In this article series, I will be walking though the process of configuring secure access to workloads using Azure virtual networking. In this exercise, we will:
- Create and configure a route table.
- Link a route table to a subnet.
We will be building on what was done in this exercise so make sure you have it done before attempting this one
Exercise 04: Configure network routing
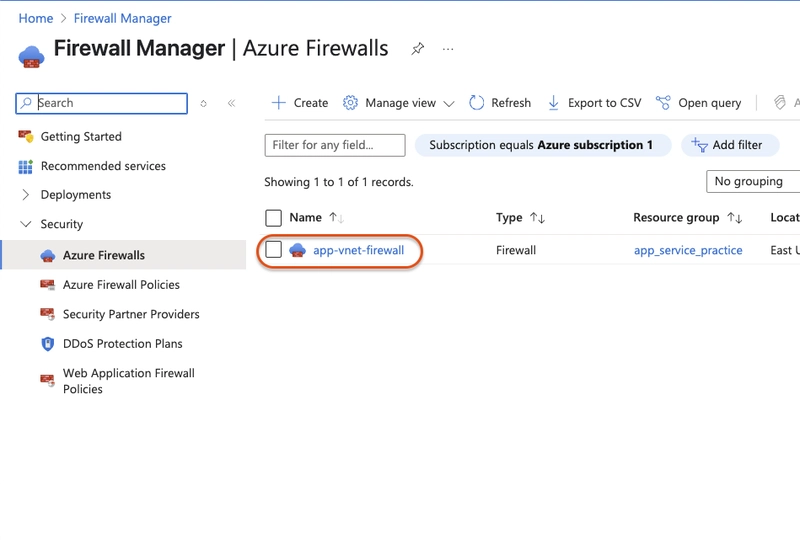
- In the search box at the top of the portal, search for and select Firewalls.
Search for and select Route tables
Enter these properties:
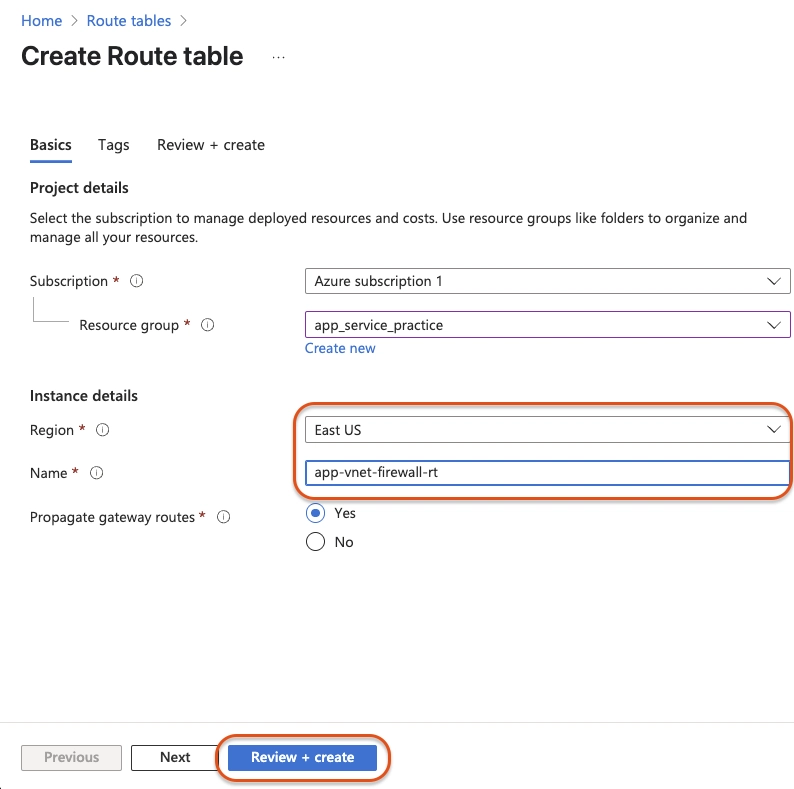
Subscription: Select your subscription
Resource group: Your resource group
Region: East US
Name:app-vnet-firewall-rtWait for the route table to deploy, then select Go to resource.
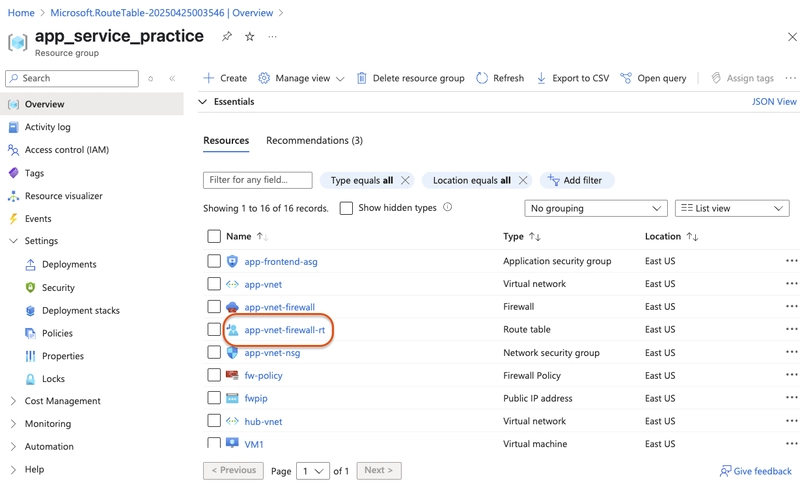
In the portal, continue working with the route table, select
app-vnet-firewall-rt.
-
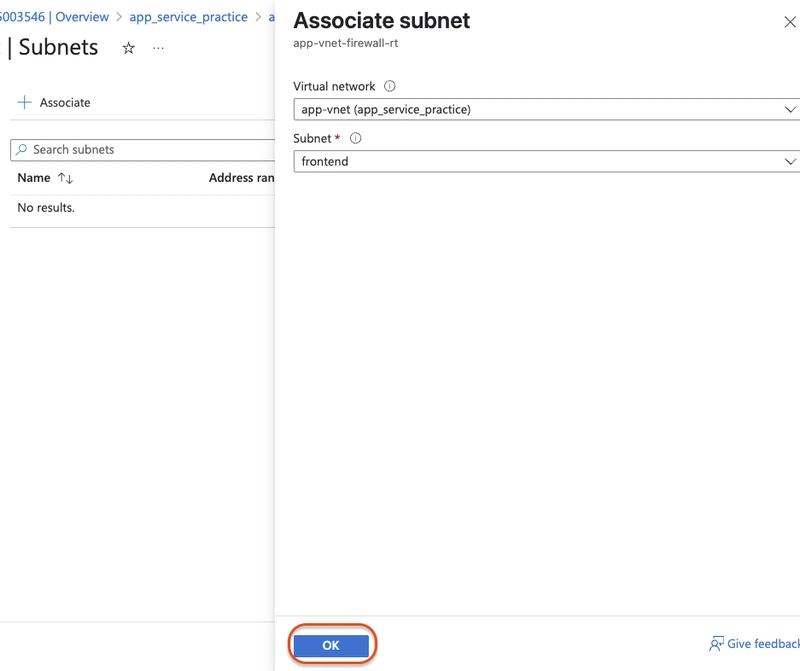
Select this configuration:
- Virtual network: app-vnet
- Subnet: frontend
Again select + associate and add this configuration:
-
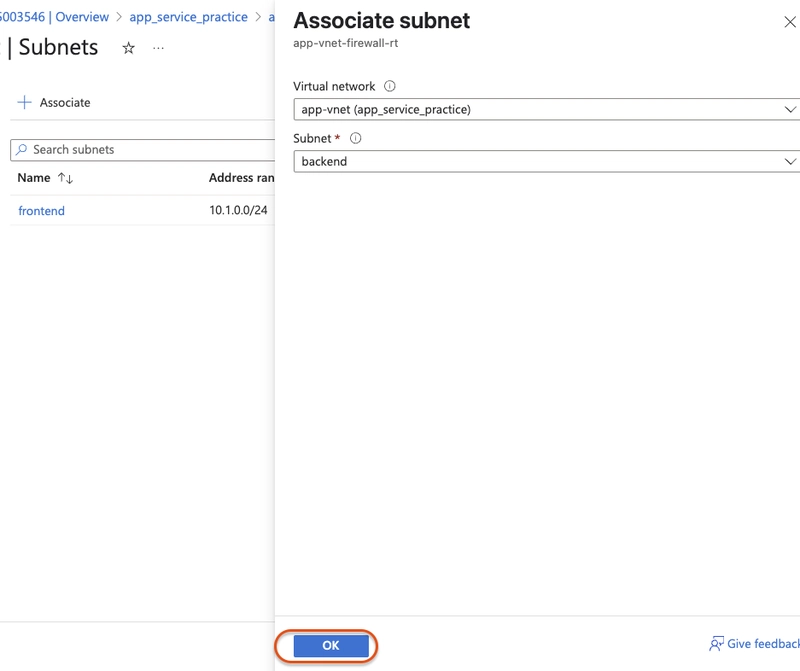
Select this configuration:
- Virtual network: app-vnet
- Subnet: backend
Select
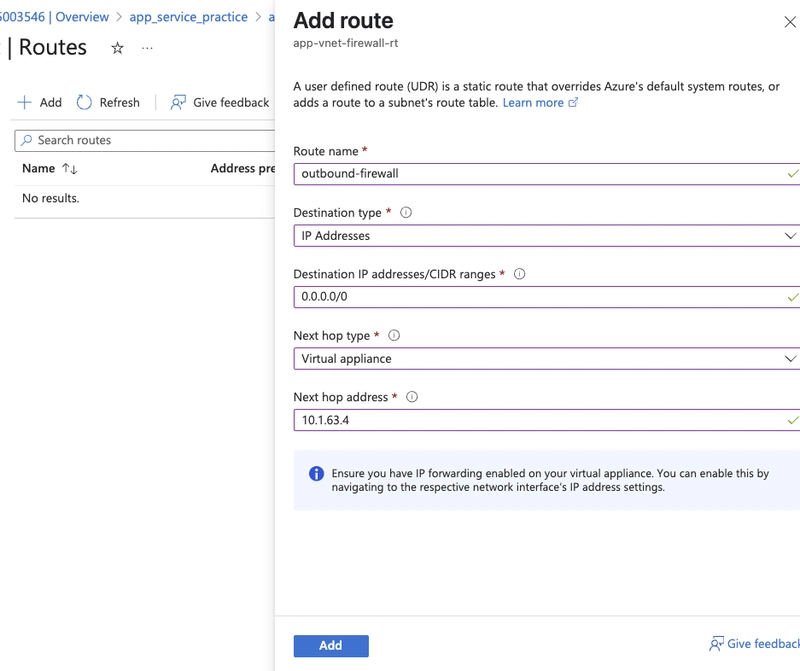
app-vnet-firewall-rt.in route tablesIn Settings, select Routes and then + Add.
-
Configure:
- Route name: outbound-firewall
- Destination type: IP addresses
- Destination IP addresses/CIDR range: 0.0.0.0/0
- Next hop type: Virtual appliance
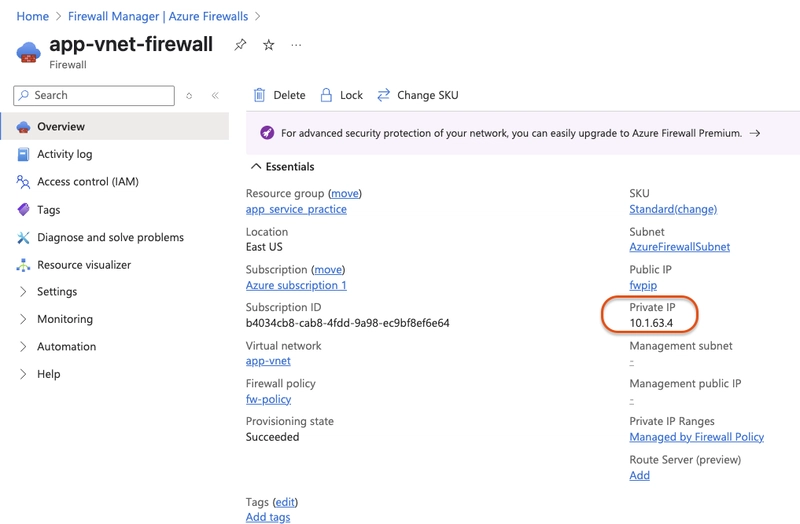
- Next hop address: private IP address of the firewall
You’ve now set up a route table and linked it to your subnets to direct all outbound traffic through the Azure Firewall. This ensures centralized control and enhanced security for your network traffic—an essential step in building a secure and well-managed Azure environment.



Top comments (0)