A single Kubernetes workload has over 30 security settings with 1 billion potential combinations. You need to be a Kubernetes expert to understand if the final configuration introduces a high risk to your cluster. With a single change to a single file, you can open your entire Kubernetes cluster to attacks, leak secrets, risk confidential data, or accidentally give public access to private services.
We at Octarine released the open source kube-scan tool that allows you to run a quick and easy security risk assessment on your Kubernetes workloads to instantly understand the security posture of your clusters.
A safe and easy way to assess your security posture
Kube-scan is a pod that runs inside your cluster. It scans all your manifest files, analyzes security settings and gives you a security score for your workloads through a simple Web UI. For each workload, you’ll get a clear explanation of the risk factors, what settings remediate or aggravate risks, and what the potential consequences are (container escape, Man-in-the-Middle, unwanted interactions between containers, and so on).
Kube-scan is designed to help you understand which of your workloads are most at risk and why, and enables you to prioritize updates to your Pod Security Policy, Pod definitions, and manifest files to keep your risk in check.
How kube-scan calculates a risk score
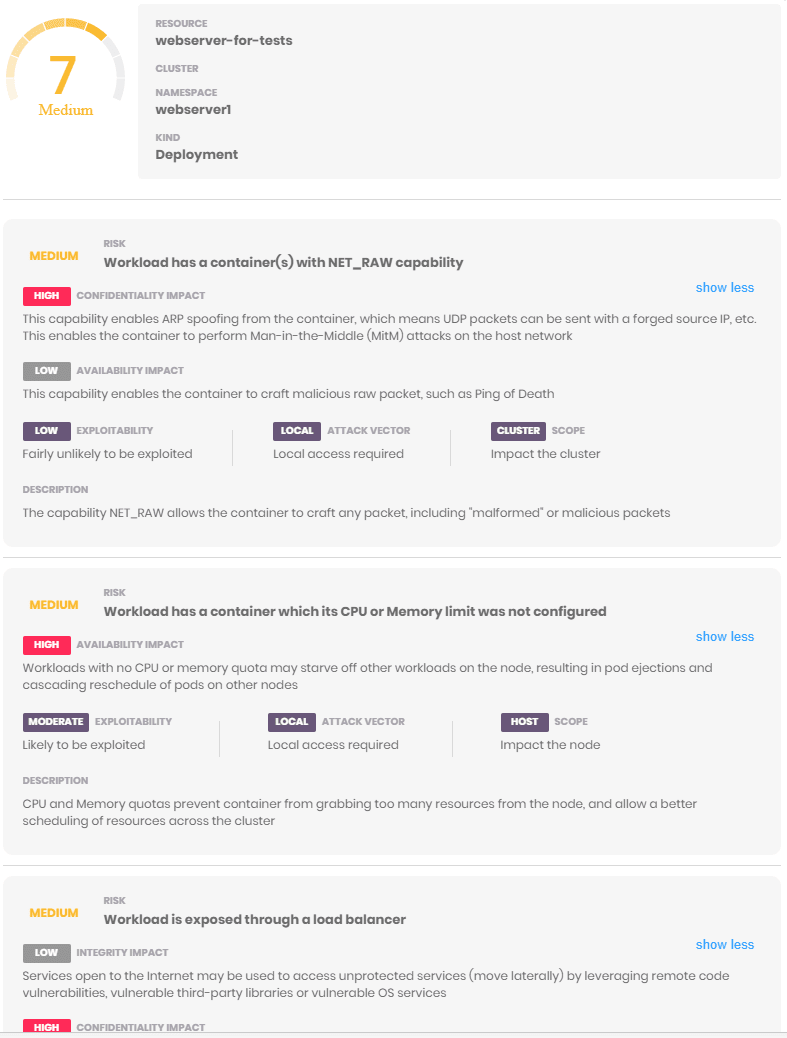
Open source kube-scan analyzes over 30 security settings including privilege levels, capabilities, and Kubernetes policies and establishes a risk baseline. Then it analyzes how these settings work in tandem so that you can understand what combinations will decrease (or increase) your level of risk. For example, the combination of potential local access risks (privileged container, container running as root) and remote access (listening to a port, no Kubernetes Ingress policy, etc.) is at a greater risk if the service is exposed to the Internet through a Load Balancer, a host port, or a shared host network.
Kube-scan also takes into consideration the ease of exploitation, and the impact and scope of exploits. This is similar to the Common Vulnerability Scoring System (CVSS). The combination of risks, remediation, aggravations factors, exploitability and impact is scored between 0 (safe) to 10 (very risky).
How to install kube-scan
Kube-scan is a single-pod deployment with a YAML file to help deploy it quickly to your cluster. The pod contains the manifest scanner, scoring engine, and the web UI.
No data leaves the containers. There is no ingress or egress access, and no data is sent or retrieved from Octarine. It is safe to run in any environment and can be deleted after you access the risk score page. You can find the instructions to deploy kube-scan on GitHub.
There are two ways to deploy the kube-scan container:
1. Direct access to the kube-scan pod
This command installs and starts the kube-scan pod:
kubectl apply -f https://raw.githubusercontent.com/octarinesec/kube-scan/master/kube-scan.yaml
Then, proxy your local port 8080 to the pod’s port 80 in the cluster:
kubectl port-forward --namespace kube-scan svc/kube-scan-ui 8080:80
Once the pod is running, simply connect to this URL to see the scan results:
http://localhost:8080/
2. Kube-scan behind a load balancer
If you prefer to not create a port-forward to kube-scan Web UI, you can deploy kube-scan behind a load balancer:
kubectl apply -f https://raw.githubusercontent.com/octarinesec/kube-scan/master/kube-scan-lb.yaml
Then, get the hostname used to access the Web Ui through the load balancer:
kubectl -n kube-scan get service kube-scan-ui -o jsonpath={..hostname}
This will display the hostname you need to connect to over port 80:
http://:8080/
Browse the kube-scan Web UI
After the installation is done, you can see the risk score for all your workloads. Click on any risk to see a breakdown of the risk factors.
The score is calculated once, when the pod starts. If you would like to run a new scan, delete the pod. You can install kube-scan in multiple clusters to compare your security posture in different environments.



Oldest comments (0)