In this comprehensive guide, we’ll walk through the process of setting up a Pritunl VPN server on Ubuntu 22.04 instance. We’ll then integrate the Pritunl server logs with Filebeat, Elasticsearch, and Kibana to visualize and monitor VPN activities and set up alerts for specific events.
What is Pritunl Server?
Pritunl Server is an open-source VPN server that's easy to set up and manage through a web-based interface. It supports various authentication methods, offers scalability for large deployments, and works on multiple platforms. Key features include security with two-factor authentication, high availability configurations, and built-in logging and monitoring. It's a user-friendly solution for setting up VPNs in businesses and enterprises.
Benefits of the Pritunl server over VPN:
- Simplicity: Using the web interface or command line, you can easily install and configure Pritunl VPN on your server. You can also connect to VPN networks using the free and cross-platform Pritunl client or any other client supporting OpenVPN.
- Security: You can be sure that your traffic is protected by strong encryption and authentication using OpenVPN standards and protocols.
- Openness: You can use Pritunl VPN for free.
- Integration: Using API and webhooks, you can integrate Pritunl VPN with other applications and platforms. For example, you can integrate Pritunl VPN with your Identity Management System (IAM), such as Active Directory, LDAP, or SAML.
Deploying Pritunl Server
1. Launch EC2 Instance and Private Server
- Launch an Ubuntu 22.04 instance and one private instance within the same VPC.
2. Create Installation Script for Pritunl
- Create a bash script named install_pritunl.sh with the following content to set up Pritunl and MongoDB: ```
!/bin/bash
Add Pritunl repository
sudo tee /etc/apt/sources.list.d/pritunl.list << EOF
deb http://repo.pritunl.com/stable/apt jammy main
EOF
Import Pritunl signing key
sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com --recv 7568D9BB55FF9E5287D586017AE645C0CF8E292A
Update package repository
sudo apt update
Install WireGuard and Pritunl
sudo apt -y install wireguard wireguard-tools
sudo apt -y install pritunl mongodb-org
Enable and start services
sudo systemctl enable mongod pritunl
sudo systemctl start mongod pritunl
- Run the script:
`. ./install_pritunl.sh`
**_3. Configure Pritunl Server_**
- Access the Pritunl web interface using the public IP over HTTPS.
- Sign up
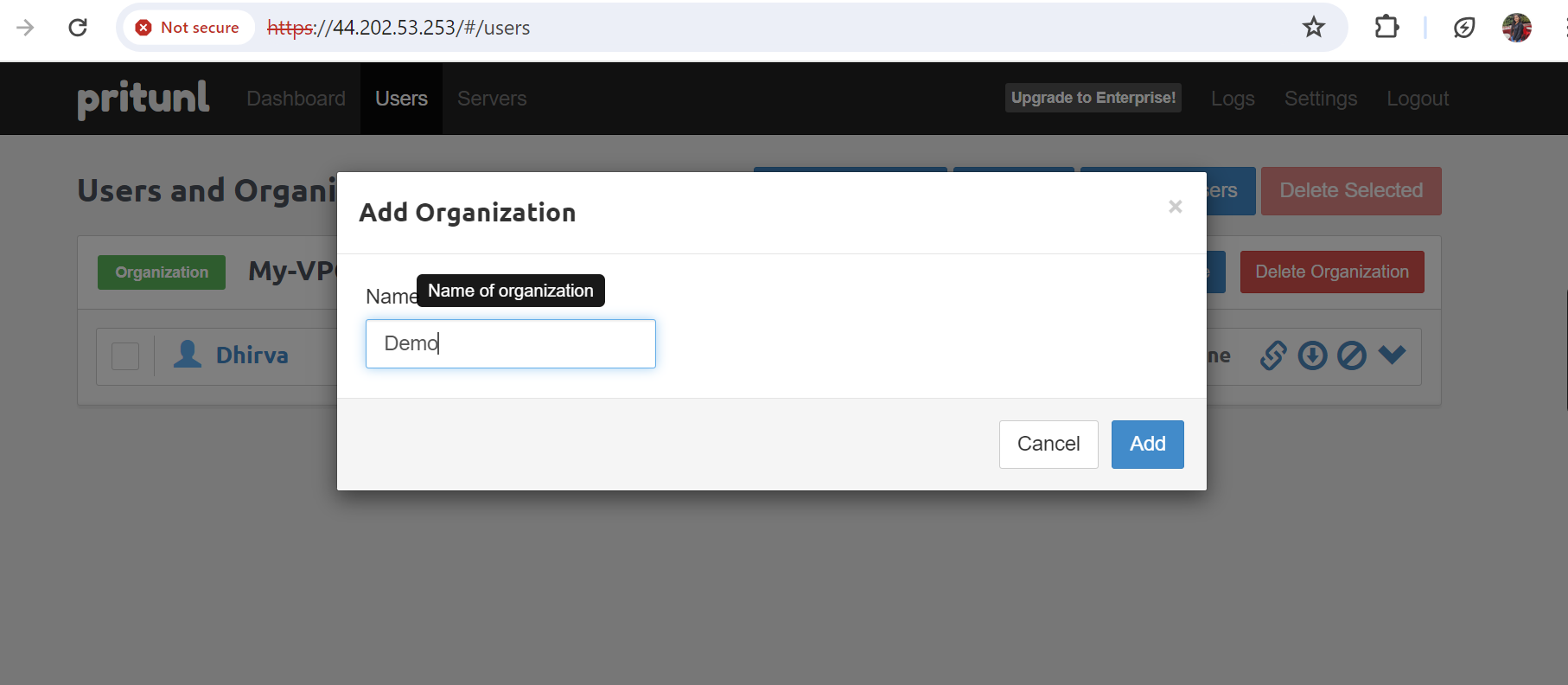
- Create organization
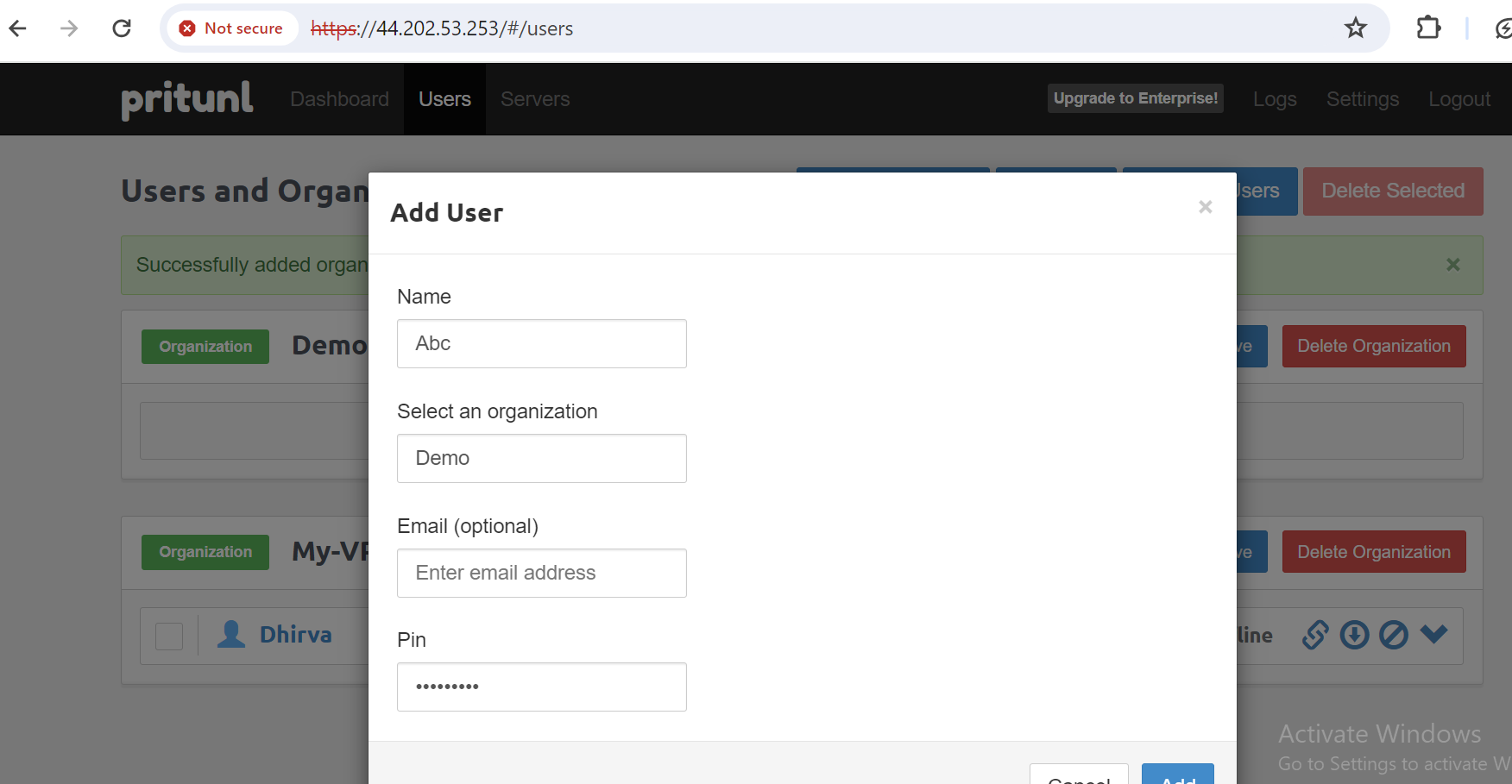
- Create a user inside the organization that you created
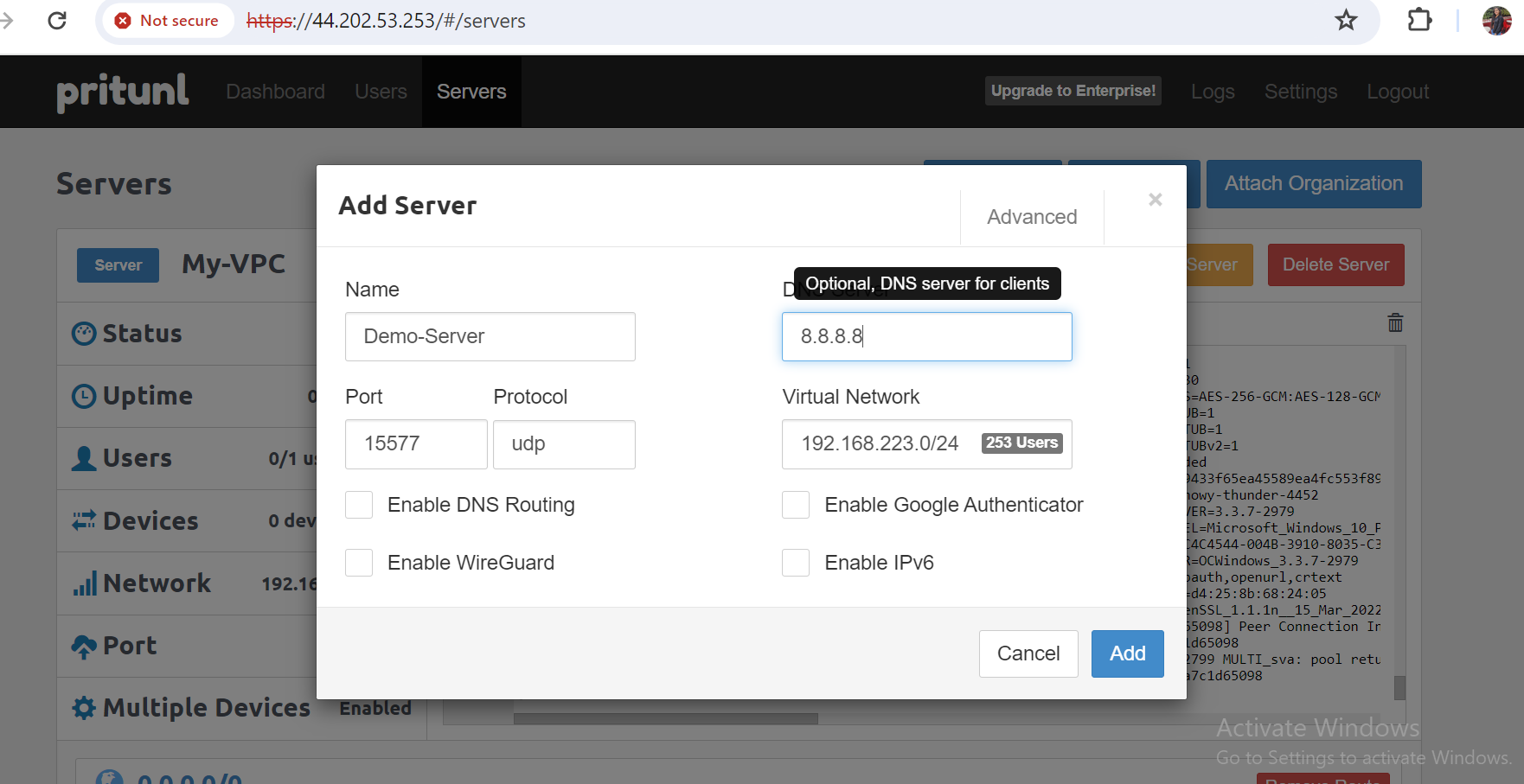
- Add a server
- Attach the server to the organization that you created
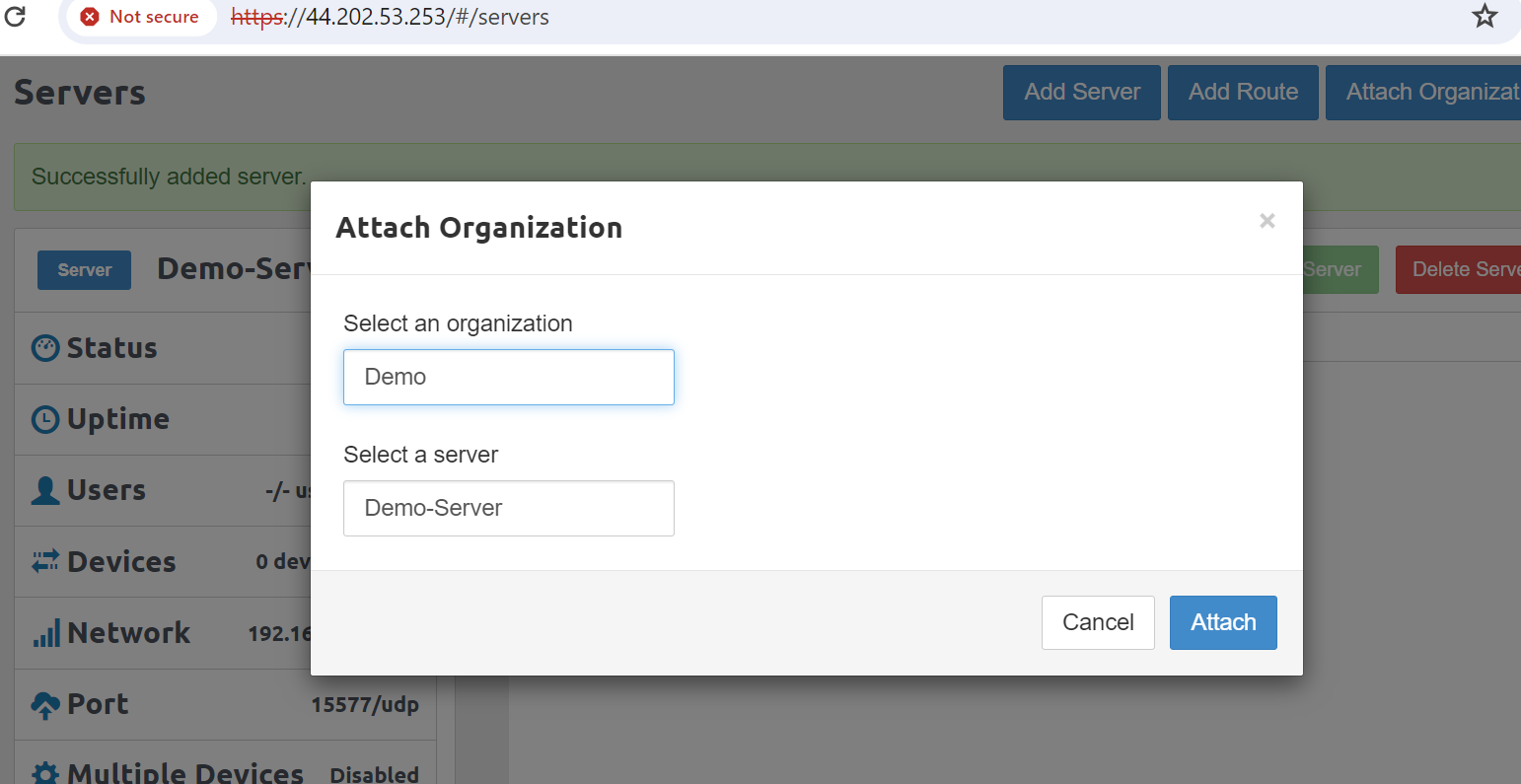
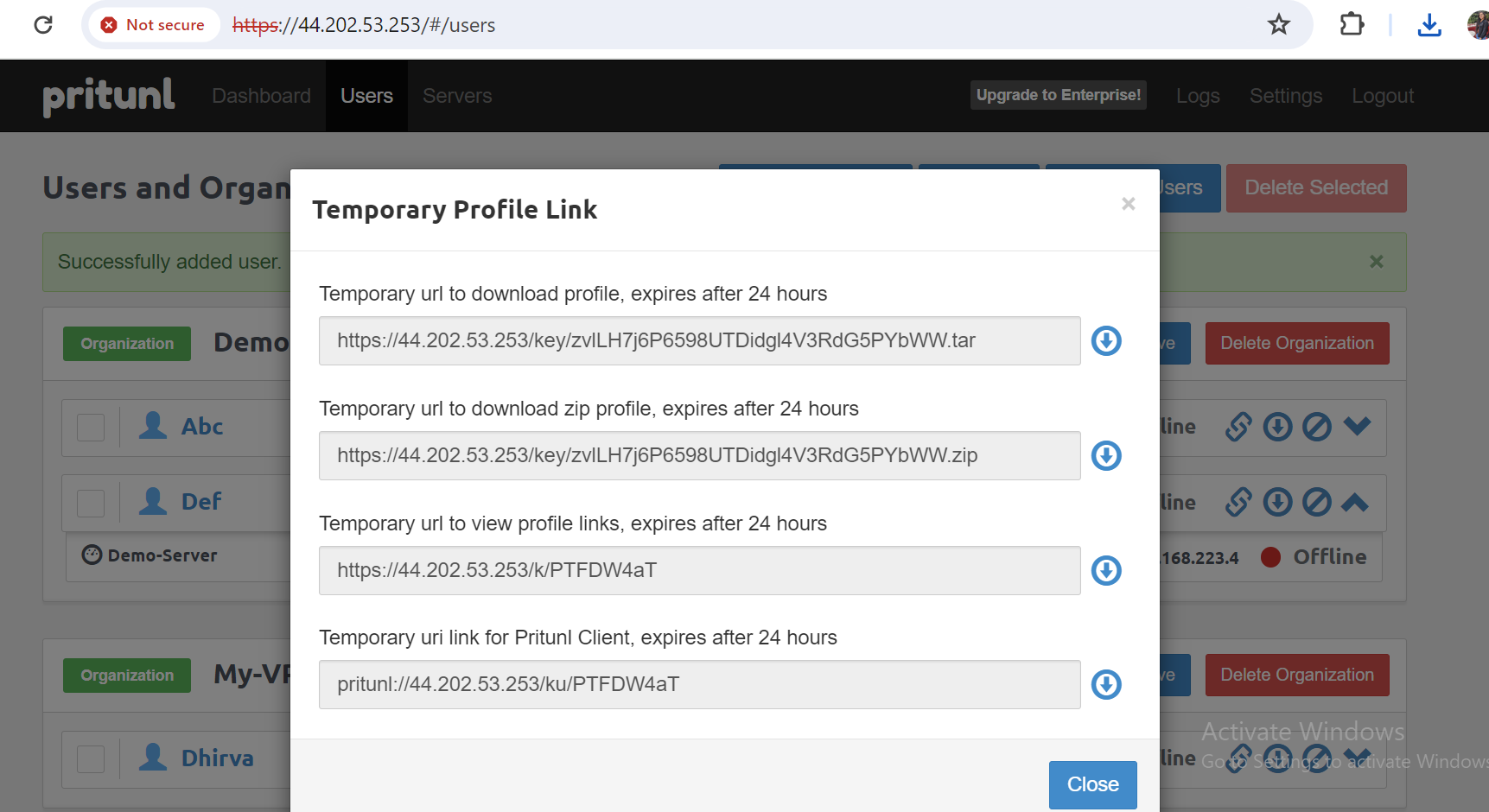
- Download the user's profile by going to the temporary profile link and download the zip file. Unzip that ovpn file.
- Download OpenVPN if not present
- Inside OpenVPN add the user's profile and connect to the Pritunl server. Add username and password of pritunl login . Add a response pin which is set when we create a user.
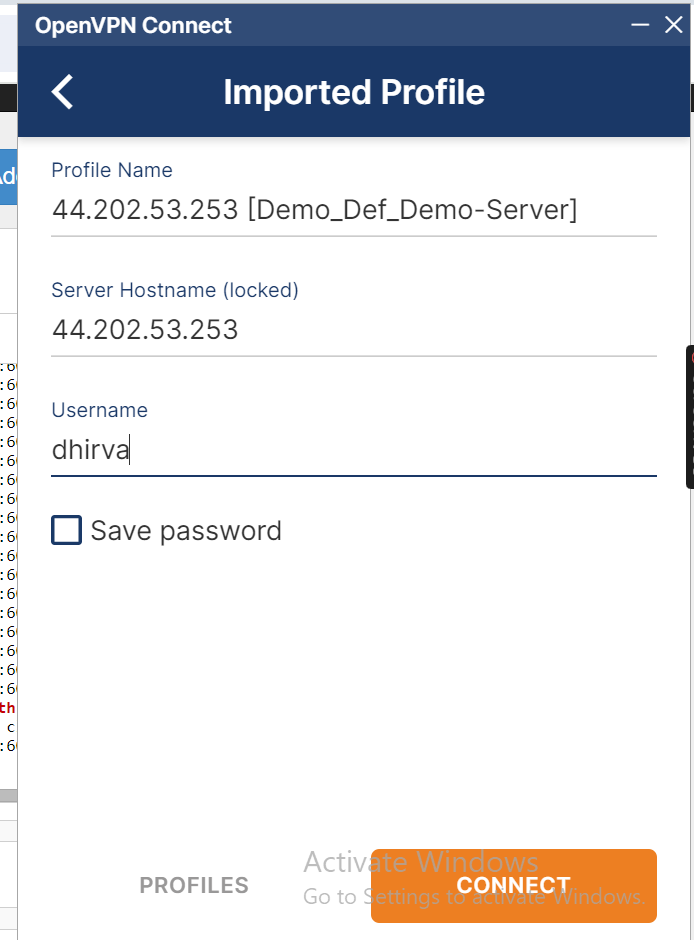
- Successfully connected to the Pritunl VPN.
- Now we will test whether we can connect(SSH) our private server which is in the same VPC network when we are connected to pritunl VPN.
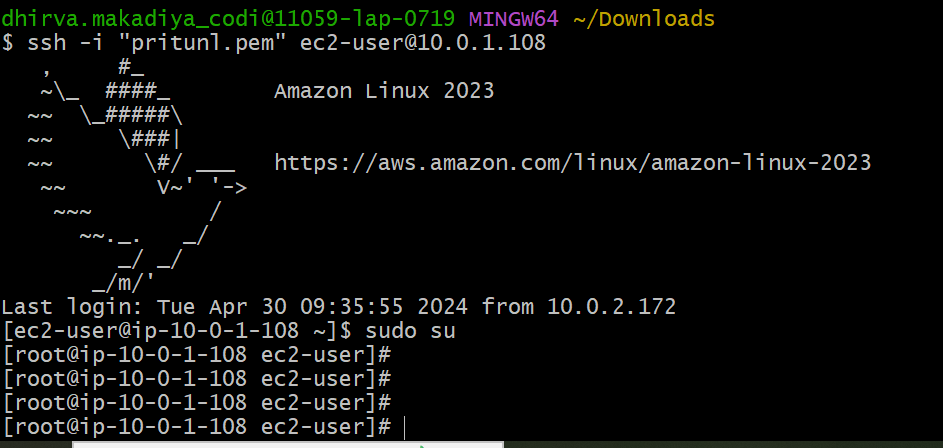
We can successfully SSH to our private server if they are in the same network and connected to our Pritunl VPN server.
## **Integrating Pritunl Logs with Elasticsearch and Kibana using Filebeat.**
**_1. Install Elasticsearch_**
- Install and configure Elasticsearch for log storage:
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo apt-key add -
sudo apt-get install apt-transport-https
echo "deb https://artifacts.elastic.co/packages/8.x/apt stable main" | sudo tee /etc/apt/sources.list.d/elastic-8.x.list
sudo apt-get update
sudo apt-get install elasticsearch
_**2. Configure Elasticsearch**_
- Edit /etc/elasticsearch/elasticsearch.yml with the following settings:
cluster.name: my-application
node.name: node-1
path.data: /var/lib/elasticsearch
path.logs: /var/log/elasticsearch
network.host: localhost
http.port: 9200
discovery.seed_hosts: ["127.0.0.1"]
xpack.security.enabled: false
- Start Elasticsearch service:
sudo systemctl enable elasticsearch.service
sudo systemctl start elasticsearch.service
- Access Elasticsearch at _http://public-ip-address:9200_
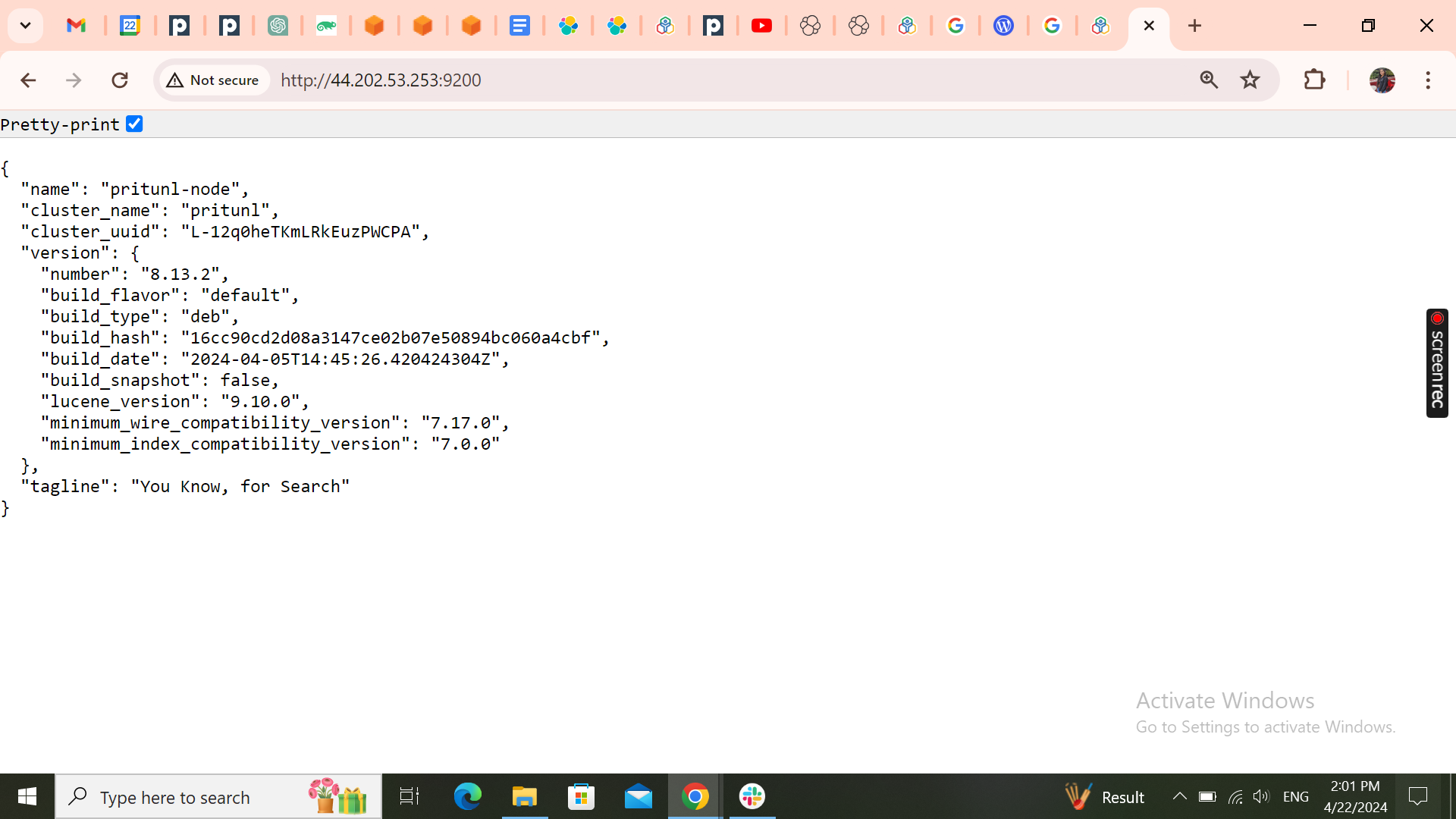
**_3. Install and Configure Filebeat_**
- Install and configure Filebeat to ship logs to Elasticsearch:
curl -L -O https://artifacts.elastic.co/downloads/beats/filebeat/filebeat-8.0.0-amd64.deb
sudo dpkg -i filebeat-8.0.0-amd64.deb
sudo nano /etc/filebeat/filebeat.yml
- Example filebeat.yml configuration:
filebeat.inputs:
- type: log
paths:
- /var/log/pritunl.log
output.elasticsearch:
hosts: ["localhost:9200"]
username: "your_username"
password: "your_password"
- Start and enable Filebeat:
sudo systemctl enable filebeat
sudo systemctl start filebeat
**_4. Install and Configure Kibana_**
- Install and configure Kibana for log visualization:
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo apt-key add -
sudo apt-get install apt-transport-https
echo "deb https://artifacts.elastic.co/packages/7.x/apt stable main" | sudo tee -a /etc/apt/sources.list.d/elastic-7.x.list
sudo apt-get update
sudo apt-get install kibana
sudo nano /etc/kibana/kibana.yml
- Example kibana.yml configuration:
server.port: 5601
server.host: 0.0.0.0
elasticsearch.hosts: ["http://localhost:9200"]
- Start and enable Kibana:
sudo systemctl enable kibana
sudo systemctl start kibana
**_5. Setting Up Alerts in Kibana_**
- Access Kibana at http://public-ip-address:5601.
- Navigate to Discover and configure the message and timestamp fields.
- In Observability, go to Alerts > Manage Rules.
- Create a new rule with conditions based on Pritunl logs (e.g., Authenticating user).
- We will create a rule that whenever a user connects to our Pritunl VPN server we should get an alert.
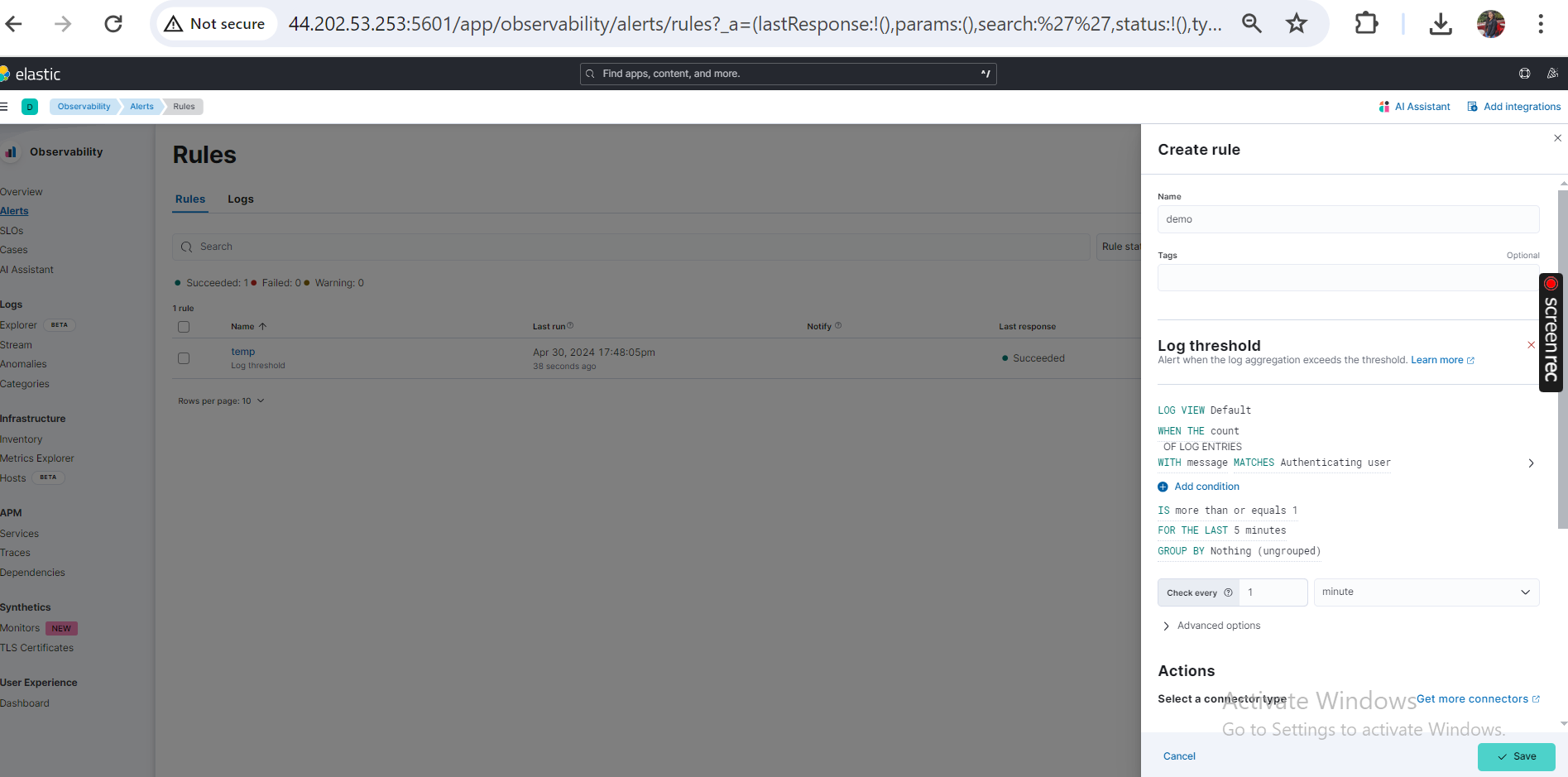
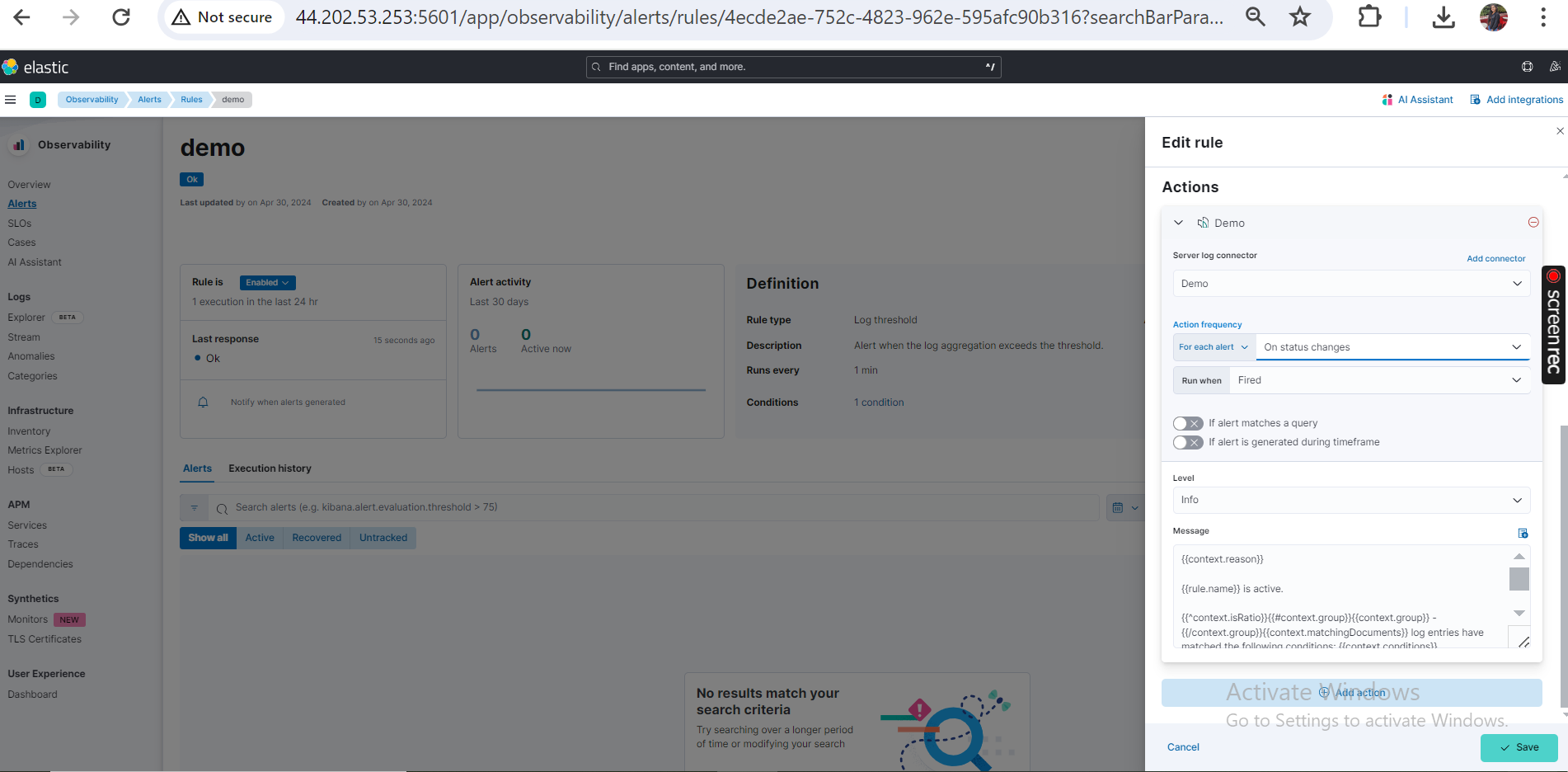
- Add actions to activate alerts (e.g., add server log)
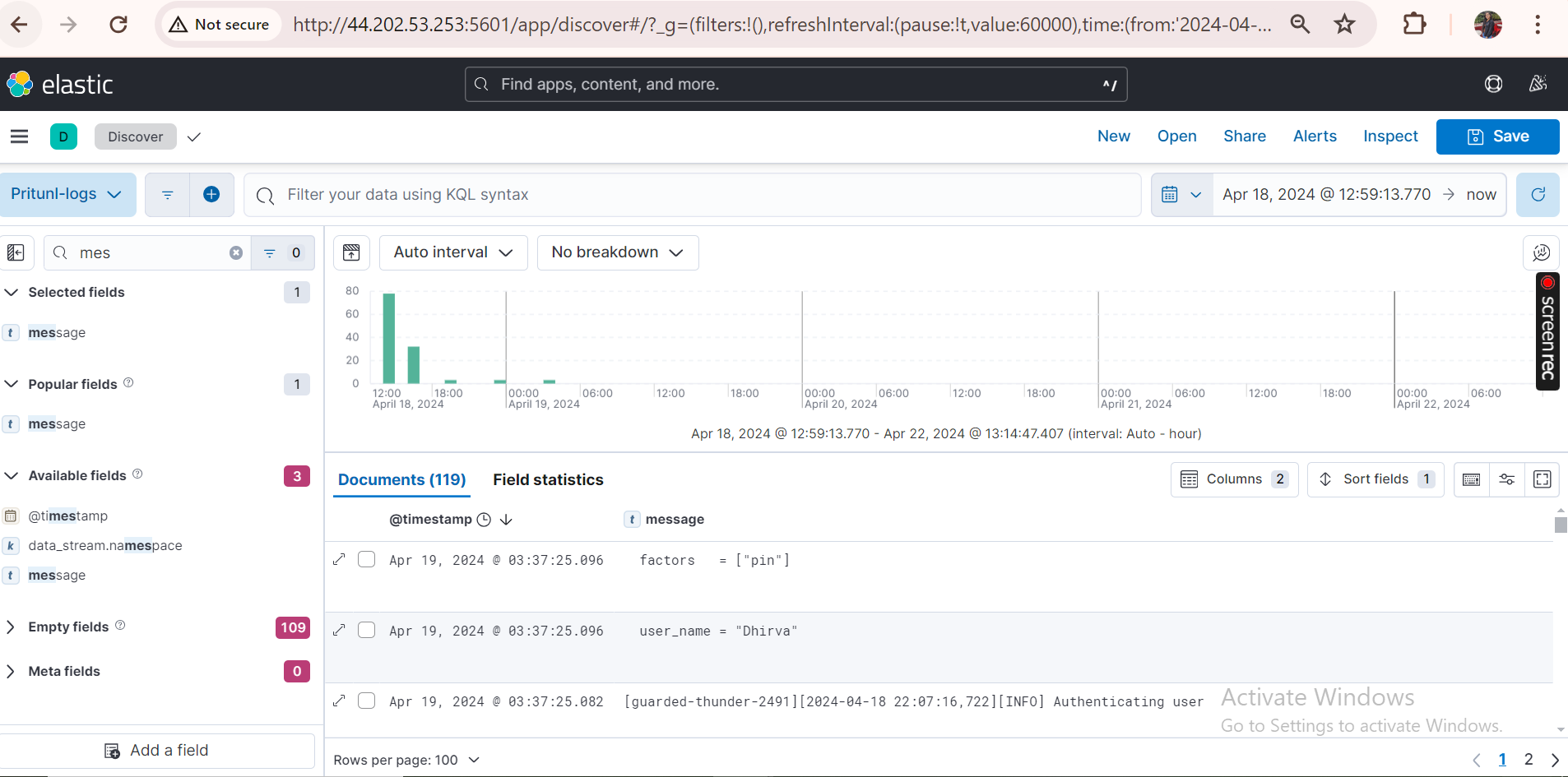
- Logs dashboard and Triggered alerts
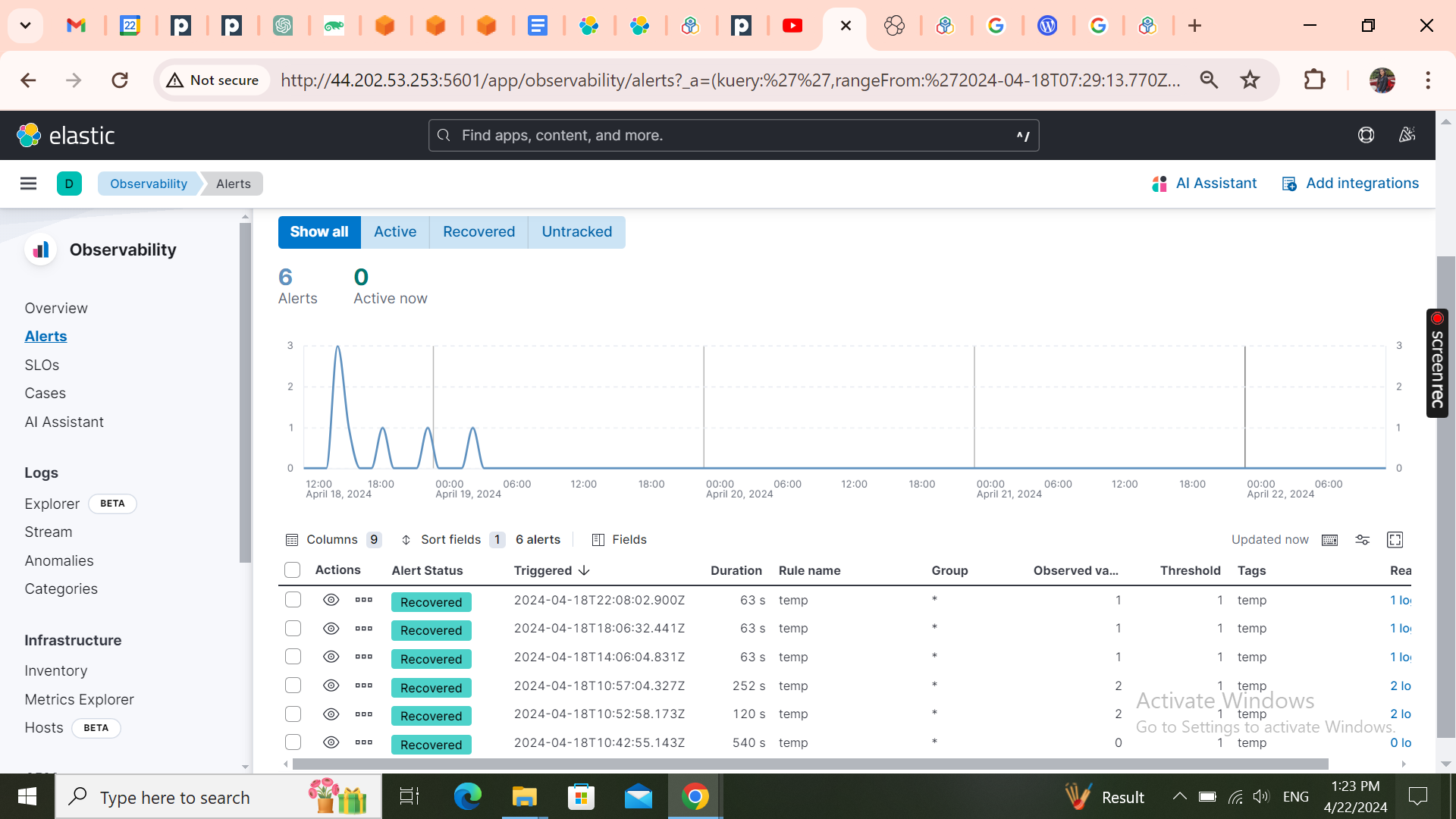
## **Conclusion**
> We have successfully set up a Pritunl VPN server, integrated its logs with Filebeat and Elasticsearch, and configured alerts in Kibana. This setup provides comprehensive visibility into VPN activities and enables proactive monitoring through real-time alerts.
Happy monitoring and secure VPN access!


Top comments (0)