Azure Logic Apps is a somewhat unique cloud service that allows to connect your business-critical apps and services, automating your workflows without writing a single line of code.
There are numerous articles out there about how to deploy Azure Logic App with Azure Resource Manager templates, including official Microsoft documentation:
Automate deployment for Azure Logic Apps by using Azure Resource Manager templates
But in a corporate environment this kind of resources, especially in Production environment, are predefined and secured. Developers often do not have permission to overwrite existing resources, and deploying with ARM templates does exactly that. The template defines the infrastructure, resources, parameters, and other information for provisioning and deploying your logic app. But what we need is to leave the infrastructure alone and deploy just our logic app and its parameters.
So what to do when you dealing with this kind of restricted environment but still want to leverage the power of CI/CD pipelines?
Fortunately, when you create a Logic App using Visual Studio, a sample deployment Powershell script named "Deploy-AzureResourceGroup.ps1" is created for us too. In fact, it uses Azure PowerShell extension that simplifies the management of Azure Cloud services.
Here is a beginning of this script, pay attention to the parameters that we can provide to customize it:
Param(
[string] [Parameter(Mandatory=$true)] $ResourceGroupLocation,
[string] $ResourceGroupName = '<YOUR RESOURCE GROUP NAME>',
[switch] $UploadArtifacts,
[string] $StorageAccountName,
[string] $StorageContainerName = $ResourceGroupName.ToLowerInvariant() + '-stageartifacts',
[string] $TemplateFile = 'LogicApp.json',
[string] $TemplateParametersFile = 'LogicApp.parameters.json',
[string] $ArtifactStagingDirectory = '.',
[string] $DSCSourceFolder = 'DSC',
[switch] $ValidateOnly
)
...
A full code for the deployment script is provided at the end of the article for those who want to use VS Code or other editor to develop a Logic App.
Let's leverage this script and create CI/CD pipelines in Azure DevOps.
Creating a build artifact in Azure DevOps pipeline
The only things that we need to create a deployable artifact are the files that are located in the project's folder: a JSON file containing the workflow, a parameters file, and a script. So a build pipeline could be extremely simple, consisting just of one step, like the one below.
- task: PublishBuildArtifacts@1
displayName: 'Publish Artifact: LogicApp'
inputs:
PathtoPublish: 'src/LOGIC_APP_FOLDER'
ArtifactName: 'LogicApp'
publishLocation: 'Container'
Execute the build pipeline to create an artifact.
Release pipeline
We can start with an empty Release pipeline, and add an artifact produced by the Build pipeline.
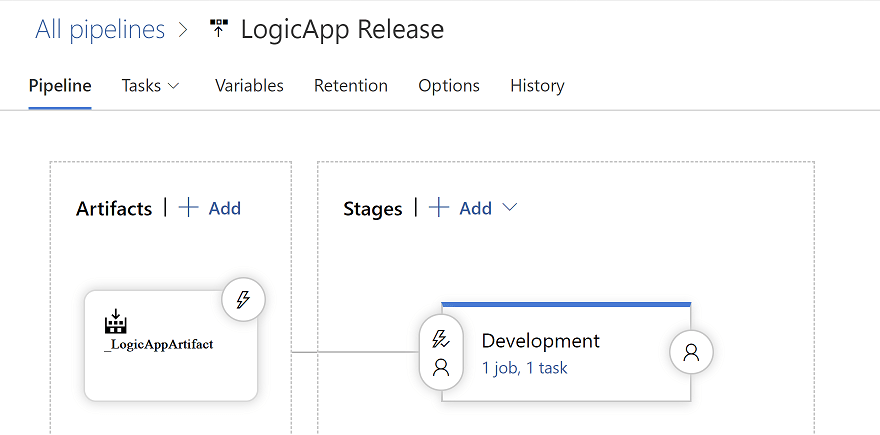
Next, we add a stage, and a single Azure Powershell Task. It is very important to select a Task Version as "2.*" and, correspondingly, Azure PowerShell Version as "Specify Other Version" and Preferred Azure PowerShell Version as "2.1.0" as that is the version that the deployment script is using.
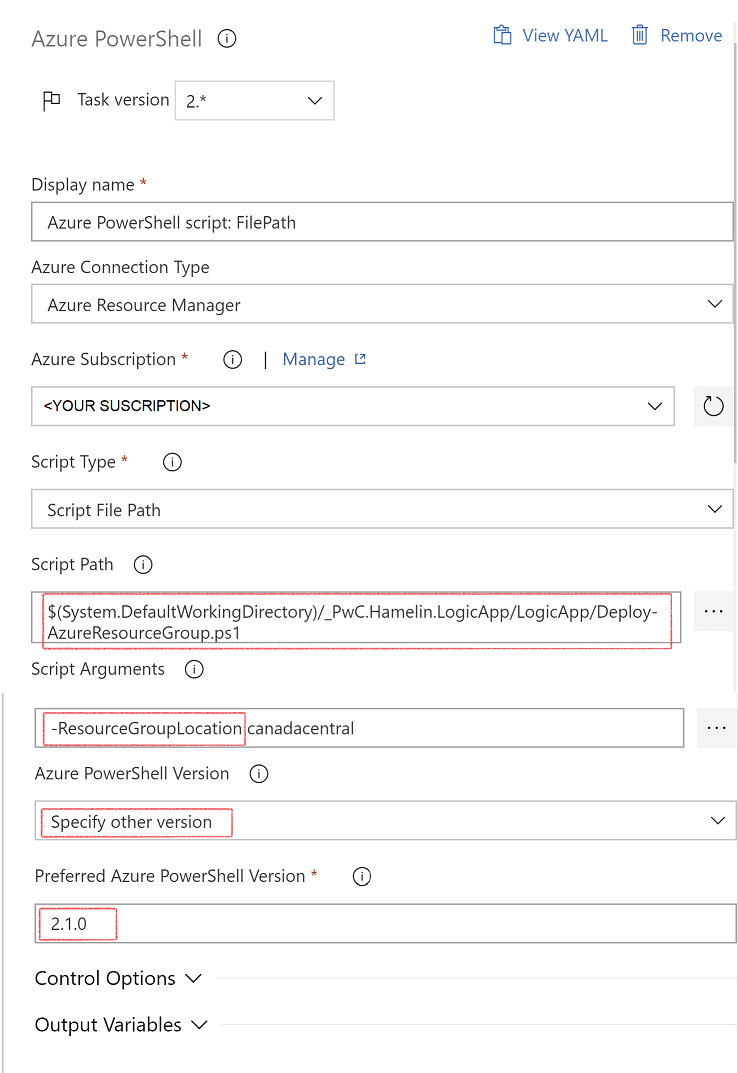
Other important parameters are Script Path - you can navigate to your artifact and select a deployment script.
Also, Script Arguments is a field where we can provide parameters to the script itself. Those arguments correspond to the parameters that we see at the beginning of the script.
A good thing about Azure Powershell task is that it will automatically authenticate it to the Azure via service connection, so you do not have to worry about that.
Powershell Script
Here is a gist with a complete script's code:
Conclusion
An alternative method to deploying Azure Logic app is to use Azure Powershell script that is relatively straightforward, does not require elevated permissions, and is applicable in the enterprise and restricted environments.
Well, that is all for this simple recipe. Good luck, and when developing your Logic App be sure not to use a cat logic!

Photo credit: Ryozuo



Top comments (1)
+1 for cat logic