This weekend I took a dive into 0x00Sec's new bi-monthly CTF.
Note::: NO, I won't be posting the found flag{}, but I will be posting the methods I used.
- CTF Name: Exercise #5
- Resource: 0x00SEC
- Difficulty: Easy
- Number of Flags: 1
Flag1
- Hint:
- You might need to get creative with this one :) Think like a pentester!
- Note in the Source Code of
<!-- TODO: -->
<!-- * Stop relying on Base64! I'm sorry... -->
<!-- * Note to Nick: I added backup pass in /etc/passwd <3 -->
- Acquired By:
- Step 1: Is to see the hint in the code and look at it. As I am here I notice that are a few hidden fields in the form and one has some Base64 encoding.
 If we decode it we get a website/ip address. The IP address is the same IP address of the hidden field above it.
If we decode it we get a website/ip address. The IP address is the same IP address of the hidden field above it. 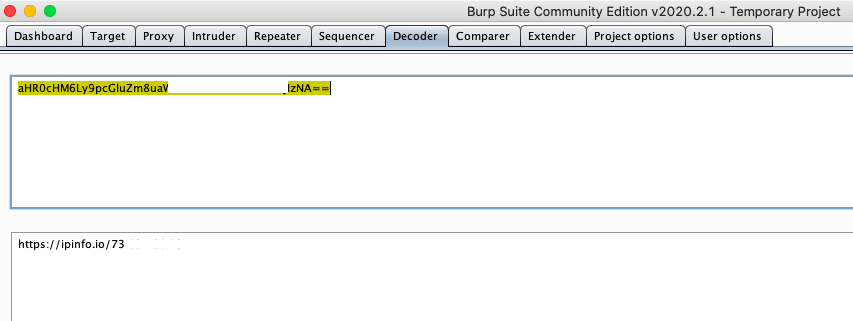
- Step 2: Second thing is so see where this goes. If we look at the site it is an IP look up site and that is my IP and location.... hmmm cool?
- Step 3 is to just click the "login" button and it produces the information on the screen as data. Nothing special.

- Step 4: is that I want to modify these fields and see if anything changes when I click the button.

- Step 4.1: First thing is to change the top field and then delete the parameter in ZAP Request Editor and see if the second link still works. It does nothing and the same information is produced, mine.
- Step 4.2: Second thing is to modify the second fields IP and see if anything changes. I used the PentesterLab IP as I am also working on some labs there and if we replace the IP in the request and base64 and URL encode as "p=aHR0cHM6Ly9pcGluZm8uaW8vNTQuMTcyLjI0Mi4xMzA%3D" we get out the informaiton on where the PentesterLab IP is. Interesting..
- Step 5: I want to look at what is running this and what happens if I put is something that is just some quotes or slashes?? For this I will use ZAP again to encode the request and resend it.
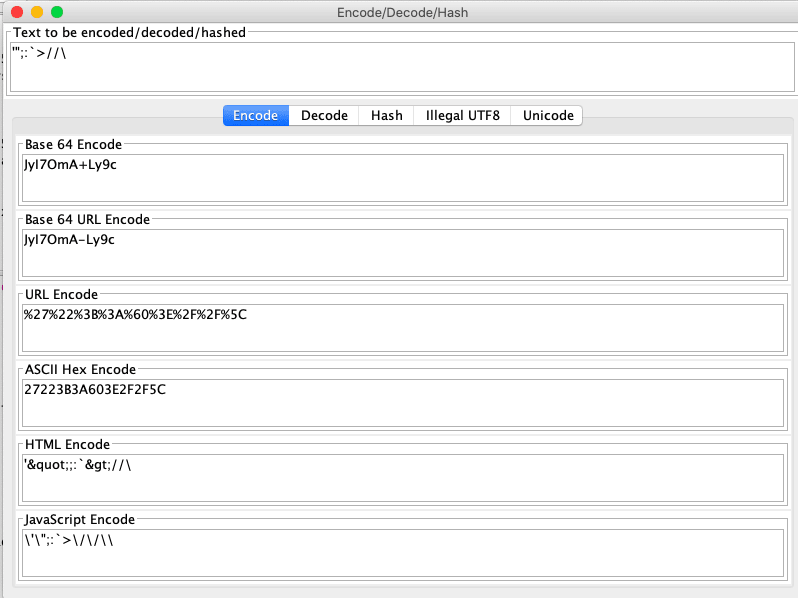 If I send in "p=JyI7OmA-Ly9c" nothing comes back... Is this some file traversal?? Can I get an error??
If I send in "p=JyI7OmA-Ly9c" nothing comes back... Is this some file traversal?? Can I get an error?? - Step 6: For this step I need to do some research on the nginx/1.17.5 server that is running and its file paths because the hint was about a password in the "/etc/passwd" file. The research I did provided info about the structure of file paths in it. This lead me to trying the path of "../../../../../../../../../../../../../etc/passwd" as "p=Li4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA%3D%3D" but this produced nothing... I am missing something.
- Step 7: If we look at how file paths are structured in our own browser we can see that they all start with a "file" word, so we need to build the command around this. For this I need to structure it like "file://etc/passwd" rather than a lot of "../../"s. This exact payload did not work though so this needs to be tweaked a tad. If we go back to the browser and look at our own file paths again we can see that there is an extra / in its path, "file:///", so let's try that. If we change the payload to "p=ZmlsZTovLy9ldGMvcGFzc3dk" and send it in we get the passwd file and the flag.

- Step 1: Is to see the hint in the code and look at it. As I am here I notice that are a few hidden fields in the form and one has some Base64 encoding.
Learned
This CTF taught me about file path traversal and, more importantly, how the browser connects to the nginx server's file system.
If we break this down a bit we can see that we are on a browser that is interacting with a server and we want access to its' file system. 
With this CTF there is an issue with the server and how a file protocol that an http client understands is being handled. Because http clients need protocols we are able to exploit this issue by exploiting the path as the server is processing the request.
See, normally the server would take in the ipinfo.io/ipAddress and pull out the information from the site and display it. But we are able to take advantage of an issues that allows us to add in a file path so that when the server processes the request it is processing it like how a browser would and we are able to access the file path. Interesting right?



Top comments (0)