Setting up a Virtual Private Cloud (VPC) is foundational when deploying resources in AWS securely. This guide walks you through creating:
- A VPC
- Public & Private Subnets
- Internet Gateway
- NAT Gateway
- Route Tables
- Optional EC2 Instances
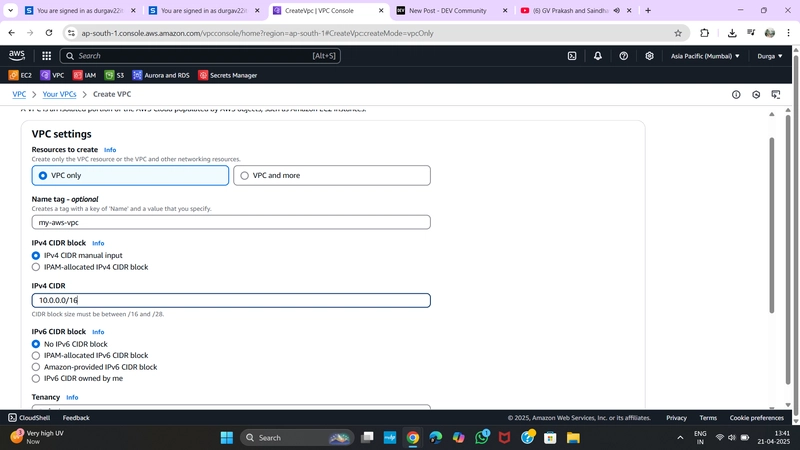
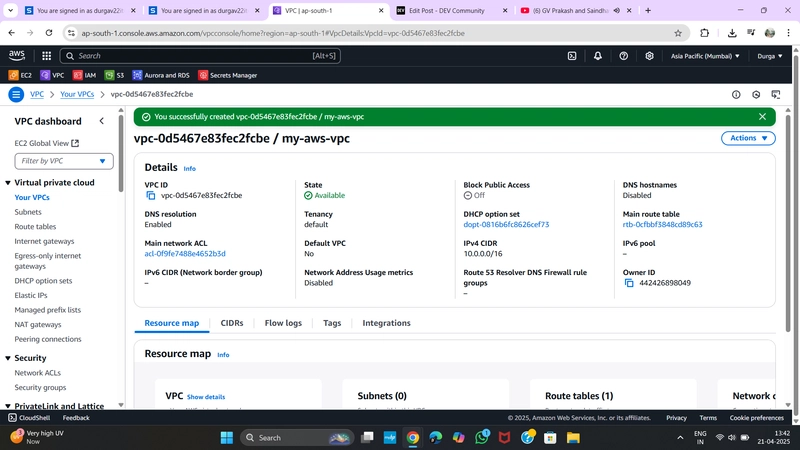
✅ 1. Create a VPC
- Go to VPC Dashboard > Your VPCs > Create VPC
- Choose VPC only
- Name:
MyVPC - IPv4 CIDR block:
10.0.0.0/16 - Leave other fields as default
- Click Create VPC
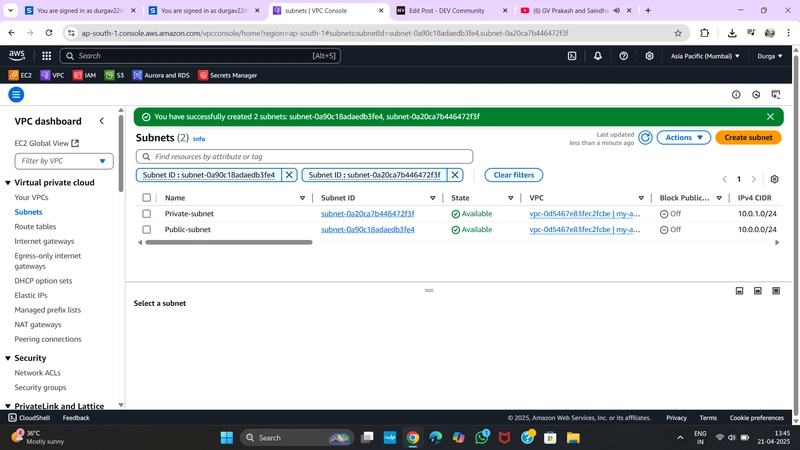
✅ 2. Create Subnets
Navigate to Subnets > Create Subnet
➤ Public Subnet:
- Name:
PublicSubnet - VPC:
MyVPC - AZ:
ap-south-1a - CIDR block:
10.0.1.0/24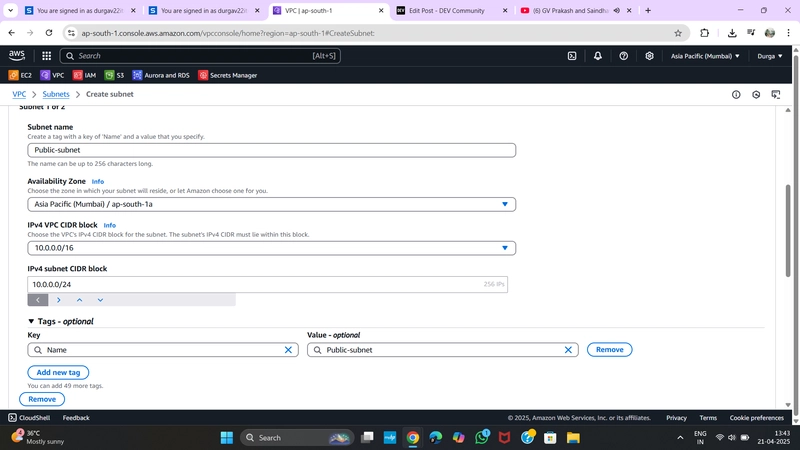
➤ Private Subnet:
- Name:
PrivateSubnet - VPC:
MyVPC - AZ:
ap-south-1b - CIDR block:
10.0.2.0/24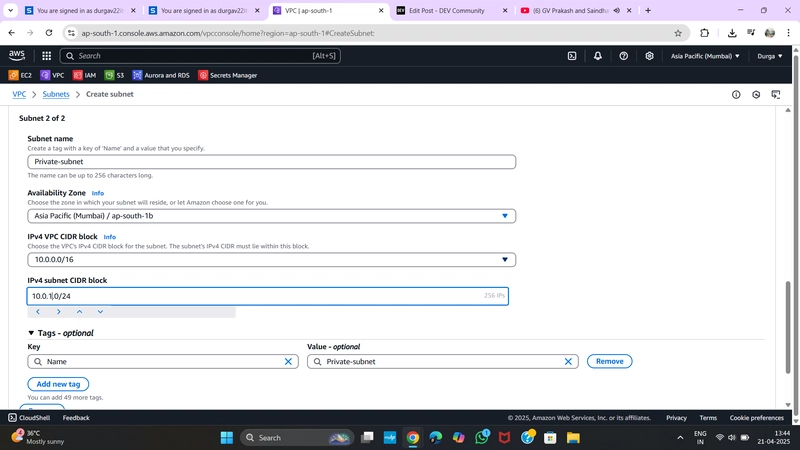
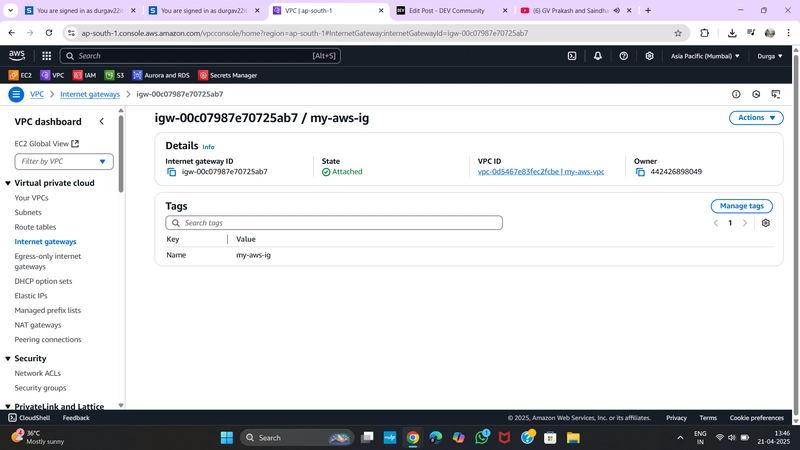
✅ 3. Create and Attach Internet Gateway
- Go to Internet Gateways > Create Internet Gateway
- Name:
MyIGW
- Name:
- Click Attach to VPC and select
MyVPC
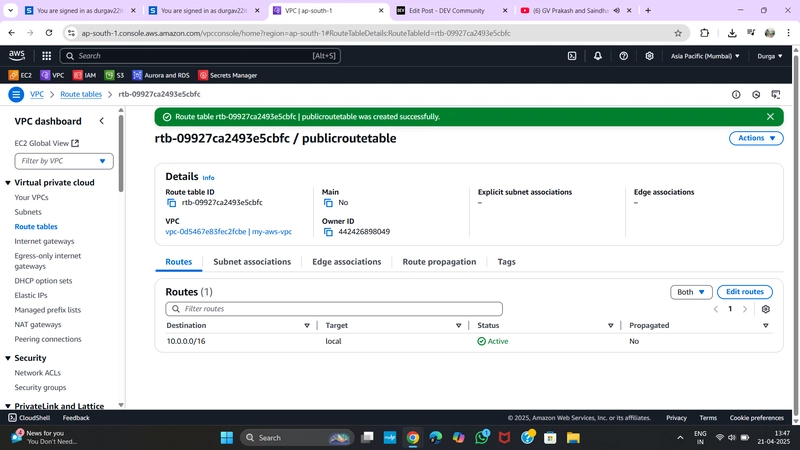
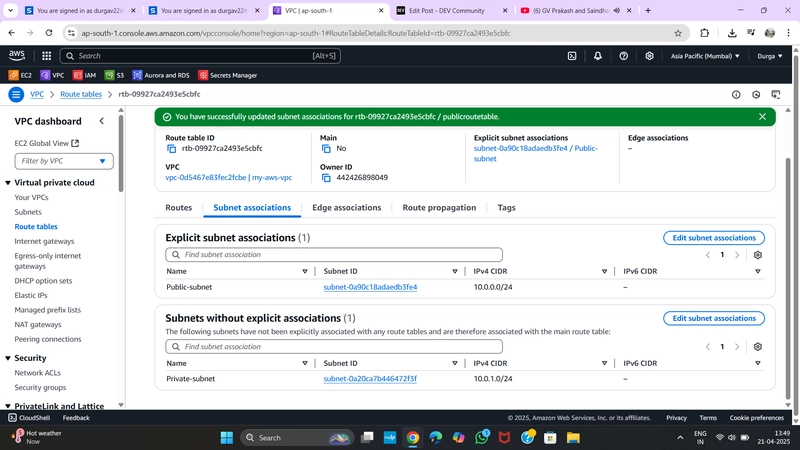
✅ 4. Create a Public Route Table
-
Go to Route Tables > Create Route Table
- Name:
PublicRT - VPC:
MyVPC
- Name:
-
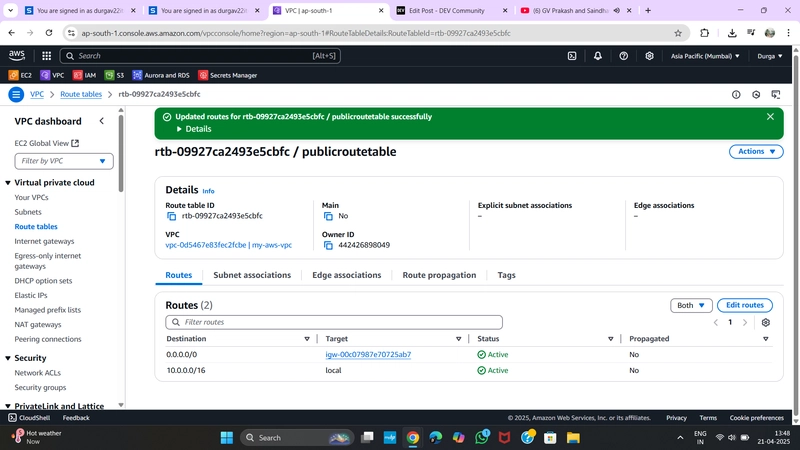
Select
PublicRT> Routes > Edit Routes- Add route:
- Destination:
0.0.0.0/0 - Target: Internet Gateway →
MyIGW
- Destination:
- Add route:
- Go to Subnet Associations > Edit Subnet Associations
- Select:
PublicSubnet
- Select:
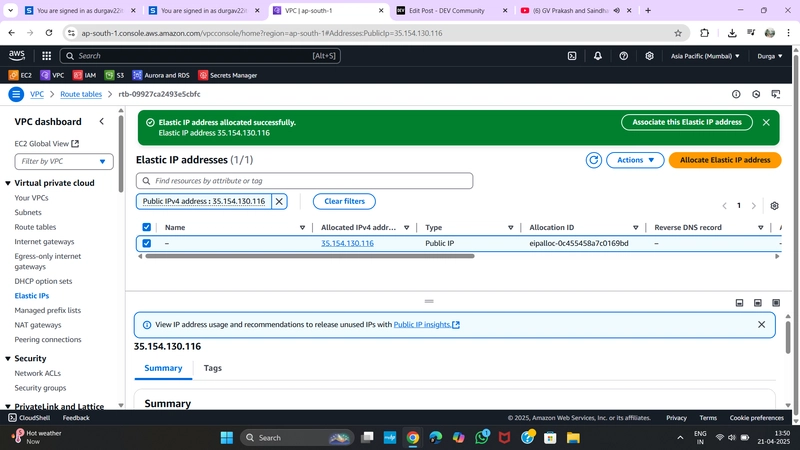
✅ 5. Allocate Elastic IP (EIP)
- Go to Elastic IPs > Allocate Elastic IP
- Note the allocation ID
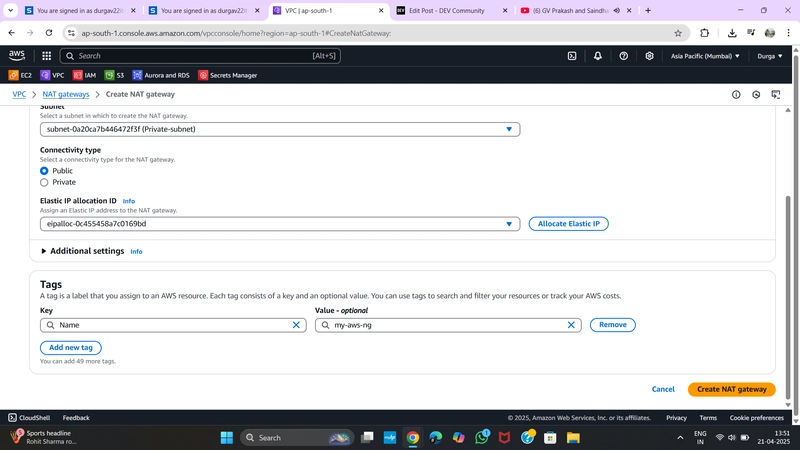
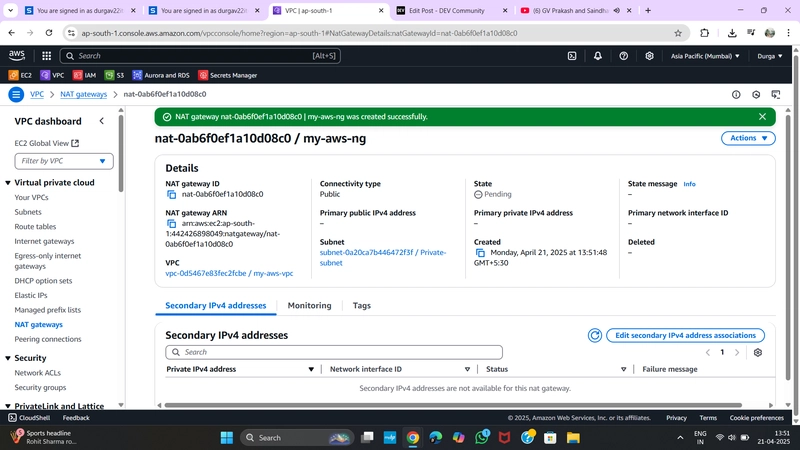
✅ 6. Create NAT Gateway
- Go to NAT Gateways > Create NAT Gateway
- Name:
MyNATGW - Subnet:
PublicSubnet - Elastic IP: select the one you just allocated
- Name:
⏳ Wait a few minutes for the NAT Gateway to become active.
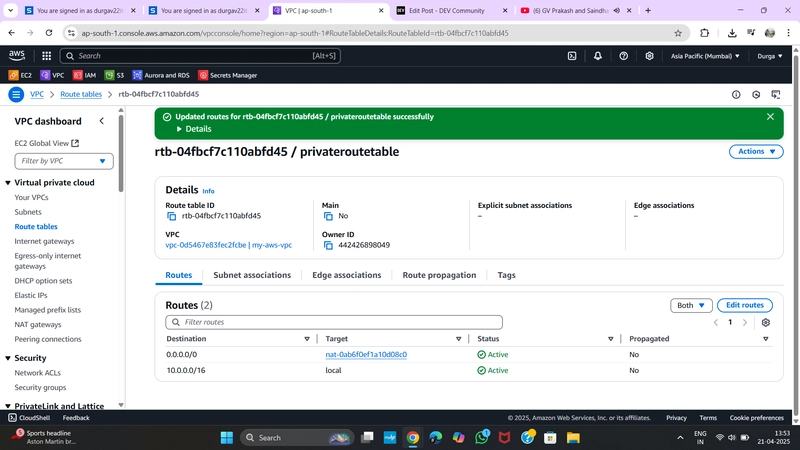
✅ 7. Create a Private Route Table
-
Go to Route Tables > Create Route Table
- Name:
PrivateRT - VPC:
MyVPC
- Name:
-
Select
PrivateRT> Routes > Edit Routes- Add route:
- Destination:
0.0.0.0/0 - Target: NAT Gateway →
MyNATGW
- Destination:
- Add route:
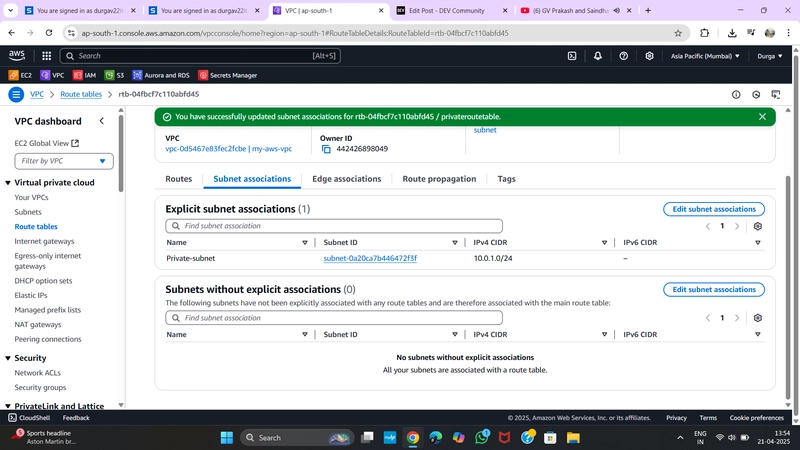
- Go to Subnet Associations
- Attach
PrivateSubnet
- Attach
✅ 8. Launch EC2 Instances (Optional)
➤ Public EC2:
- AMI: Amazon Linux 2
- Network:
MyVPC, Subnet:PublicSubnet - Auto-assign Public IP: Enabled
- Security Group: Allow SSH (port 22) from your IP
➤ Private EC2:
- Same AMI
- Subnet:
PrivateSubnet - Auto-assign Public IP: Disabled
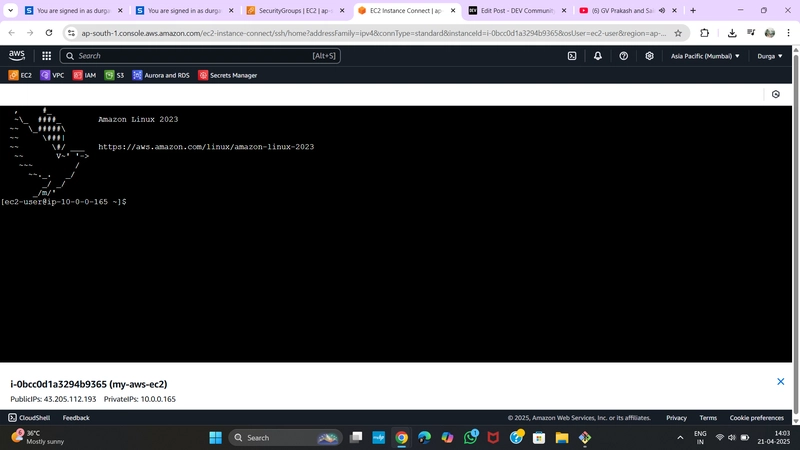
✅ SSH Connection Established
Use your terminal to SSH into the public instance, and from there connect to the private one using its private IP.
⚠️ Troubleshooting Tip
If you're unable to connect:
- Check your Security Group's inbound rules:
- Type: SSH
- Protocol: TCP
- Port: 22
- Source:
My IPor0.0.0.0/0(for open access - use carefully!)
🧹 Clean Up Resources
To avoid unnecessary charges, clean up:
📌 Summary Diagram
VPC: 10.0.0.0/16
├── PublicSubnet (10.0.1.0/24)
│ ├── Internet Gateway → Public RT → 0.0.0.0/0
│ └── NAT Gateway (for private subnet)
├── PrivateSubnet (10.0.2.0/24)
└── NAT Gateway → Private RT → 0.0.0.0/0
✨ Happy Cloud Building!





Top comments (0)