For newcomers to cybersecurity, setting up a practice range environment for penetration testing is often necessary. A practice range is essentially a platform simulating a real network environment, allowing security personnel to conduct various security tests (like penetration testing, vulnerability hunting, and attack/defense drills) in a controlled setting. Building such a range helps professionals practice simulating real-world attacks and vulnerabilities legally and ethically, ultimately enhancing the effectiveness and accuracy of security defenses.
The technical architecture for building a practice range environment is fundamentally the same as deploying a real website. While production environments might involve more complex configurations (like load balancing, security hardening, etc.), the core runtime environment relies on these key components:
- Website Application Code: Includes both front-end and back-end logic.
- Web Server: Handles requests and serves content. Common examples include Nginx, Apache, Caddy, etc.
- Database: Stores and manages data, such as MySQL, MongoDB, PostgreSQL, etc.
These three components form the foundation of a functional website.
Based on these components, various technology stacks can be combined, such as Frontend + Python + Nginx + MySQL, Frontend + Java + Nginx + MySQL, Frontend + PHP + Apache + MongoDB, etc.
Manually configuring and managing all these components and their dependencies for a practice range would be quite tedious and time-consuming. Therefore, to simplify deployment and focus on the practice itself, we recommend using a convenient integrated tool like ServBay. It helps us quickly and easily set up website runtime environments with various combinations.
Okay! Let's start building the practice range environment!
ServBay
ServBay Introduction
ServBay is a development environment management tool that integrates common development languages (including Python, PHP, Go, Node.js, etc.), as well as popular web servers and databases. For our penetration testing needs, we must consider various scenarios. ServBay's core advantage lies in its one-click switching between different software versions, enabling you to quickly simulate various target environments with known vulnerabilities.
ServBay Installation
First, let's install ServBay. Official download link: https://www.servbay.com/download
Enter ServBay's initialization interface and select the web servers, languages, and databases you need to install.
Wait for the installation to complete. ServBay will run automatically.
The following screen indicates that the installation is complete.
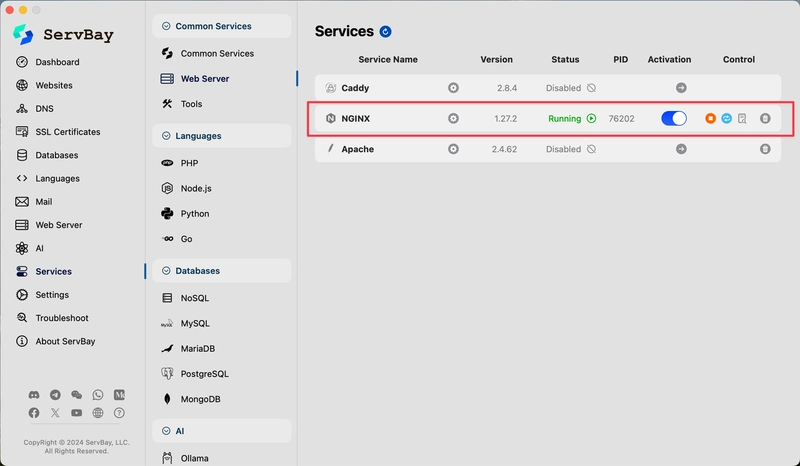
Download and start the MySQL database.
Then, start the required web server. I chose Nginx here.
Once the environment is ready, we need to install the practice application. Here, I recommend DVWA.
DVWA
DVWA Introduction
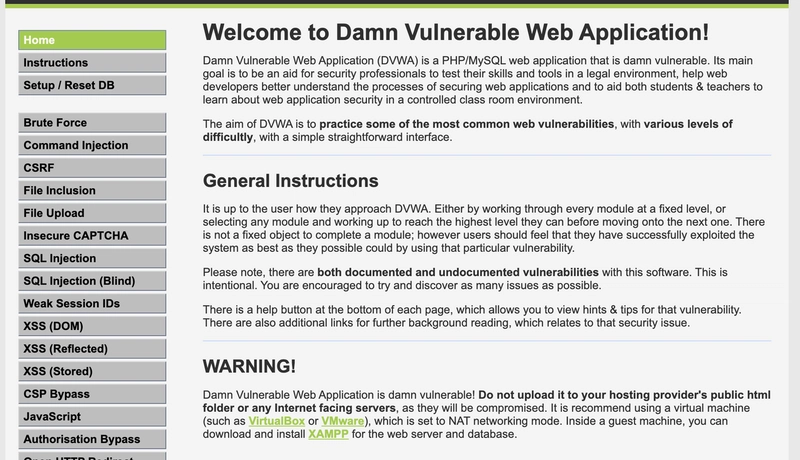
DVWA (Damn Vulnerable Web Application) is, simply put, a website deliberately filled with vulnerabilities ("damn vulnerable") specifically for practice. It intentionally includes a bunch of common web vulnerabilities, such as SQL Injection, XSS (Cross-Site Scripting), File Upload vulnerabilities, etc., making it perfect for cybersecurity learners to practice on.
DVWA includes 10 attack modules.
Additionally, DVWA allows you to manually adjust the security level of the source code: Low, Medium, High, and Impossible. The higher the level, the stricter the security measures, and the greater the penetration difficulty. Whether you're a beginner or an expert, DVWA can meet your practice needs!
DVWA Installation
DVWA Download Link: https://github.com/digininja/DVWA
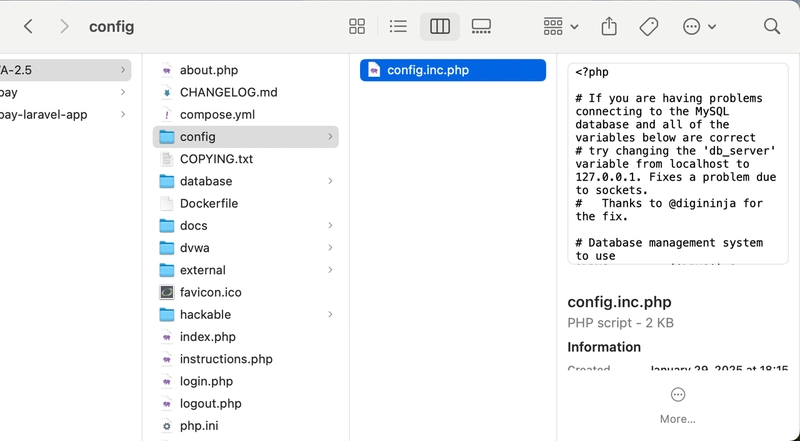
After downloading and extracting, move the files to the /Applications/ServBay/www/ directory. (Note: This path is macOS specific. Adjust if using a different OS, typically within ServBay's designated web root folder.)
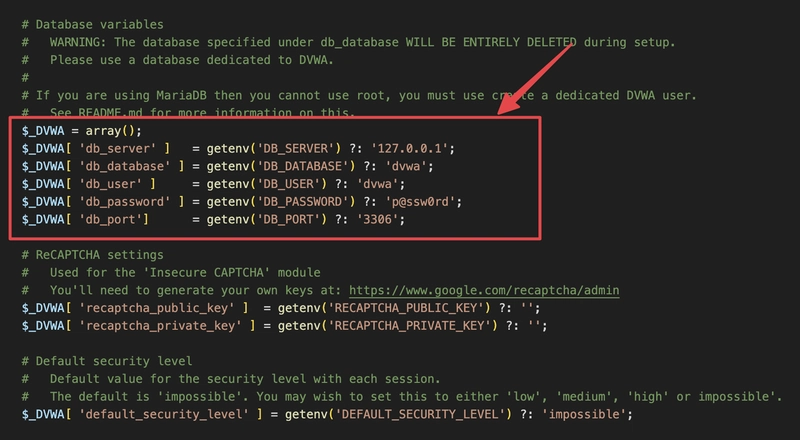
Then, rename the config.inc.php.dist file to config.inc.php. You only need to modify the database username and password; other configurations can remain unchanged.
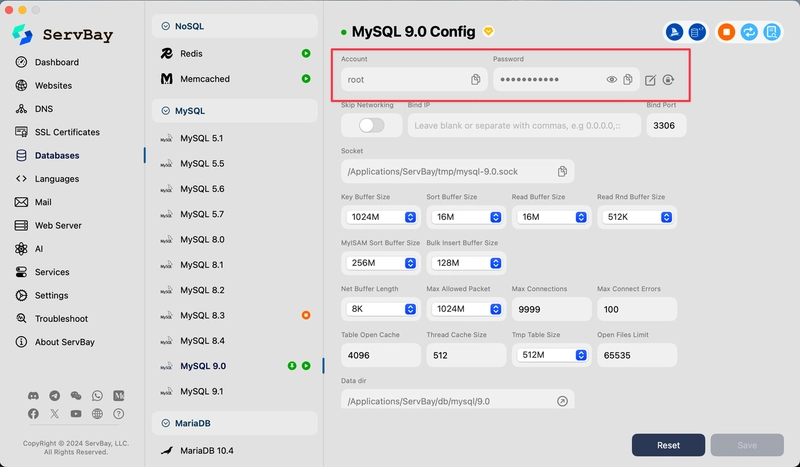
Friendly Reminder: You need to enter the MySQL credentials here (username and password). The defaults can usually be found in the ServBay panel unless you've changed them during setup or afterwards. If you have modified the MySQL username or password, use your custom credentials here.
Configure Database and Website
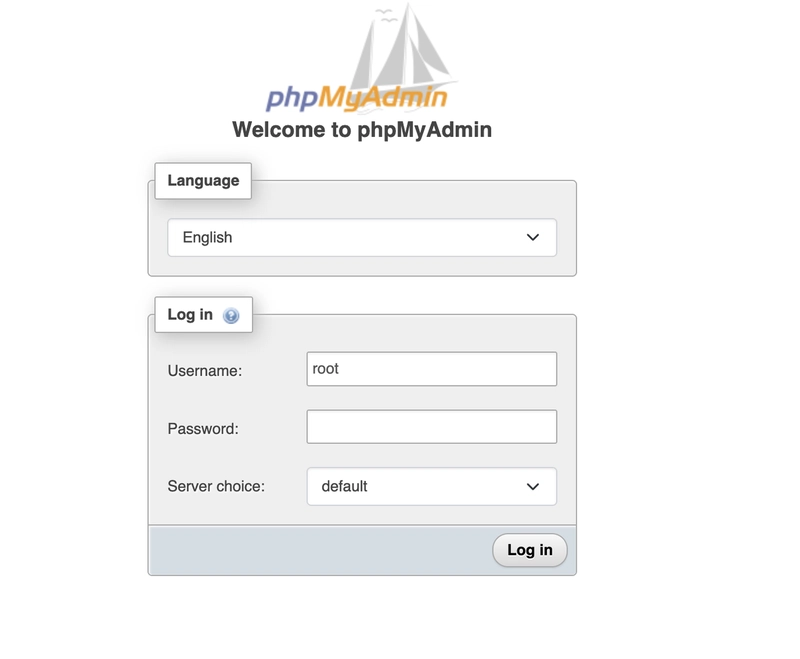
In your browser, go to https://servbay.host/ (or the host configured in ServBay) to open the instance website. Click on phpMyAdmin to reach the login page.
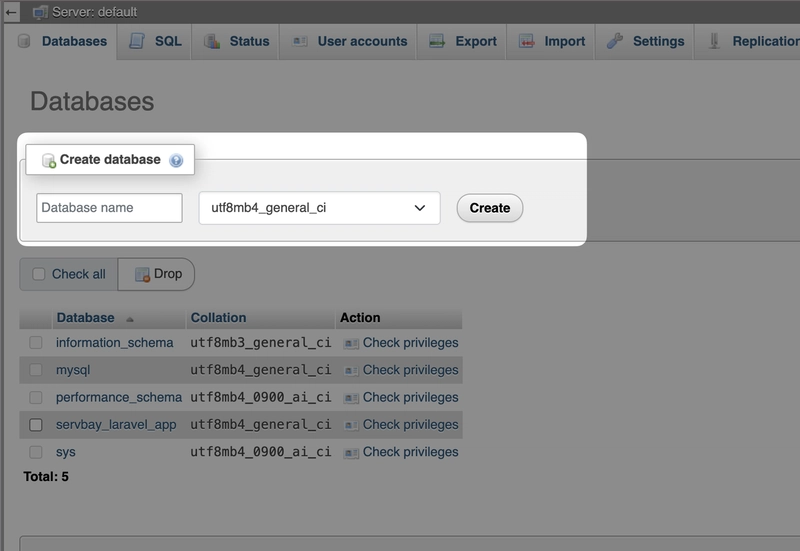
Enter the MySQL username and password (found in ServBay or set by you), access the database management page, and create a new database.
Enter the name for the new database (usually 'dvwa' as specified in the DVWA config file) and click 'Create'.
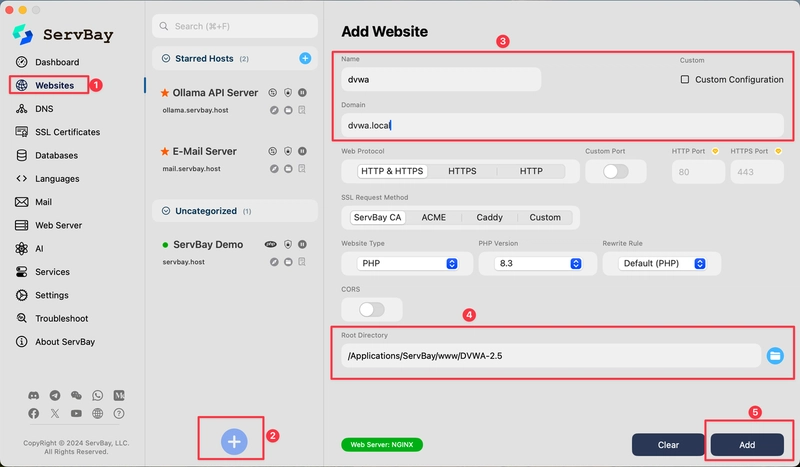
Now, open ServBay and create a new site, pointing its root directory to the DVWA folder you placed earlier (e.g., /Applications/ServBay/www/DVWA). Assign it a domain name (e.g., dvwa.test).
In your browser, enter the domain name you just configured for the site. You should successfully reach the DVWA setup/login page. If it's the setup page, click the "Create / Reset Database" button first.
Enter the default username admin and password password to log into the penetration testing practice page.
Alright, DVWA setup is complete! Congratulations!!!
Click the 'DVWA Security' button on the left menu. On this page, you can set the security level for the DVWA practice range (Low, Medium, High, Impossible). Choose the desired level according to your needs and start your penetration testing practice.
By combining ServBay and DVWA, you can quickly build a cybersecurity practice range environment. Your journey from beginner to cybersecurity pro is well underway!




Top comments (0)
Some comments may only be visible to logged-in visitors. Sign in to view all comments.