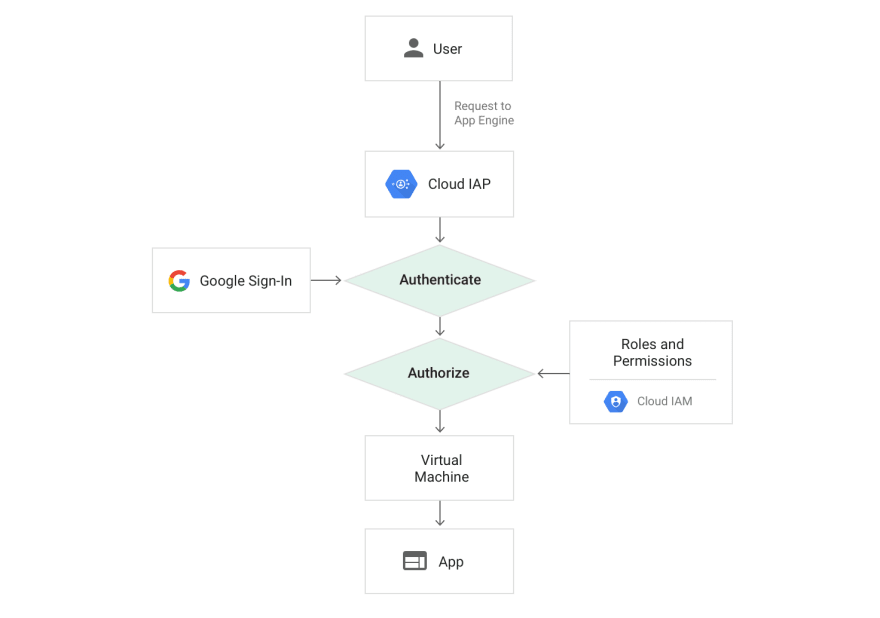
Google's Identity-Aware Proxy is a service that intercepts web requests sent to your application, authenticates the user making the request using the Google Identity Service, and only lets the requests through if they come from a user you authorize.
Using this takes most of the authentication responsibilities away from your application allowing you to make use of a service provided by Google. You can also use it on your on-prem / non-GCP resources using the IAP connector.
How IAPs work 👮🏽♀️
When an application/resource is protected by IAP, only users you have given the correct IAM role will be granted access. After authentication is successful, some information is attached to the headers of the request. X-Goog-Authenticated-User-XXX headers are provided by IAP.
You can use the info gotten from these headers to get useful information that can be used in your application.
What if IAP is turned off mistakenly?
How do I protect my application from Spoofing👨🏽💻?
Answer: Cryptographic Verification 💂🏽♀️
A request header is added by IAP called X-Goog-IAP-JWT-Assertion. The value of the header is a cryptographically signed object that also contains the user identity data.
Your application can verify the digital signature and use the data provided in this object to be certain that it was provided by IAP without alteration.
For an example on how to verify the digital signature check this repo
Knowing all of this, when do you think it is best to use IAP, what is its pitfall, would love to read your opinions in the comment section.
Coming up next is a demo on setting up IAPs on Google Cloud 😉.



Top comments (0)