Permissions on Graph is a very interesting topic. It is wide and can be confusing sometimes. I will try my best to explain a few things that I understand on the topic.
For starters, I will explain how to revoke consent to permissions that you have granted for any client application that consumes Microsoft Graph.
Do you feel like an application you signed into has too much permissions?
Do you know that you can revoke consent to some permissions that you have granted that application?
For this article to make sense, you need to understand how to register client applications on Azure. This article https://learn.microsoft.com/en-us/azure/healthcare-apis/register-application will help
Client applications use delegated permissions to access information on behalf of a signed in user. This article will focus on client applications, but the steps can also work for backend services.
Let's also understand a few terms before we delve into the details of revoking consent:
Service principal - Whenever you sign into an application that consumes Graph, a copy of the application's identity is saved in your Azure tenant. This ID is used to identify the application in your Azure tenant.
Permission grant - When you give permissions to a client application to access resources on your behalf, the information is contained in an object called a permission grant.
To revoke consent,
- Retrieve the
service principal IDfor the application whose permission consent you want to revoke Log in to Azure portal then click on Enterprise Applications:

This will list all the applications that you have signed into and given consent. Look for the application whose permissions you want to revoke and copy the application ID.

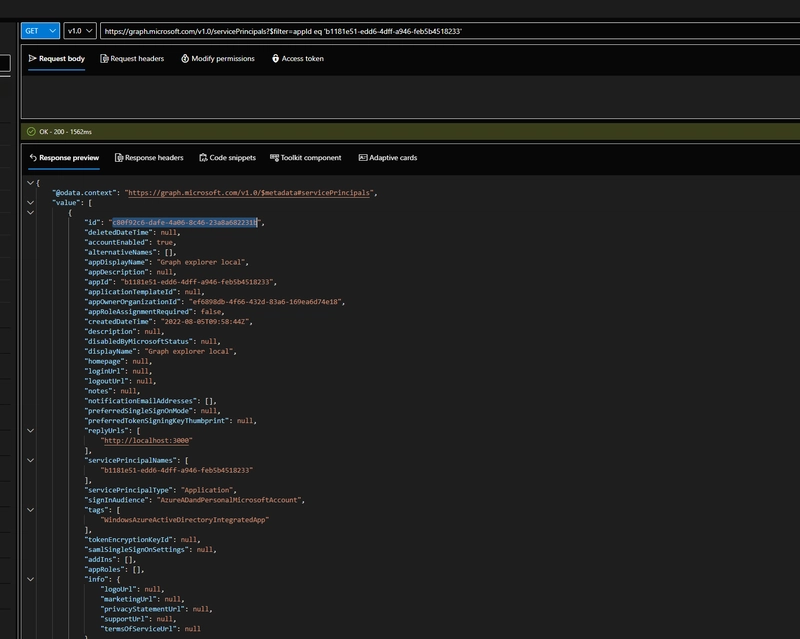
For my case, I want to revoke permissions for Graph explorer local with Application ID: b1181e51-edd6-4dff-a946-feb5b4518233.
The service principal ID is a representation of the Graph explorer local app in my tenant.
Let's hop onto https://developer.microsoft.com/en-us/graph/graph-explorer to get this service principal ID.
We will search for the service principal whose appId is the same as the app ID for Graph explorer local https://graph.microsoft.com/v1.0/servicePrincipals?$filter=appId eq 'b1181e51-edd6-4dff-a946-feb5b4518233'
The ID highlighted below is the service principal ID:
- Retrieve permission grants
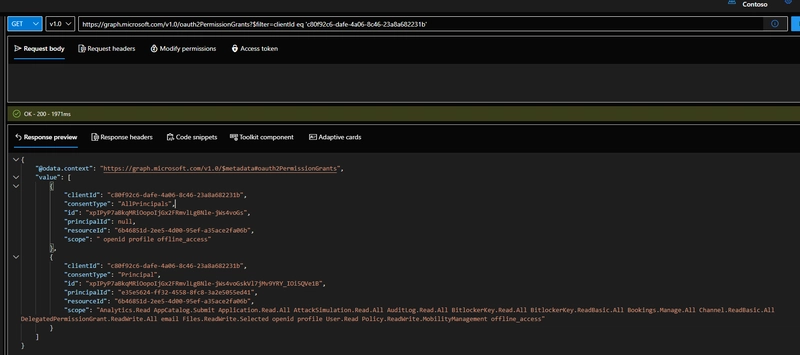
Using this service principal ID, I can get the permission grants for this applicaiton in my tenant. The endpoint that returns this information is
v1.0/oauth2PermissionGrants. Here is the query:https://graph.microsoft.com/v1.0/oauth2PermissionGrants?$filter=clientId eq 'c80f92c6-dafe-4a06-8c46-23a8a682231b'Notice that this endpoint refers to the service principal ID as 'clientId'.
The payload returned by the endpoint contains permission grants for all members of the tenant who have signed into 'Graph explorer local' and given consent to permissions. We can also see the permissions that each signed in tenant has given consent to in the scopes property.
- Filter permission grants to get the grant that I want to modify
Since we are revoking our own permission consents in the tenant, we need to find the correct
principalIdwhosegrantwe want to modify/(whose permission we want to revoke). If you already know the principalID whose consent you want to revoke, copy the id of the grant. In my case, it is the highlighted ID below:

If you do not know your principal ID, head over to Azure portal and click on Azure Active Directory:

On the left pane, click on Users:

This will list all users in the tenant. Click on the user whose principalID you want to get.
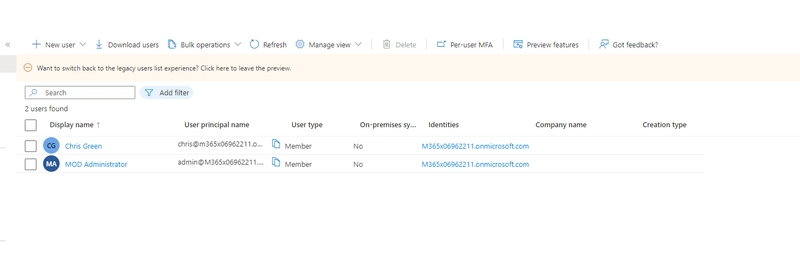
In my case, it is Mod Administrator.
The principal ID is the Object ID. Copy this ID

Lets go back to Graph Explorer. Notice that the ID I just copied is the principalID I selected.
- Modify the permission grant of the selected principal ID
Since we know the principal ID whose grant we want to modify, we will make a patch request to the
v1.0/oauth2PermissionGrantsendpoint. Copy the ID of the permission grant for the principal ID we just got from AAD. Next, we'll make a patch request to the
Next, we'll make a patch request to the oath2PermissionGrantsendpoint. On Graph Explorer, click on the GET button and select patch. Using the permission grant ID we just copied, type the URLhttps://graph.microsoft.com/v1.0/oauth2PermissionGrants/<permission-grant-id>, wherepermission-grant-idis the ID we just copied.
Next, we will add a request body which has an updated scope. The updated scope should have the new permissions minus the ones we want to revoke.
When I make a new call to the v1.0/oath2PermissionGrants endpoint for permission grants, this is what we get:
You can see that the scope object has been updated with the new permissions and the permission I removed from the grant are no longer there.
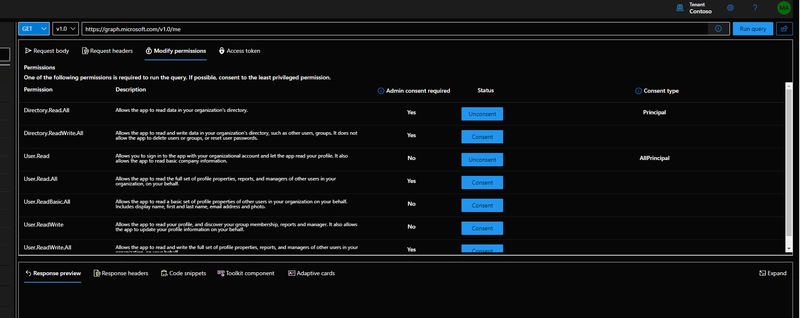
If you want to revoke consent to permissions that you have granted Graph Explorer: veloper.microsoft.com/en-us/graph/graph-explorer, then all of these steps have been done for you. All you need to do is head over to the Modify Permissions tab
Once you are here, click the Unconsent button to revoke consent for specific permissions :)
Let me know what you would like me to write about in my next article :)








Top comments (0)