Containerization since it hit the market has optimized development, scalability of applications, and a ton of other utilities, so much so that it can easily be viewed by development teams as the gift that keeps on giving. Be that as it may, containerization for all its benefits has led to the unintended consequence of creating some application silos. Depending on the scale of your company’s digital operation, this can be a lot to handle even with the help of Docker.
Container security has become a hot topic in the wake of several cybersecurity attacks, notable among which is the cryptojacking attack on Tesla, which was temporarily successful due to their insufficient container security.
Container security involves bulletproofing your deployment environment and resources and inculcating Kubernetes security best practices to secure your Docker, host, and/or cloud deployment resources.
Important Steps For Container Security
Container security isn’t a random “once and done” check you do when you’re about to deploy an application. And it’s not a periodic audit of your deployment environment to check for issues or free up space. Effective container security is policy and real-time container monitoring that leverages software and professional inspection to prevent external threats from slipping through the cracks.
Some of the best practices for container security are basic rule of thumb actions that do not require learning more than you already know. These are the steps we explore in this article.
It’s an open secret that a lot of organizations do not have a proper handle on how many containers they’re running. For massive corporations that are slowly transitioning into microservices architecture, you will have a mix of containers and monolithic applications to handle. It’s very important to know the location of all containers as well as their responsibilities in order to speed up monitoring and managing your container security.
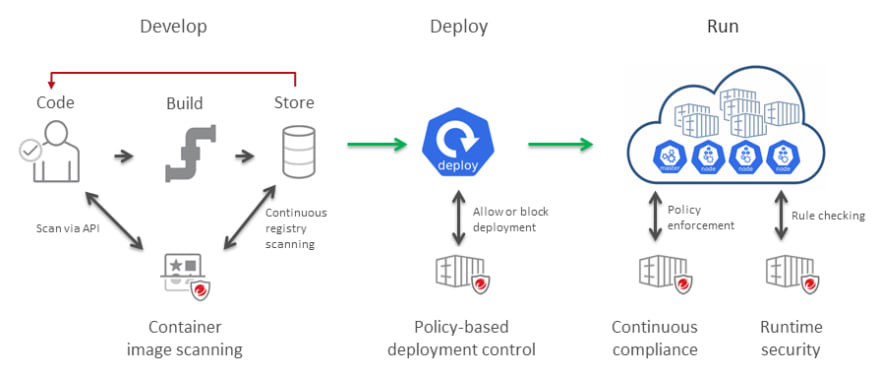
Creating a Deployment Control Policy
During pre-deployment processes, it’s important to develop policy-based deployment control rules that will be implemented in your deployment environment. By infusing your rules into your Kubernetes object’s properties, you make it easier for other tools that evaluate your deployment control to determine if your image is ready for deployment or if it needs a second look. Little things like this can have a snowball effect if things go wrong. This is why it’s best to err on the side of caution.
Container Image Scanning
Starting with deployment, container image scanning has to rank as the first thing you need to do regardless of whether you’re deploying to a new operating system or one that already hosts other applications. Image scanning helps reduce the likelihood of deploying applications that are corrupted directly or are compromised as a result of the packages and other dependencies that they’ve been bundled with.
VPNs and MFA
While a lot of best practices dictate that you foolproof your containers against external threats, sometimes internal threats can be more damaging. The use of a VPN (virtual private network) and MFA (multi-factor authentication) for employees who have administrative access to your containers can reduce the likelihood of their user accounts falling into the wrong hands and being used maliciously. This measure is especially important now that working remotely has become the norm.
Using the Right OS
When deciding on operating systems for your containers, it’s best to leverage the OS that best aligns with the nature of your container. Reducing the amount of unnecessary packages and resources in an environment will directly reduce the number or possible loopholes that can be exploited. The rule of thumb is that if your container doesn’t interact with a dependency resource, the resource shouldn’t be in your OS. The rise in infected packages justifies the need to trim the excess in your OS.
Container Management
There are times when it’s easy to forget why a microservice architecture is revolutionary when building applications. Knowing when to make a component of your application into a separate service can sometimes be challenging. A mistake at this point of development can result in a container that does too many things and needs to constantly be modified.
Containers must remain lightweight and focused on specific responsibilities in order to reduce the number of modifications needed on it. This in turn reduces the likelihood of compromising the container security by mistakenly introducing resources that compromise the container.
Continuous Monitoring
Deploying your application and having your containers running without any challenges doesn’t exactly mean it’s ok to kick back and relax, it’s important that you continuously monitor your environment and containers as cybersecurity threats can spring out of nowhere. Moreover, by virtue of the fact that your applications interact with the internet and with users who have different motives, frequent inspections are needed to confirm that things are the way they should be or resolve anomalies in your container.
The use of monitoring tools can’t be overemphasized in container security. Procurement of container security tools can provide round-the-clock security for your containers and react faster to threats as they appear. Because the human ability to actively juggle multiple pieces of information is relatively finite, it’s more pragmatic to saddle container security tools with the bulk of the responsibility of enforcing policies and checking container images during and after deployment.
Conclusion
As the world pivots more applications from the monolithic architecture to microservice architecture, it’s important that cybersecurity is enforced not just in the application, but in the environment that helps the application interact with the broader internet. Protecting your digital infrastructure for the benefit of your clients and your organization must also include container security in order to guarantee holistic immunity to the attackers of hackers and other malignant actors.
There are tools that make the process of securing containers less tedious and it can be really handy to leverage them where necessary, depending on the size of your team and your budget.



Top comments (1)
This was a great read. Thank you for sharing.