What is Cybersecurity?
Cybersecurity protects internet-connected systems such as hardware, software, and data from cyber threats and attacks. Individuals and enterprises use the practice to protect against unauthorized access to data centers and other computerized systems.
Cyber Threats?
These are popularly known as cyber-attacks or hacks. A cyber threat is an attempt to expose, alter, disable, destroy, steal, or gain unauthorized access to or make unauthorized use of an asset.
Forms of Cyber Attacks
There are various ways cyber-attacks are carried out depending on the nature of what is being attacked. Some of which include:
Phishing Attacks
This attack involves an attacker cloning the login page of a website and sharing it with victims in an attempt to steal their login credentials.
Malware Attacks
This attack involves the creation and distribution of malware. Examples of malware are viruses, trojan horses, network worms, ransomware, etc.
SQL/NoSQL Injection
This attack is targeted at databases. They attempt to steal or clone the database content of a website or app if the queries constructed from user input are not properly sanitized.
Cross-Site Scripting Attacks
This attack involves embedding malicious JavaScript code on websites that do not sanitize user input before rendering. Hackers can use them to steal sensitive data from users and send it to an attacker.
DOS/DDOS Attacks
This attack seeks to overload a web server by sending more requests than it can handle within a short period.
Brute-force Attacks
This attack involves a user trying every possible combination of passwords for a user account on a website.
Man-in-the-middle Attacks (MITM)
This attack is typical in networks and occurs when an attacker intercepts requests sent outside a network. An example of this is an attacker seeing form data submitted on websites and even changing their values (the data can include passwords and credit card information).
Zero-day Exploits
This attack is a newly discovered or developed vulnerability for a system, platform, or application that the creator of the software has not had time to patch or fix.
Social Engineering Attacks
This attack involves an attacker attempting to get access to a system via the users themselves.
Cross-Site Request Forgery Attacks
This attack allows an attacker to perform actions on websites that a user is authenticated on without their consent or knowledge.
Insider Threats
This form of attack involves attacking a system with inside help. This could be an employee who decides to destroy a system and not an unknown outside attacker.
Effects of Cyber-attacks
Cyber-attacks cause various damages to businesses, companies, and individuals, some of which include but are not limited to:
- Loss of corporate information.
- Loss of money and financial information.
- Disruption of business operations and possible bankruptcy.
- Reputational damage to a company or business.
- Legal consequences of a data breach.
Fields in Cybersecurity
There are various paths to take in Cybersecurity, all of which have different areas of specialization. Some of the fields include:
- Application Security
- Penetration Testing
- Reverse Engineering
- Digital Forensic Analysis
- Systems Administration
- Malware Analysis
- Cryptography
Categories of Hackers
There are different categories of hackers, and the categories are based upon the end goal of the hacker. Some report, some exploit, others do it for fun. The categories include:
White Hat Hackers
This set of hackers break into a system, reports vulnerabilities found in the system, and works with the development team to fix the flaws.
Black Hat Hackers
This set of hackers break into a system, then exploit it for their gain or destroy a company or business. These are the set of people referred to as cybercriminals.
Grey Hat Hackers
These set of hackers are the hobbyists and people who practice hacking for the fun of it. They break into systems and either report or exploit or even do nothing about it. They have no definite aim, just on the fence between good and evil.
Hacktivists
This set of hackers targets corporate and governmental platforms with intentions to take their systems, expose information, or make their voices heard.
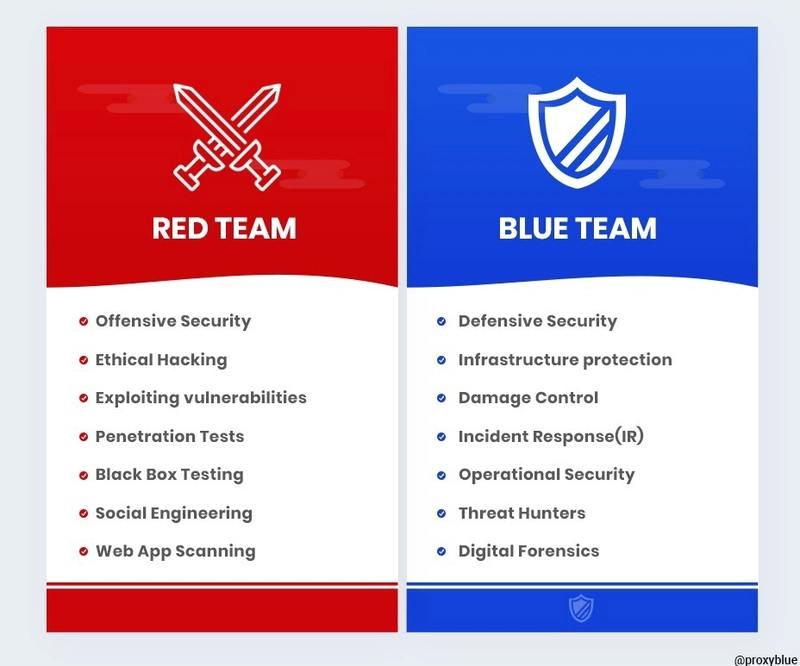
The Reds vs. The Blues
Red teams are offensive security professionals who are experts in attacking systems and breaking into defenses. In contrast, Blue teams are defensive security professionals responsible for maintaining internal network defenses against all cyber-attacks and threats.
A bit of Penetration Testing
Penetration testing, also called ethical hacking, tests a computer system, network, or web application to find security vulnerabilities that an attacker could exploit.
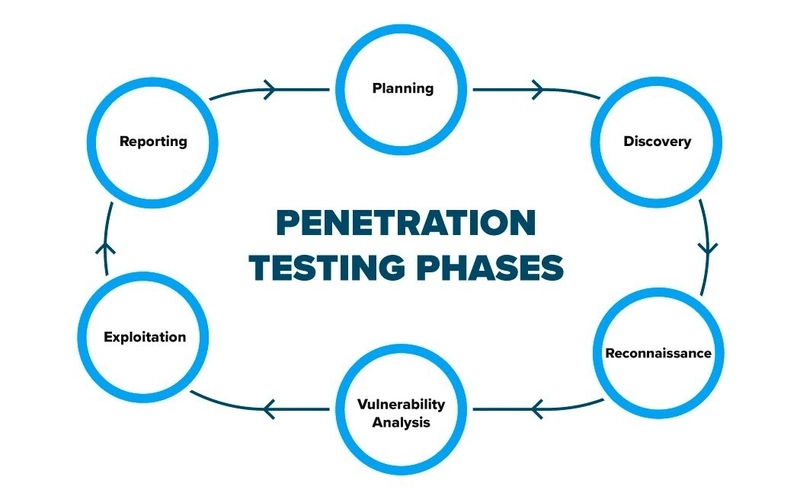
Penetration Testing Stages
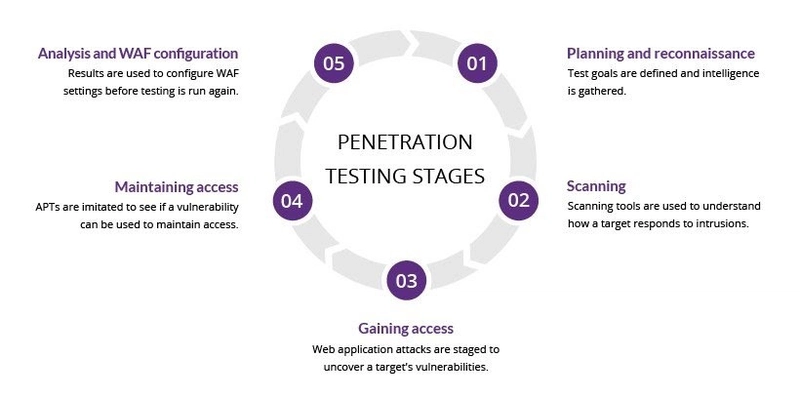
Penetration testing steps gotten from imperva.com
1. Planning and reconnaissance
The first stage involves:
- Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used.
- Gathering intelligence (e.g., network and domain names, mail server) to understand better how a target works and its potential vulnerabilities.
2. Scanning
The next step is to understand how the target application will respond to various intrusion attempts. This is typically done using:
- Static analysis - Inspecting an application’s code to estimate how it behaves while running. These tools can scan the entirety of the code in a single pass.
- Dynamic analysis - Inspecting an application’s code in a running state. This is a more practical way of scanning, as it provides a real-time view of an application’s performance.
3. Gaining Access
This stage uses web application attacks, such as cross-site scripting, SQL injection, and backdoors to uncover a target’s vulnerabilities. Testers then try and exploit these vulnerabilities, typically by escalating privileges, stealing data, intercepting traffic, etc., to understand the damage they can cause.
4. Maintaining Access
This stage aims to see if you can use the vulnerability to achieve a persistent presence in the exploited system long enough for a bad actor to gain in-depth access. The idea is to imitate advanced persistent threats, which often remain in a system for months to steal an organization’s most sensitive data.
5. Analysis
The results of the penetration test are then compiled into a report detailing:
- Specific vulnerabilities that pentester exploited.
- Sensitive data that pentester accessed.
- The amount of time the pentester was able to remain in the system undetected.
Cybersecurity Roadmap
- Learn Linux (Parrot OS or Kali).
- Familiarise yourself with pen-testing tools on your distro.
- Joining cybersecurity communities.
- Following cybersecurity researchers on Twitter.
- Playing CTF.
- Getting Certifications.
Common Cybersecurity Certifications
- Certified Ethical Hacker (CEH)
- CompTIA Security+
- Certified Information System Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- Certified Information Systems Auditor (CISA)
- NIST Cybersecurity Framework (NCSF)
- Certified Cloud Security Professional (CCSP)
- Computer Hacking Forensic Investigator (CHFI)
- Cisco Certified Network Associate (CCNA) Security
Why learn Cybersecurity?
- High paying salary up to $90k annually.
- You're learning and building a skill that only a tiny percentage of people have.
- High demand for cybersecurity experts.
- Cybersecurity is an evergreen industry where personnel is needed in every single company operating in the digital space.
- Unlimited career growth options.
- Opportunities to work with high-profile agencies.
- It's filled with a lot of fun and exciting moments.
Conclusion
In this article, we walked through what Cybersecurity is and saw forms of Cyber Threats and their effects on a business, company, or individual. We also explored fields in Cybersecurity, went over different categories of hackers, and learned about Red and Blue Teams. We took a deep dive into penetration testing and studied its processes, saw a Cybersecurity roadmap, looked at a couple of Cybersecurity certifications, and why people should have Cybersecurity skills.
I also plan to start a series that goes in-depth into explaining forms of cyber-attacks, how they are carried out, and show how to protect your application from them. Subscribe, so you don't miss out on this. If you have any questions, don't hesitate to hit me up on Twitter: @LordGhostX







Top comments (0)