Airline websites don’t care about your privacy follow-up: Emirates responds to my article with full-on denial
Yesterday, The Register wrote about my exposé on the privacy failings of airline websites.
When I published my original article last Friday, Emirates had failed to respond to my request for comments. But Emirates did respond to The Register, with the following statement:
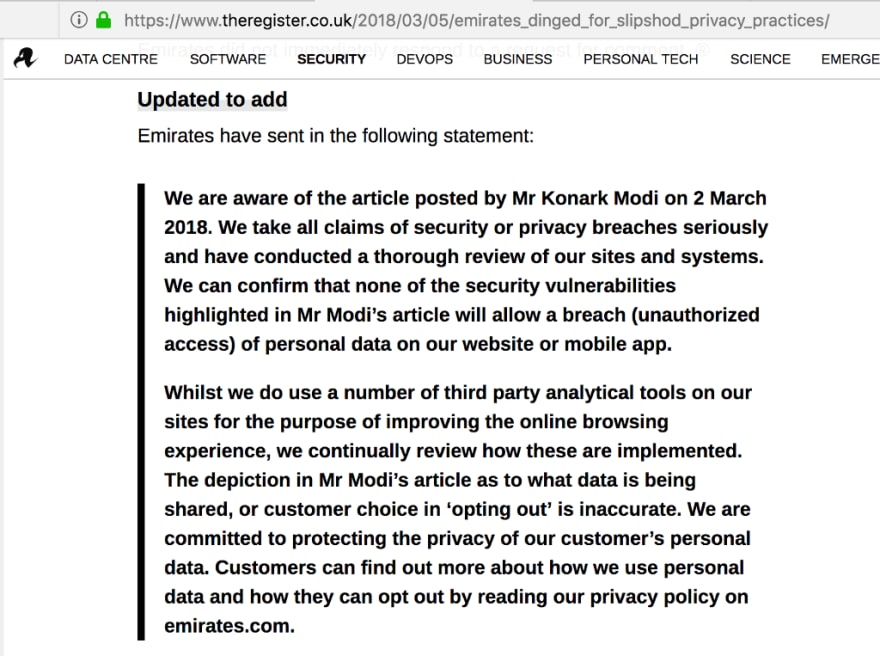
Their statement is not only vague — it is factually incorrect. And I feel it’s my professional duty to call them out on this.
A breakdown of their statement, and how their logic breaks down when you really think about it
Issue #1
First Emirates says, “We can confirm that none of the security vulnerabilities highlighted will allow a breach (unauthorised access) of personal data on our website or mobile app.”
How does Emirates define breach? Well, Wikipedia defines a data breach like this:
“A data breach is a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorised to do so.”
In its Privacy Policy, Emirates highlights the importance of safeguarding Booking Reference information:
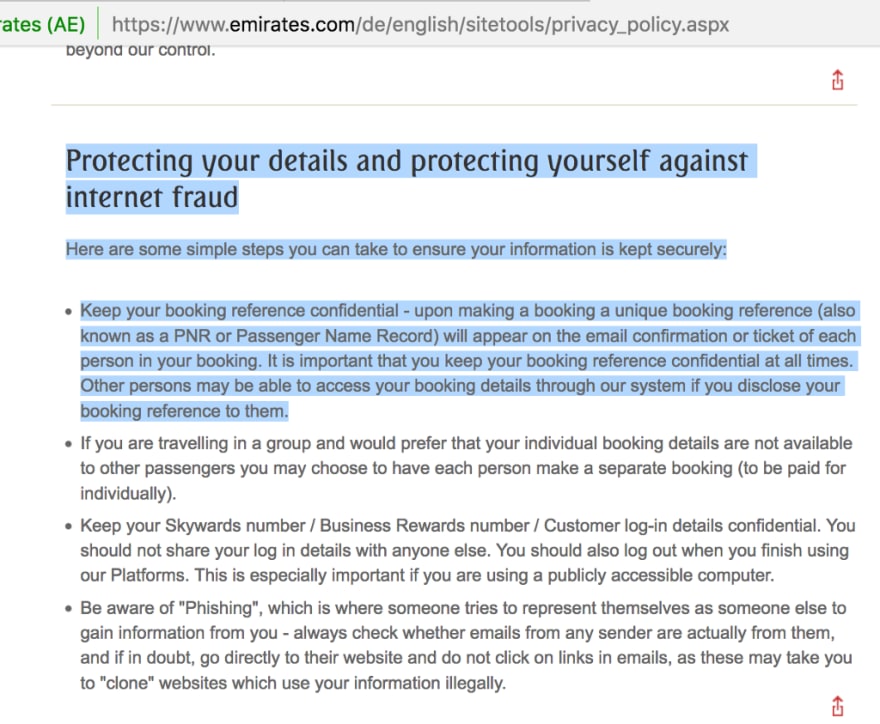
Update 8th March, 2018: Another exhibit how Emirates seems to have forgotten to pay heed to their own advice “keep your Booking Reference safe” and is still sending it to Google Analytics from mobile app, via key:cd8 (unmasked). I have masked the fields in the picture to ensure Privacy.

For any changes to an existing booking, a Booking Reference number and Last name is all that is required. There is no requirement to verify who initially made the booking and whether the person making the changes is authorised to do so or not.
Emirates.com and the Emirates mobile app version (6.1.0) both allow access to their Manage Booking section based only on these two data points. This a standard practice across airlines, and this is not the point of contention for the purposes of this article.
But this is when it gets worrisome
As of March 6th, 2018, Booking Reference number and Last Name, among many other data points, are still being sent to the third-parties implemented. Does Crazy Egg, Boxever, Coremetrics need Booking Reference Number and Last name for showing Heat Map of the page? I don’t think so.
This is the problem area — passing on user’s personal information to third parties who have absolutely no need for this information to render their services to Emirates “for the purpose of improving the online browsing experience.”
The importance of using HTTPS links has been established over and over again by everyone who is anyone in the field of Technology. HTTP links are not only vulnerable to Man-In-The-Middle attacks but can also suffer from injection of malicious data.
I am not sure how Emirates is confident enough to “confirm that none of the security vulnerabilities highlighted in (Mr. Modi’s) article will allow a breach (unauthorized access) of personal data on our website or mobile app” when track.emirates.email still does not have any SSL. How do they plan to avoid Man-in-the-Middle attacks?
Issue #2
Emirates says, “Whilst we do use a number of third party analytical tools on our sites for the purpose of improving the online browsing experience, we continually review how these are implemented.”
I shared in the article how Passport information and contact details were earlier un-obfuscated on both website and Mobile app. While the website was fixed when I checked last in February 2018, the mobile app continues to be problematic in this area. This can happen only when there is a lack of communication between the Website and Mobile Development Team or they did not “continually review the implementation” across all products.
Another question that begs to be answered is what are the parameters for reviewing the implementation of third parties. Unless the mandate is strictly to NOT leak any kind of user-information, the reviews could be of anything and would not have the slightest impact on the security and vulnerability of user information being freely passed on the third parties.
The last time this issue was highlighted to Emirates was in October 2017. In the 5 months that have passed since then these issues were not picked up by the review team. Maybe they are not as “continuous” as Emirates claims them to be.
Issue #3
Emirates says, “Customers can find out more about how we use personal data and how they can opt out by reading our privacy policy on emirates.com”


Upon a thorough review of Emirates’ Privacy & Cookie Policy, these are the points to note:
It does not list ALL the implemented third-parties and the information being shared with them. Third parties like Boxever, ads-twitter.com, Coremetrics, Imigix, bing and many other that I had aggregated from their website are not even mentioned in their Privacy Policy.
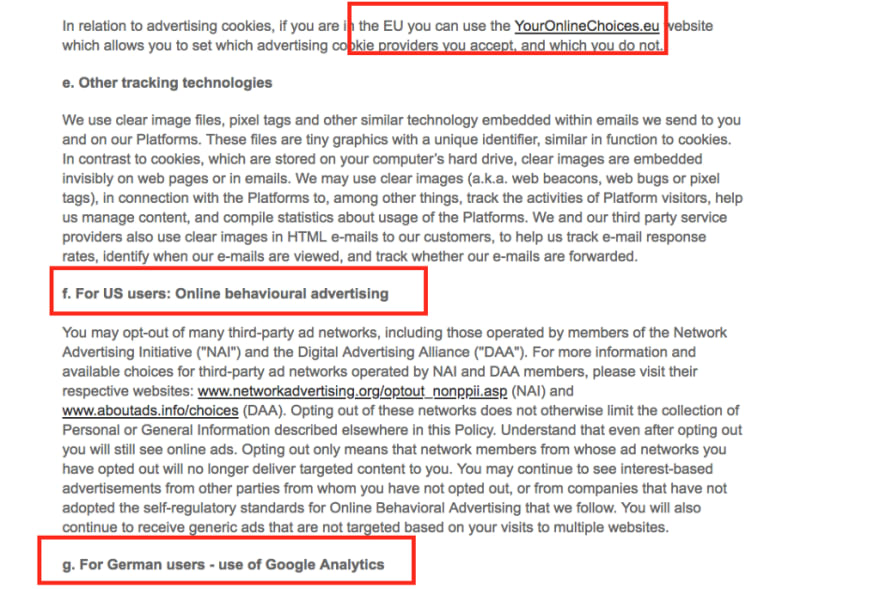
Opt-out options available only mentions ways using about cookies, YourOnlineChoices. This means that not only the information provided in Privacy Policy is incomplete but also does not share any options to opt-out of services CrazyEgg, BoxEver, Coremetrics etc. The process is tedious and cumbersome.
The option to opt-out is biased based on the country of residence of the users. If you are a resident of EU you can use this link to opt-out. If you are a resident of USA this is the link to opt-out. But if you are a resident of any other region, I am sorry to break it to you that you have been short-changed.
- Opting-out of cookies is not going to have any impact on the data leaks highlighted in the article because the referrer is not being cleaned. Anybody with basic tech knowledge can confirm this.
In Short
Even if the user somehow manages to opt-out of all the trackers using the methods listed and not listed, Emirates will still leak the Booking Reference and Last Name which is enough to access all other sensitive information because the implementation of these third-party services on Emirates.com is flawed.
Emirates needs to understand that once the information has been shared with third-parties, there is very little they can do to control how it is being used or might be used in the future, as they have themselves mentioned in their privacy policy.
It is one thing for Emirates to think that these issues are not critical enough for them to take necessary actions to fix them. It’s an entirely different thing to say that the information shared in the article is “not true”.
I hope they fix these issues sooner rather than later.
Happy Hacking !
Thanks for reading and sharing ! :)
If you liked this story, feel free to 👏👏👏 a few times (Up to 50 times. Seriously).
Credits: Special thanks to Remi_ ,_ Pallavi for reviewing this post too :)



Top comments (1)
Emirates’ response doesn’t seem to address the real issue—accountability. Transparency in how they handle our data is crucial, but too often living in emirates, it’s all just lip service. Hopefully, more pressure will push for real change.
Some comments may only be visible to logged-in visitors. Sign in to view all comments.