Preface
Django build in password policy are by itself provide a great basis toward making sure the password that the user choose is relatively strong enough that its hard to guess.
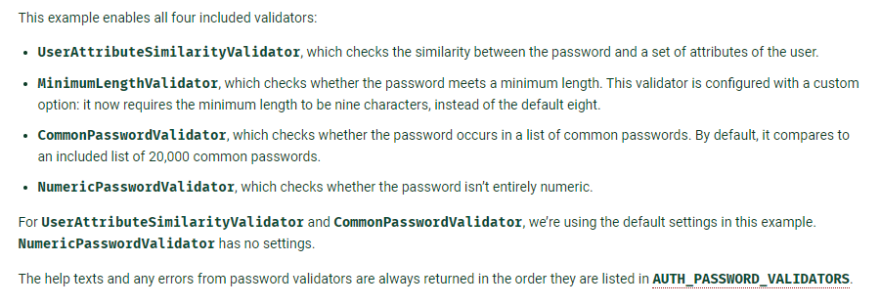
Build in Password Validators
however usually in a business setting, almost all company will have its own set of password policy that need fine grain control of what is acceptable and what is not.
Things like password require 1 uppercase, 1 lowercase, 1 digit, and 1 special character or thing such as no repeated password for the last x number password change require a special kinda of password validator so that we can make it better. My go to password validator would be django-password-validators.
Installing Django Password Validator
Installing django-password-validators with the command:
pipenv install django-password-validators
pipenv lock -r >requirements.txt
Configuring the settings
If you want to have only the password strength check, just use the following in your settings.py file
INSTALLED_APPS = [
...
'django_password_validators',
...
]
AUTH_PASSWORD_VALIDATORS = [
...
{
'NAME': 'django_password_validators.password_character_requirements.password_validation.PasswordCharacterValidator',
'OPTIONS': {
'min_length_digit': 1,
'min_length_alpha': 2,
'min_length_special': 3,
'min_length_lower': 4,
'min_length_upper': 5,
'special_characters': "~!@#$%^&*()_+{}\":;'[]"
}
},
...
]
however if you need validator to check with the historical password
INSTALLED_APPS = [
...
'django_password_validators',
'django_password_validators.password_history',
...
]
AUTH_PASSWORD_VALIDATORS = [
...
{
'NAME': 'django_password_validators.password_history.password_validation.UniquePasswordsValidator',
'OPTIONS': {
# How many recently entered passwords matter.
# Passwords out of range are deleted.
# Default: 0 - All passwords entered by the user. All password hashes are stored.
'last_passwords': 5 # Only the last 5 passwords entered by the user
}
},
...
]
# If you want, you can change the default hasher for the password history.
DPV_DEFAULT_HISTORY_HASHER = 'django_password_validators.password_history.hashers.HistoryHasher'
End
I think with django-password-validators package, we are now able to make sure that the user would atleast have a much harder password to crack.


Top comments (0)