health Information (PHI). Attackers often use debuggers, emulators, or jailbroken devices to extract sensitive data, bypass security controls, and manipulate application behavior.
The Role of RASP (Runtime Application Self-Protection) in HIPAA Compliance
How RASP Helps Secure WPF Medical Applications
Runtime Application Self-Protection (RASP) is a security mechanism that monitors an application in real-time to detect and block potential threats. Unlike traditional security tools that focus on network traffic or system monitoring, RASP works inside the application to ensure immediate response to security breaches.
- Detects unauthorized modifications: Identifies debuggers, memory tampering, and jailbroken devices attempting to manipulate app behavior.
- Prevents data leaks: Automatically erases PHI or disables sensitive functionality when a security risk is detected.
- Ensures HIPAA compliance: Proactively protects patient data from real-world security threats, reducing the risk of violations.
Example: Real-World Application of RASP in WPF Medical Apps
Protecting PHI in WPF Medical Apps with RASP
A WPF medical app used by hospitals for managing patient prescriptions is running on a compromised device where an attacker is using a debugger to extract PHI. With RASP protection, the application can:
✔ Detect the unauthorized debugger.
✔ Automatically wipe stored PHI from the device.
✔ Log the security event for compliance audits.
✔ Notify system administrators of the breach.
This prevents unauthorized data access while maintaining HIPAA compliance.
Detecting Debuggers and Jailbreaks in .NET Medical Apps
Attackers rely on debugging tools, reverse engineering techniques, and jailbroken/rooted environments to bypass application security and extract medical data. Detecting these threats in real-time is essential to prevent data breaches.
Common Techniques for Identifying Debuggers and Modified Environments
Detecting Debugging Tools
- Using
Debugger.IsAttachedto check if a debugger is connected. - Monitoring system APIs for debugging-related behavior.
Identifying Jailbroken or Rooted Devices
- Checking for modified system files indicating an altered OS.
- Detecting jailbreak tools commonly used by attackers.
Preventing Memory Tampering
- Scanning memory regions for unauthorized modifications.
- Verifying the integrity of stored PHI.
Why Stopping Execution Is Not Enough – The Need for Automated PHI Deletion
Simply terminating the application when a security threat is detected is not sufficient for HIPAA compliance. If PHI remains stored on the device, attackers can still access it later. To fully protect patient data, the app must automatically delete PHI as soon as a security breach is detected.
🔹 Example: Implementing Automatic PHI Deletion in WPF
A WPF hospital management app detects that it is running on a jailbroken device. Instead of simply closing, it:
✔ Overwrites PHI with random data to prevent recovery.
✔ Deletes all cached medical records from local storage.
✔ Logs the security event for compliance and auditing.
This approach ensures that PHI remains protected at all times, even if the device is compromised.
Implementing Auto-Deletion of PHI with ByteHide Monitor
Setting Up ByteHide Monitor in a WPF Medical App
To integrate ByteHide Monitor into a WPF medical application, follow these steps:
- Install ByteHide Monitor via NuGet: Open the NuGet Package Manager in Visual Studio and run:
Install-Package Bytehide.Monitor
Initialize ByteHide Monitor in Your Application
Add the following code in your App.xaml.cs or main entry point:
var monitor = new MonitorManager("<your_project_token>");
monitor.Start();
Configure Detection Rules
Use ByteHide Monitor to detect jailbreaks, debugging tools, or reverse engineering attempts:
monitor
.On(DebuggerDetection.Enabled)
.On(JailbreakDetection.Enabled)
.React(() =>
{
// Define what happens when a security threat is detected
Console.WriteLine("Security Threat Detected!");
});
Automating PHI Wipeout on Security Threats
When an unauthorized modification is detected, sensitive medical data should be wiped immediately. ByteHide Monitor allows automatic data deletion upon security events.
Configure Auto-Delete Rules:
monitor.React(() =>
{
// Securely erase PHI stored in the application
SecureDataWipeout();
Console.WriteLine("PHI wiped due to security risk.");
});
Example: Removing Patient Data from Storage
private void SecureDataWipeout()
{
// Delete patient records stored locally
if (File.Exists("patient_data.json"))
{
File.Delete("patient_data.json");
}
// Clear sensitive memory locations (Example)
GC.Collect();
GC.WaitForPendingFinalizers();
}
Logging and Auditing Security Events
Tracking security incidents is critical for HIPAA compliance, but logs must not expose PHI.
Use ByteHide Logs for Security Tracking:
var logs = new LogsManager("<your_logs_token>");
logs.RecordEvent("Security Incident", "Debugger detected, PHI wiped");
Ensuring Log Security and Compliance
Ensure Logs Do Not Contain Sensitive Patient Information
Only store metadata about security events, not actual medical data.
Compliance Best Practices for Secure WPF Medical Apps
Aligning with HIPAA Security & Privacy Rules
Ensuring HIPAA compliance in a WPF medical application requires a combination of encryption, access control, logging, and real-time monitoring. These measures protect Protected Health Information (PHI) and help prevent unauthorized access.
- Encryption: All PHI must be stored and transmitted securely. Using AES-256 or quantum-resistant encryption ensures that sensitive medical data remains unreadable to unauthorized users.
- Access Control: Implement role-based access control (RBAC) to restrict PHI access based on user roles. This prevents unauthorized personnel from retrieving sensitive records.
- Logging and Auditing: HIPAA requires maintaining an audit trail of all access attempts and security incidents. However, logs must not contain PHI. ByteHide Logs can be used to record security events while ensuring compliance.
- Real-Time Threat Detection: Using ByteHide Monitor to detect debuggers, jailbreaks, and suspicious activities helps prevent PHI breaches before they occur.
Example: Applying Encryption in a WPF Medical App
var storage = new StorageManager();
var encryptedData = storage
.Encrypt()
.Set("patient_records.json", patientData);
Enhancing Security with Multi-Layered Protection
A multi-layered security strategy is essential for HIPAA compliance, as relying on a single protection method is not enough. Combining ByteHide Monitor with other security solutions strengthens protection against attacks, reverse engineering, and unauthorized access.
- ByteHide Monitor (RASP Protection): Detects debuggers, jailbreaks, and tampering in real-time, triggering immediate security actions such as data deletion.
- ByteHide Shield (Code Obfuscation): Prevents attackers from reverse engineering the application by making the code unreadable and difficult to manipulate.
- ByteHide Secrets (Secrets Management): Ensures secure storage of API keys, encryption keys, and authentication credentials, preventing exposure in the application’s source code.
Example: Combining Monitor and Shield for Enhanced Security
var monitor = new MonitorManager("<your_project_token>");
monitor
.On(DebuggerDetection.Enabled)
.React(() =>
{
Console.WriteLine("Debugger detected! Terminating app.");
Environment.Exit(0);
});
// Shield protects the application's code from tampering
var shield = new ShieldManager();
shield.ApplyObfuscation();
Final Thoughts: Future-Proofing WPF Medical Apps for HIPAA Compliance
Building HIPAA-compliant WPF medical applications goes beyond just encrypting data or setting up access controls. Threat detection and automated PHI deletion are essential for preventing security breaches, especially in environments where jailbroken or compromised devices could put patient data at risk.
With ByteHide Monitor, developers can detect real-time threats, trigger instant security actions, and ensure that PHI is never exposed in an unsafe environment. By integrating automated data deletion when risks are detected, healthcare apps can prevent unauthorized access before it happens, keeping patient records secure.
Next Steps for Securing Your WPF Healthcare Application
- ✅ Implement ByteHide Monitor to detect and respond to security threats dynamically.
- 🔒 Integrate encryption and access control to ensure PHI is only accessible to authorized users.
- 📊 Leverage ByteHide Logs for compliance-friendly security auditing, tracking unauthorized access attempts without exposing sensitive data.
- 🛡 Combine multiple security layers (Shield for code obfuscation, Secrets for secure key management) to strengthen application protection.
As healthcare data security regulations evolve, staying ahead of compliance requirements is key. By adopting proactive threat detection and automated security measures, developers can future-proof their WPF medical apps, ensuring that patient data remains protected at all times.



Top comments (0)